A friend of mine is nearing retirement and thinking about spending some extended time living and working abroad. He has a few years to plan how to manage this transition, and asked for my advice. Here are a few recommendations on gear, process, and managing his security. In the past year I have been to London, Prague and Israel, so I have some ideas. I also asked some long-time fellow vagabonds to help provide some guidance based on their own experiences.
 Your phone. At the heart of your communications is going to be your smartphone. My recommendation is to have at least one country-based SIM card when you travel, which is what I do when I am abroad. The issue is that some countries can recognize others’ cards, and some can’t. If you have a European cell plan, you can easily roam around the entire continent. For those of us from the States, we can use the GiffGaff SIM — it works really well there and it is very inexpensive. Another recommendation is to limit your use of voice minutes, and get the biggest data plan that you can afford for the period of time that you will be traveling. If you are going to be someplace for a month or longer, you should consider buying the SIM when you arrive, as you often can get the best deals at a local drugstore or supermarket.
Your phone. At the heart of your communications is going to be your smartphone. My recommendation is to have at least one country-based SIM card when you travel, which is what I do when I am abroad. The issue is that some countries can recognize others’ cards, and some can’t. If you have a European cell plan, you can easily roam around the entire continent. For those of us from the States, we can use the GiffGaff SIM — it works really well there and it is very inexpensive. Another recommendation is to limit your use of voice minutes, and get the biggest data plan that you can afford for the period of time that you will be traveling. If you are going to be someplace for a month or longer, you should consider buying the SIM when you arrive, as you often can get the best deals at a local drugstore or supermarket.
The issue is whether to have an Android or an Apple one. I am biased towards Apple. Do you need to buy the latest and greatest iPhone model? No, and lately the American cellular carriers are offering all sorts of discounted (and sometimes free) phones if you agree to a two year contract on an older iPhone, such as the iPhone 8. One issue with using different SIMs on an iPhone is that it can mess up iMessage and deregister your American phone number from your iCloud account. A way to avoid this is to start originating your iMessages from your iCloud account instead of from your phone number.
If you are an Android fan, I would stick with Samsung, because they have updated their phones’ security software. Avoid other Androids, because they are so easily compromised: all it takes is downloading a phony app, or clicking on a phished email. You might say that you will pay careful attention and not download anything, but it is just human nature.
What about getting a dual SIM card phone such as the iPhone XR or Samsung Galaxy S10? I don’t think this feature is worth it, especially as these tend to be the more pricey phones. They also don’t really have two physical SIM sockets, so you will have to make use of a virtual or eSIM, which adds another layer of complexity and compatibility. Many non-US carriers offer free inbound calling from US numbers anyway.
Your American cell provider. Reading articles about SIM attacks such as this one on c|net, I think the best US carrier for secure international use is T-Mobile. It also has a very flexible travel plan. This doesn’t mean that it works everywhere, and you should map your planned route with its coverage area, otherwise you will run up a nasty roaming bill in those unsupported places.
You should definitely add a wireless PIN to your online cellular account. Depending on how long you will be out of the USA, you might be able to get by without having any American cellular account. Given that there are so many data-based voice apps (WhatsApp, Skype, Viber, Facetime), you probably can limit your actual voice calls anyway. For example, WhatsApp seems to be the app of choice that many AirBnB owners use to get in touch with you, and in Israel it is really the main communications tool among locals.
Google Fi also has some interesting plans, especially for international travel, and has expanded their geographic coverage. If they offer service in the countries that you intend to be in, then give them consideration. They also might work better on Android models. One of my friends uses this and finds it very handy: “I can touch down in 170 countries and immediately have data access plus have coverage for when I’m in the States. I cannot stress enough how important it’s been to have data when I land somewhere for both safety and convenience. When I’m able to respond to messages at touchdown and get an Uber from the airport without needing to hope there’s Wifi it’s been a genuine lifesaver.” That reminds me when I was in London for a few days and just had Wifi coverage: I had to run back and forth between the terminal and the car park and almost missed my ride because the garage had no coverage.
One other recommendation for navigation is the mobile app Maps.me. You can easily prepare digital maps and download them to your phone in situations where you don’t have decent data coverage. One downside is that the maps are in their native language.
Your American banking provider. If you take a look at the twofactorauth site, you can see that Capital One, HSBC and USAA all support phone authentication apps. There may be others — my friend pointed out that his local credit union also now supports the Google Authenticator app. Now I know that changing banking providers is painful, but if you are planning this in advance you might as well start now and choose one of them that supports one of the auth apps. Also, if you haven’t gotten a Yubikey or a Google Titan key, you might want to purchase one of these as well.
While supporting the local credit union has some appeal, you want a bank that has a larger footprint, and is able to make deposits and withdrawals from overseas ATMs with minimum fees. If you are going to be sticking around in one place for several months, you might want to open up a local account, and then consult the twofactorauth website to see if there is a bank that offers additional authentication support.
Speaking of other accounts, I have been experimenting with the mobile app Revolut. It makes it easy and inexpensive to move money around the world. You can use the app to find low-fee ATMs and hold funds in multiple currencies.
What other accounts do you have that handle money transactions? Amazon, for example, is an obvious one. But you might have set up accounts for bitcoins that you have forgotten about, or other online merchants that you do business with. You should use this time to flag them and if they don’t have an authentication app option, delete them. I had set up a Yahoo.com email account back in the early days, and had about 100 contacts on this account. When Yahoo got breached, that account was compromised. I had forgotten about this account and its contents. It didn’t help matters that Yahoo made it difficult to completely delete it too.
Harden all of your passwords. If you don’t use a password manager, now is the time to get on board with one of them and start changing your passwords to something more complex, and of course unique. Watch yourself and take note when you create a new online account and let the password manager take over – rather than typing in one of your old standbys. I use Lastpass, but there are others that are just as good. Should you be concerned about storing your entire password collection in the cloud? Yes, but the better password managers also use authentication apps to secure your master password, so make sure you use this option. BTW, you should not store your passwords in any of your browsers. This is because if you cross an international border, you might have to unlock your phone at the checkpoint. This also means that you should sign out of all your email and other sensitive accounts when you reach a customs barrier, especially when entering and leaving the USA.
What online accounts use your present cell phone number as part of your identity? This is a lot harder to figure out, even with your password manager. Facebook and Twitter are the biggest issues here. I don’t think you can easily change your cell attached to your account, but if you can you should set up Google Voice as a phone number for use just in authentications. It will forward both voice and texts to your “regular” cellular number too. One issue: you can’t use both Google Voice and Google Fi on the same account.
Laptop physical security. I got a “disposable” – meaning cheap – laptop so I don’t have to worry about it being stolen when I travel. But when you are living somewhere else, you might have to rethink this. How can you travel with your data without worrying that something will happen to your laptop if it is all on your computer? I have heard that thieves in Silicon Valley are going around with Bluetooth scanners looking for laptops in cars. It is only a matter of time before this catches on elsewhere. This means you might want to consider either a laptop with a removable hard drive, or else keep everything in the cloud with a Chromebook.
How about a VPN? I use ProtonVPN, made by the same folks that do ProtonMail. The basic free version is fine. One issue, though: when transiting some airports and staying at some hotels, you have to turn it off in order to connect to the venue’s WiFi hotspot web portals. The nice thing about this VPN is that you can use it on both your phone and laptop. The paid versions have fancier features, such as being able to pick an originating network.
Thanks to Paul, Bryan and Joel for their help with this article. Feel free to share your own digital nomadic experiences in the comments here. And good luck with your travels!
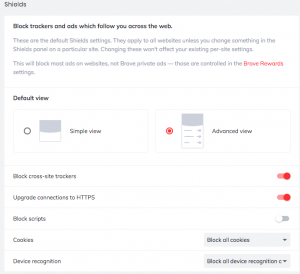 If you aren’t familiar with Brave, it is built on the same Chromium engine that Google uses for its browser, but it does have a more logical grouping of privacy settings that can be found under a “Shields” tab as you can see in this screenshot. It also comes with several extensions for an Ethereum wallet and support for Chromecast and Tor. This is why Brave is marketed as a privacy-enhanced browser.
If you aren’t familiar with Brave, it is built on the same Chromium engine that Google uses for its browser, but it does have a more logical grouping of privacy settings that can be found under a “Shields” tab as you can see in this screenshot. It also comes with several extensions for an Ethereum wallet and support for Chromecast and Tor. This is why Brave is marketed as a privacy-enhanced browser.








