As many of you know, for the last several years I have been doing a regular podcast with Paul Gillin on B2B marketing trends. Gillin has been in tech journalism for more than 30 years, having run Computerworld and TechTarget and written numerous books. It is a fun gig, and we offer a lot of insight, and you should subscribe if you are interested in the overall topic.
In our latest episode, we return to talking to Dan Newman, who is a very insightful guy for just being born when both Paul and I started in IT. Newman said one thing that I want to expand upon here. We were talking about the rise of customer self-service portals and methods, including using chatbots as a tool to provide quick answers. He thinks this is an indication that “We have become more social, but only behind our keyboards.” That is an interesting phenomenon.
I would amend that position to say not only have we become more social, but more critical to a fault thanks to our consumption of online social networks. You could lay the blame on Reddit, as this recent book does. (We are the Nerds, as reviewed in the NY Times here.) A better title for this book, as the reviewer David Streitfeld states, should be “We are the Trolls” and suggests its tag line should be “Two inexperienced young guys created something they didn’t understand and couldn’t control.” He writes, “the lack of adult oversight; the suck-up press; the growth-at-any-cost mentality; the loyal employees, by turns abused and abusive” all contributed to its offensive snark. In the end, it didn’t matter. Forget about connecting the world, or doing good, or bringing a voice to the disenfranchised. Reddit is a $2B media property, and in the Valley, money is what eventually matters.
 That is a common theme for many tech companies, and it seems we are seeing the same effect happening down highway 101 at the Facebook campus (shown here). You should watch the two-part Frontline series this week about Facebook. During the program, you will see how in the process of connecting the world’s populace, it has inflamed their worst passions and stoked their fears. It interviews several current and ex-employees. While the latter might have axes to grind, it is worth hearing their points of view. You’ll hear how Trump’s digital media manager spent $100M on Facebook ads before the 2016 election. If you haven’t thought about this before, it is worth viewing both episodes to see how much influence the company has had, and how poor Zuck’s leadership has been. The program also highlights the rise of “fake news” across Facebook, such as these companion posts on the Pope endorsing either Trump or endorsing Clinton.
That is a common theme for many tech companies, and it seems we are seeing the same effect happening down highway 101 at the Facebook campus (shown here). You should watch the two-part Frontline series this week about Facebook. During the program, you will see how in the process of connecting the world’s populace, it has inflamed their worst passions and stoked their fears. It interviews several current and ex-employees. While the latter might have axes to grind, it is worth hearing their points of view. You’ll hear how Trump’s digital media manager spent $100M on Facebook ads before the 2016 election. If you haven’t thought about this before, it is worth viewing both episodes to see how much influence the company has had, and how poor Zuck’s leadership has been. The program also highlights the rise of “fake news” across Facebook, such as these companion posts on the Pope endorsing either Trump or endorsing Clinton.
Think fake news is easy to spot? Take this quick quiz developed by the Newseum education staff. My wife and I tried it, and while we did reasonably well, we still got a couple of items wrong. Granted, we had a timed deadline to complete the quiz, and some of them we just guessed answers. But we saw that it is harder than we both thought, even when you have been told to be on the lookout. Imagine how much harder this task could be in our normal lives consuming online media posts?
The Frontline program interviewed their chief of security Alex Stamos who says, “Russia [through its advertising and fake accounts] wants to find fault lines in US society and amplify them, and to make Americans not trust each other.” Russians orchestrated two concurrent and co-located protest rallies in Houston, seeding participants on both sides. There is no question that Facebook is being used as an amplifier to promote hatred of all kinds. Just look at your own news feeds.
Farhad Manjoo’s column in the NY Times this week makes a case that Zuck is “too big to fail,” playing off the phrase used for the 2008 mortgage banking crisis. He mentions reports that tie Facebook posts to the Myanmar genocide, discriminatory advertising and multiple federal legal inquiries. He concludes by saying either Zuck fix Facebook, or no one does, like it or not.
But here’s the thing: as we become more social behind our keyboards, we can’t be as discriminating as we can when we meet people face-to-face. In embracing the self-service world, we are all doing ourselves a tremendous disservice too. Lies become truth, and democracy is turned inside out. It is time Facebook took responsibility for its power and role in this process.
 Paul Gillin and I speak this week with
Paul Gillin and I speak this week with 


 Driven and imaginative leadership.
Driven and imaginative leadership. Application security is the process of making apps more secure by finding, fixing, and enhancing the security of apps. Much of this happens during the development phase, but it includes tools and methods to protect apps once they are deployed. This is becoming more important as hackers increasingly target applications with their attacks.
Application security is the process of making apps more secure by finding, fixing, and enhancing the security of apps. Much of this happens during the development phase, but it includes tools and methods to protect apps once they are deployed. This is becoming more important as hackers increasingly target applications with their attacks.
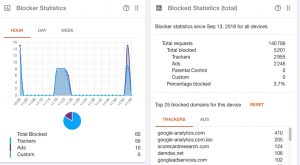

 This has been quite a year for data breaches, with reports that numerous unsecured Amazon Web Services storage containers were inadvertently made public, a rise in hidden cryptomining malware, and lots of victims continuing to fall for ransomware and other botnet attacks. So, with that context, let’s look at what security trends 2019 could bring and ways to prepare for the coming year. I cover security awareness training, hiding malware in plain sight with fileless and other techniques, the rise of FIDO2 and better cloud security in
This has been quite a year for data breaches, with reports that numerous unsecured Amazon Web Services storage containers were inadvertently made public, a rise in hidden cryptomining malware, and lots of victims continuing to fall for ransomware and other botnet attacks. So, with that context, let’s look at what security trends 2019 could bring and ways to prepare for the coming year. I cover security awareness training, hiding malware in plain sight with fileless and other techniques, the rise of FIDO2 and better cloud security in  One of the best takeaways I got from
One of the best takeaways I got from