Keeping track of your monthly cloud computing bills isn’t easy. While it is great that cloud providers usually charge you on the resources you consume, the various elements of your bill are very complex and made up of dozens of different factors, such as CPU core, storage units, RAM size and data transfers. Fortunately, there are a number of online services (see chart below) that can help you save money by using a series of clever choices. In this article for CIO (email reg. req.), I will look at five questions that you can ask to try to reduce your monthly cloud computing bill.
| Service, link | Number of Cloud Providers | Expertise | Free or paid? |
| Cloudability | AWS | Cost monitoring | Paid |
| Cloudorado Cloud Hosting Comparison | 27 | CPU benchmarks | Free (paid by participating vendors) |
| Cloudyn | AWS, Azure, Google | Costing trends | Both |
| CloudHarmony CloudSquare | 101 | Uptime status | Free |
| CloudSpectator | Varies | Custom analytics | Both; paid reports are $400 each |
| CloudHealth Technologies | AWS, Google | Costing, performance and security analytics | Paid services start at $250/mo |
| Datapipe Analytics | AWS, Azure | Management tools | Paid services start at $3500/mo |
| RightScale PlanForCloud | 6 | Deployment scenarios | Both; paid services start at $6000/mo |
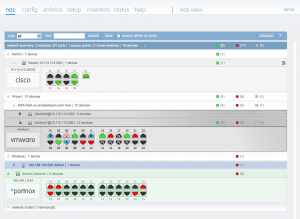
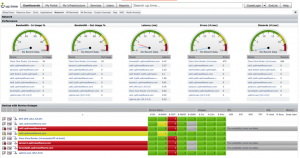
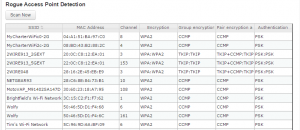 Overall, the market has slowly evolved more than had any big revolutionary changes. Products are getting better in terms of features and price/performance. All six of these units will do fine for securing small offices of 25 people.
Overall, the market has slowly evolved more than had any big revolutionary changes. Products are getting better in terms of features and price/performance. All six of these units will do fine for securing small offices of 25 people.