 Properly testing your virtual infrastructure has been an issue almost since there were virtual VMs and AWS. Lately, the tool sets have gotten better. Part of the problem is that to adequately test your AWS installation, you need to know a lot about how it is constructed. CPUs can come and go, and storage blocks are created and destroyed in a blink of an eye. And as the number of AWS S3 data leaks rises, there have to better ways to protect things. Rhino Security and Amazon both offer tools to improve visibility into your AWS cloud environments, making it easier to find configuration errors and vulnerabilities.I write about Pacu and CloudGoat tools as well as various AWS services to test your VMs in my article from CSOonline here.
Properly testing your virtual infrastructure has been an issue almost since there were virtual VMs and AWS. Lately, the tool sets have gotten better. Part of the problem is that to adequately test your AWS installation, you need to know a lot about how it is constructed. CPUs can come and go, and storage blocks are created and destroyed in a blink of an eye. And as the number of AWS S3 data leaks rises, there have to better ways to protect things. Rhino Security and Amazon both offer tools to improve visibility into your AWS cloud environments, making it easier to find configuration errors and vulnerabilities.I write about Pacu and CloudGoat tools as well as various AWS services to test your VMs in my article from CSOonline here.
Category Archives: virtualization
The best tools to predict and manage cloud computing costs
 Cloud pricing can be a frustrating experience. Everything is charged by different metrics. Some of the prices are spelled out, some are hidden behind paywalls or aren’t clear until you get your monthly bill and realize you forgot to turn off an instance that is chewing up your wallet. Some are charged by usage, others by the month.
Cloud pricing can be a frustrating experience. Everything is charged by different metrics. Some of the prices are spelled out, some are hidden behind paywalls or aren’t clear until you get your monthly bill and realize you forgot to turn off an instance that is chewing up your wallet. Some are charged by usage, others by the month.
I look at some of the issues in keeping track of your cloud costs and summarize the numerous services that are currently available. You can read my post on WindowsITpro here.
SecurityIntelligence.com: Security Solutions for the Virtual Network
 I cover a recent white paper from the Cloud Security Alliance about network function virtualization (NFV) in a series of posts for IBM’s SecurityIntelligence.com blog. In the first post, “Security and the Virtual Network: Part I,” I discuss how NFV and software-defined networks (SDNs) are changing the traditional enterprise infrastructure. Part two explored some security challenges and implementation risks involved with deploying new virtual networks and their related technologies. And in the third post, I recommend improvements and certain security frameworks for protecting your virtual networks.
I cover a recent white paper from the Cloud Security Alliance about network function virtualization (NFV) in a series of posts for IBM’s SecurityIntelligence.com blog. In the first post, “Security and the Virtual Network: Part I,” I discuss how NFV and software-defined networks (SDNs) are changing the traditional enterprise infrastructure. Part two explored some security challenges and implementation risks involved with deploying new virtual networks and their related technologies. And in the third post, I recommend improvements and certain security frameworks for protecting your virtual networks.
Virtual networks’ dynamic nature means IT staff have to take time to document its topology and data flows carefully and keep up with any changes to its structure.
Redmond Magazine: Using OpenStack to Control VM Chaos
I join Dell Virtualization Evangelist Hassan Fahimi to provide a complete overview of OpenStack and Foglight for OpenStack, including:
- Understanding OpenStack deployment strategies and issues
- Gaining complete visibility into your OpenStack topology
- Monitoring the performance of specific OpenStack modules and components
- Leveraging alerts to proactively identify issues
- Taking advantage of built-in “FAQs” and reports to immediately get the answers you need
You can download my slides here, and watch the webinar here.
TechTarget seminar: How to make the move to hybrid cloud computing
The benefits of cloud computing have been hammered into IT – streamlined processes, improved accessibility, greater flexibility, and so on – but latent concerns around security, performance, and access have kept many organizations from realizing the true value of the cloud.
You need to objectively compare the capabilities and costs of cloud services against those of traditional on-premises infrastructure – even if you’re already doing some mix of the two (in fact, especially if you’re doing a mix of the two).
This five-city event provides that objective perspective by focusing on building a data center infrastructure that realizes the true value of cloud computing across your IT infrastructure – including automation, high availability, appropriate utilization rates – and not just limited, low-impact use cases. Sign up for one of the cities that I will be speaking here.
SearchSecurity: Virtualization security tools defend across clouds
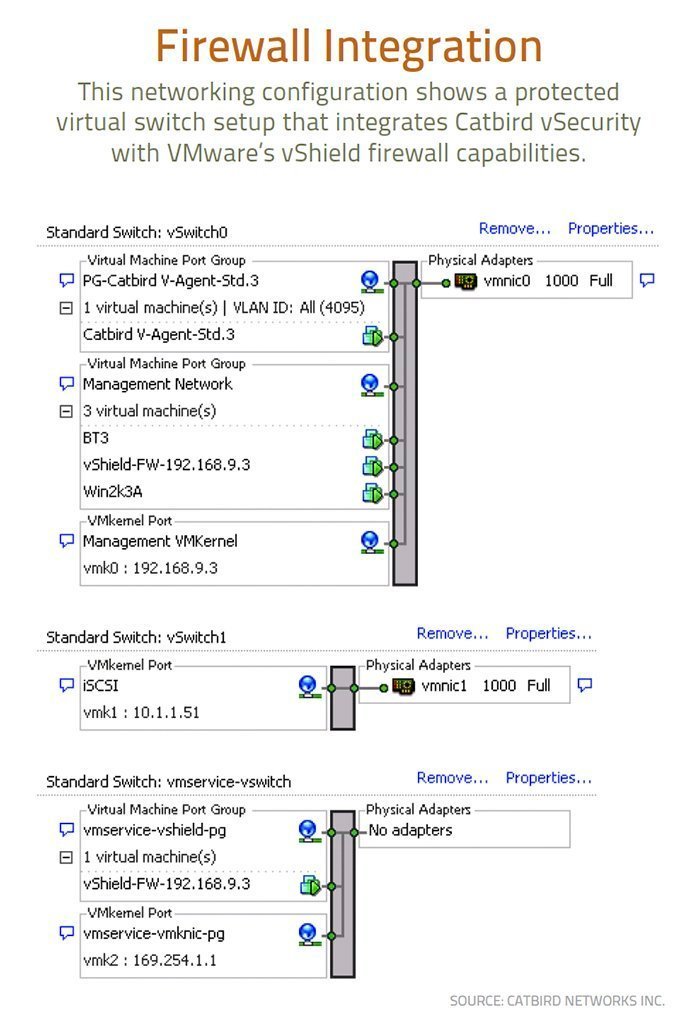 The days when IT managers used different security products to protect their on-premises and cloud infrastructures are happily coming to a close. There’s a growing awareness that migrating virtual workloads to new IT infrastructure requires different levels of protection with security mechanisms built-in.
The days when IT managers used different security products to protect their on-premises and cloud infrastructures are happily coming to a close. There’s a growing awareness that migrating virtual workloads to new IT infrastructure requires different levels of protection with security mechanisms built-in.
In this story for TechTarget’s SearchSecurity, I talk more about this trend and some of the products (such as Catbird’s shown above) that can be used to protect your cloud-based resources.
SearchSecurity.com: Five ways CIOs tackle hybrid cloud security
As CIOs adopt hybrid-cloud strategies, some quickly learn that these environments need new kinds of security models or, at least, contexts in which to apply existing controls and security technologies. Most organizations also find that their environments are not as simple as a pure private plus public cloud. Legacy on-premises systems and SaaS applications come into play.
ITworld: A get-up-to-speed guide on hyper-converged infrastructure
The market for hyper-converged systems is quickly evolving. Traditional storage infrastructure vendors remain the largest installed base, but software-defined and hyper-converged storage providers represent the fastest growing market segment, with some of the latter vendors rapidly increasing their market share.
This get-up-to-speed guide posted here will help you navigate the hyper-converged infrastructure options.
ITworld: A get-up-to-speed guide on VDI
Virtual desktop infrastructure, better known as VDI, is undergoing a new life. A few years ago, it was plagued by lackluster user experiences and cost overruns. Now, thanks to an injection of new technology and better implementations, there’s a lot to like. Faster, cheaper technology has made it an interesting option for companies seeking a way to support flexible, work-from-anywhere environments.
How does this transformation happen? This get-up-to-speed guide posted on ITworld explores how VDI can help organizations navigate shifts in business, and user needs.
ITworld: A get-up-to-speed guide on moving legacy apps to the cloud
Making a case for moving legacy apps to the cloud is becoming easier, with the biggest driver being the ability to shift costs from capital to operating expenses, which can save money. Also, renting capacity rather than owning servers and network infrastructure allows more flexibility in how computing resources are provisioned, enabling workloads to be matched to demand. Quick provisioning is key: New servers can be brought up in the cloud in just minutes, not only making it easier to improve availability but also enabling more flexible disaster recovery mechanisms.
This get-up-to-speed guide explores the key approaches to migrating legacy apps to the cloud, and the value each can bring to your business. You can download my guide here.