Normally, these essays are a lot less personal, where I write about something tech-related. Today I want to talk about myself. Actually, my hearing.
You see, I was born deaf in my left ear. I didn’t realize it for several years, until one day I happened to pick up a ringing phone in my left hand while I was eating something in my right hand. I didn’t hear anyone. Back in those days, they didn’t test kids for hearing until later on.
Being monaural meant I have never heard stereo, have difficulty locating the direction of sounds, and it is tough when I am in noisy places. My wife has so gotten used to being on my right side that when she is with her friends she tends to migrate to that position too.
But my deafness isn’t all that debilitating. At least not until 20 years ago, when I started getting these random dizzy spells. They would happen seemingly at random: sometimes when I was just sitting in my kitchen in the early morning, reading the paper. Once I got one when I on a flight – that wasn’t fun, but fortunately I could lie down across a row of seats and just hope it would be over quickly.
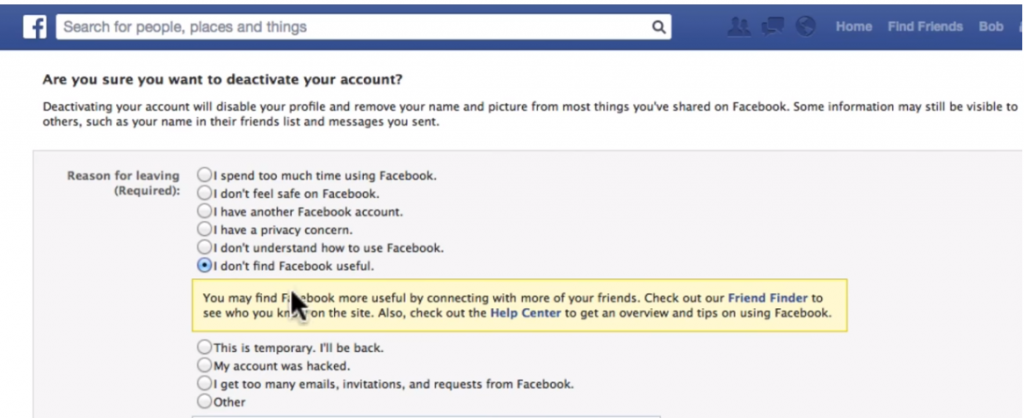
 Eventually, I was diagnosed with Meniere’s Disease, which has no known cure and no simple cause. As you can see from the above diagram, your ear is a very complex organ, with a lot of moving parts. Some folks have it worse, with daily dizzy spells that severely limit what they can do. Mine were relatively minor. To try to fix things, I went through dietary changes, saw a lot of different doctors, gave up driving for a while. And then the dizziness went away.
Eventually, I was diagnosed with Meniere’s Disease, which has no known cure and no simple cause. As you can see from the above diagram, your ear is a very complex organ, with a lot of moving parts. Some folks have it worse, with daily dizzy spells that severely limit what they can do. Mine were relatively minor. To try to fix things, I went through dietary changes, saw a lot of different doctors, gave up driving for a while. And then the dizziness went away.
However, it was replaced by something less onerous but equally vexing: Tinnitus. A constant ringing in my one working ear. Sometimes the ringing would be more noticeable at certain times than others. Lack of sleep, added stress, too much alcohol or caffeine: all of these would make the ringing noise worse. I can hear the ringing right now as I write this.
One of the interesting aspects of Tinnitus is that it comes in various shapes and sizes. People hear different sounds and at different modulations and frequencies. For some patients, it can be just as debilitating as my original Meniere’s. For others, like me, it is just mild enough to be annoying.
Over the years, I have learned to deal with it. Sometimes I would hold a pity party for myself, sometimes the ringing was more than annoying, especially when I was in crowded noisy rooms or restaurants. I remember one time I was at a professional conference of about 300 people. For dinner, we were seated at very long tables in a cavernous room and the noise was literally deafening. I quickly ate my meal and literally ran back to my room, in pain from the noise. I know it looked odd to my dinner companions.
For the most part I accepted the ringing and figured it was better that being dizzy and having the whole world spin around me. But it wasn’t until this summer when I went to a medical conference on Tinnitus that I realized what I hadn’t yet accomplished was actually owning my disease, and facing it head-on. Or ear-on, as it were.
What does owning mean? It means that you control it, rather than it controlling you. You aren’t defined by your Tinnitus, you aren’t at its mercy, and you manage your own treatment and your own response to the disease. The noise you and I hear may be all in our heads, but we have to use our brains to figure out a way to cope and live our lives. For some reason I didn’t really understand what owning my Tinnitus meant until I was sitting in that medical conference, listening to the various presentations. Then it all clicked, so to speak.
As patients, we tend to interact with the medical/industrial complex at the moment when we have a problem: we break a bone, we want it fixed. We have an infection, we want to get rid of it by taking medicine or getting surgery. But the single point of contact with our doctors method doesn’t work with a chronic condition such as Tinnitus (or Meniere’s or whatever). That is because research is ongoing: new drugs, new procedures, new devices, and so forth. We aren’t watching the medical literature like our doctors are doing, because we are busy living our lives. And even if we are willing to put the time into doing Internet research, we aren’t going to medical conferences and learning about many of the latest technologies and techniques that don’t reach the general public for several years.
So I came away from the Tinnitus conference with newfound conviction, and one of the first things that I wanted to do is to get fitted for a hearing aid. The process is relatively simple to explain: you sit in a sound proof booth and listen carefully as the audiologist plays various sounds to test your hearing. But like many medical solutions, the devil is in the implementation details. And as patients, we have to learn a lot before we can figure out the best course of treatment. I found I had some slight high-frequency hearing loss, which is pretty typical for someone my age. So while my hearing is “fine” I could benefit from an aid.
Here’s the thing. When you don’t hear across all the frequencies you are supposed to, your brain doesn’t get to process those sounds, and it is likely that your hearing will only deteriorate as you get older. You go to the gym to maintain and build muscle tone. You need the sonic equivalent of that to maintain your hearing “muscles.”
Before I got an aid I also had to conquer the “old man” stereotype about wearing one. My dad resisted getting an aid for a long time, and by the time he got one it was too late to do much help. But the modern aids aren’t that noticeable, and if I had long hair they would be almost invisible. This is because they separate the battery compartment and the sound processor (which sits behind your ear) from the speaker, which goes inside your ear canal. The two are connected by a very thin wire.
Then I had to decide which problem I wanted to fix more: Did I want a hearing aid that would simulate stereo by placing a microphone in my deaf ear and transmitting the sound to my hearing ear? Did I want an aid to give me more high frequency amplification? Did I want an aid to try to counteract my Tinnitus? Turns out I couldn’t have all three in a single aid.
To fix the deaf ear, there are specialized aids called CROS and BAHA that are available. Years ago I tried the BAHA and I could hear stereo and place the direction of sounds behind me, and it was amazing. But these aids require surgery, and I passed on that opportunity. I tried the CROS aid this time around and didn’t get much benefit from it. So forget that issue: I have lived up until now with a single ear. I decided to look elsewhere, and focus on the latter two issues (Tinnitus and high frequency boost).
At the Tinnitus conference, I got to see what the latest aid technologies were – and being a techy kinda guy, I was somewhat excited. The aids can be used as a Bluetooth headset for your phone. They have all sorts of programmable modes that work with your smartphone. They even come with GPS chips so you can try to track them down if you misplace them. They can help you cook your dinner. Well, not that last item, but almost.
Now, I should know better than to trust the wonderful claims of tech vendors. I found the software lacking: unless I set it up in a certain sequence, the smartphone app (as nifty as it possibly could be) would crash. Hearing the word “Bluetooth,” I immediately thought that the sonic quality of the aid would be close to what an Airpod would be, and it wasn’t even close. Outdoors in a high wind, the aid wasn’t very usable as a phone headset. I am still getting used to having something sitting in my ear canal during most of the day. And the various programmable modes that I can dial into on my phone really don’t have much difference (at least that I can distinguish) on what I can hear from the aid. My audiologist says that my results are typical for many of his patients. Some of the aids have even more buggy smartphone software controls.
However, if I leave these issues aside, I can hear better with my aid, especially those higher-frequency sounds. And the aid does help reduce the ringing tone of my Tinnitus, which was one of the original goals.
I am still learning how to own my Tinnitus, but the hearing aid is a great first step. And here are links to the American Tinnitus Association and the Vestibular Disorders Association, both of which have helped me find other sufferers and great helpful resources to cope.
 Eventually, I was diagnosed with
Eventually, I was diagnosed with 
 4. Avoid endless edit cycles. I have had my stories go through several edit passes, and often after the first one these edits aren’t adding any value to the piece and instead are more political nods to a manager’s whims. While everyone thinks she or he is a great editor, few often have the right skills. It also helps to be clear on who is going to be doing the editing, and who just needs to see the document prior to any final distribution. Sometimes you get stuck in a seemingly endless loop between two editors: one undoes the other’s changes.
4. Avoid endless edit cycles. I have had my stories go through several edit passes, and often after the first one these edits aren’t adding any value to the piece and instead are more political nods to a manager’s whims. While everyone thinks she or he is a great editor, few often have the right skills. It also helps to be clear on who is going to be doing the editing, and who just needs to see the document prior to any final distribution. Sometimes you get stuck in a seemingly endless loop between two editors: one undoes the other’s changes. Your first to-do is to download all of your data that Facebook has on you. I wrote about this process earlier (and
Your first to-do is to download all of your data that Facebook has on you. I wrote about this process earlier (and