This piece was written for Sam Whitmore’s MediaSurvey, which is a subscriber-only site. I have reposted it with his permission.
We have come to the end of an era. It is time to retire a professional title that was significant role in my own life, that of the Editor-in-Chief or EIC. It now has little significance for those in online publishing, perhaps because the entire editorial department has collapsed into a single individual. As in, the EIC is also the copy editor, chief illustrator (thanks, clipart), social media promotions manager, and freelance manager. We might as well add the roles of lunchroom monitor and basketball coach too, for all that they matter.
To say that editorial operations have changed from back in the day when I was EIC at Network Computing in the early pre-web 1990s is an understatement. It is a completely different world. Look at some of the magazine mastheads from that era: there are dozens of roles that are historical curiosities now. It is like looking at the Dead Sea Scrolls. “Yes, sonny, back in my day we printed things on dead trees, and put them into the mail. And we walked five miles uphill to school too.” Who uses ordinary mail, and many kids learn online. Is there anything that the Internet can’t do now?
We had a significant editorial staff: some 20 people, some million or so dollars in annual salaries. Oh what fun I had back then. Not everyone wrote for the publication, but all contributed towards creating a solid editorial product every month. Remember art directors? Another job title that is headed for the scrap heap. Since then, I held other EIC titles and have run online publications with varying sized staffs, but never that big and for that much budget. Little did I know that my first EIC job was going to be the best of them.
Today we don’t have that luxury of having an editorial staff. If the EIC still writes their own stuff, they have a pressure to get it posted online within moments of the actual news event: how many posts on the Microsoft/LinkedIn deal did you read Monday morning, barely minutes after the acquisition was announced? You don’t have time to do a copy edit, or even check the facts, before you get something online.
Sure, there are pubs that have huge (by comparison) editorial staffs and probably still have EICs that can lay claim to the title, but they are by far the exception. Look how many publications Techtarget still has: Each one has a miniscule staff, with a lot of shared services. And I mean no disrespect for them; they are just an obvious example. When I was at EETimes back in the mid 2000’s, their print revenue was 10x or 20x their online revenue, and healthy revenue it was. Not so today. No one prints on dead trees anymore. It seems even silly to say so.
Now the current tech publishing model isn’t really about the articles. Instead, it is all about how you can pay the bills with other things: custom publishing and lead generation and conference sales – in other words, with everything but your actual editorial product. Who needs editorial product, anyway? Bring in the copywriters!
When I was last at ReadWrite, I ran a successful editorial effort with several full time editors and numerous freelancers. The company had just been purchased by an online advertising agency called, ironically, Say Media. Their first question: do you intend to still do copywriting for ReadWrite? Ahem, I didn’t realize that the rebel alliance had taken over. Or maybe it was the dark side of the Force, if I want to have the right Star Wars metaphor. Whatever, Say What? I didn’t last long as a “copywriter.”
Regardless of what the job I was doing was called, the problem is those golden words that I have written over the years used to be the crank that turned the cash machine on. It was words that got readers to open the pages, which in turn drove advertisers to plunk down thousands per fullpage ads. Thanks to the web, there are no more printed pages, and ad rates are down. Way down. If you the reader doesn’t click, we the writers don’t get paid.
But the web isn’t only to blame: that just started the process of decline of the EIC. What really killed him or her off was the very nature of the web publication itself has changed. When every article that I write lives or dies based on the clickstream, you are just a Google entry away from obscurity – or fame and becoming a viral meme. Nowadays the time that I spend promoting, tweeting, reposting, commenting, and cajoling and trying to find readers is just as much as the time spent interviewing, testing, researching and writing. Social media is the cart now driving this old workhorse.
So say farewell to the EICs, may they RIP. Soon we will take our place next to buggy whip operators in history. Please take a moment and honor their memory.
 If you use LinkedIn for marketing, you must listen to this interview. LinkedIn consistently ranks as the most effective social network for B2B marketers. What do the best of the best do well? David Karel shares the lessons he’s learned from nearly two years of working with hundreds of B2B marketers as well as using the LinkedIn platform to reach his own customers.
If you use LinkedIn for marketing, you must listen to this interview. LinkedIn consistently ranks as the most effective social network for B2B marketers. What do the best of the best do well? David Karel shares the lessons he’s learned from nearly two years of working with hundreds of B2B marketers as well as using the LinkedIn platform to reach his own customers.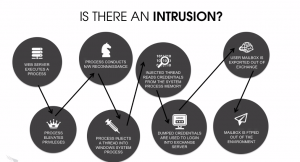

 James Mathewson is a prolific author, digital marketing expert, search engine aficionado and editor-in-chief of IBM.com. Paul Gillin and I recently spent some time with him talking about using data to understand how customers think so that you can align messages to explicitly and implicitly stated needs.
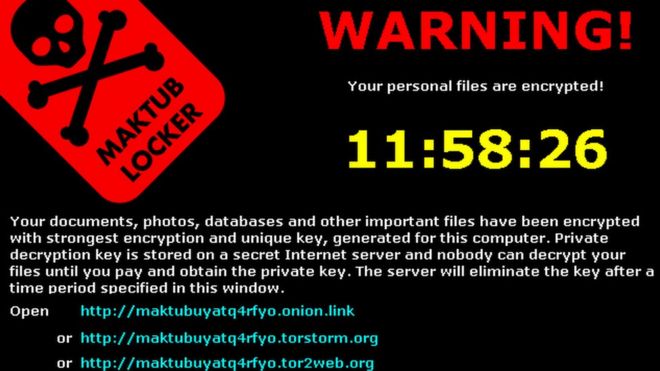
James Mathewson is a prolific author, digital marketing expert, search engine aficionado and editor-in-chief of IBM.com. Paul Gillin and I recently spent some time with him talking about using data to understand how customers think so that you can align messages to explicitly and implicitly stated needs. Detecting virus signatures is so last year. Creating a virus with a unique signature or hash is quite literally child’s play, and most anti-virus products catch just a few percent of the malware that is active these days. You need better tools, called endpoint detection and response (EDR), such as those that integrate with SIEMs, that can recognize errant behavior and remediate endpoints quickly.
Detecting virus signatures is so last year. Creating a virus with a unique signature or hash is quite literally child’s play, and most anti-virus products catch just a few percent of the malware that is active these days. You need better tools, called endpoint detection and response (EDR), such as those that integrate with SIEMs, that can recognize errant behavior and remediate endpoints quickly. With the number of coding for cash contests, popularly called hackathons, exploding, now might be the time that you should consider spending part of your weekend or an evening participating, even if you aren’t a total coder. Indeed, if you are one of the growing number of citizen developers, you might be more valuable to your team than someone who can spew out tons of Ruby or Perl scripts on demand. I spoke to several hackathon participants at the QuickBase EMPOWER user conference last month to get their perspective. You can
With the number of coding for cash contests, popularly called hackathons, exploding, now might be the time that you should consider spending part of your weekend or an evening participating, even if you aren’t a total coder. Indeed, if you are one of the growing number of citizen developers, you might be more valuable to your team than someone who can spew out tons of Ruby or Perl scripts on demand. I spoke to several hackathon participants at the QuickBase EMPOWER user conference last month to get their perspective. You can 