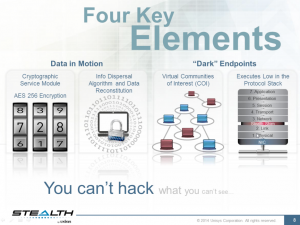
The Internet is a nasty place, and getting nastier. Current breach detection products using traditional anti-malware sandbox technologies can’t keep up with advanced persistent and hyper-evasive threats that pummel enterprise networks on an hourly basis. Malware authors encode their exploits with a number of operational vectors, so in case one entry point doesn’t work they can still find a way into your network to do their dirty work. And as more businesses hire more outsourced consultants, part-time workers, and employ mobile devices, they open up additional mechanisms for malware to enter their corporate networks.
Some traditional AV and endpoint protection vendors have responded to these threats by adding features to their security products to do a better job of anticipating badly behaving packets coming through their detectors. They make use of limited virtual machines or operating system emulators to view how a piece of malware operates. That is great, but it isn’t enough. Many malware authors can detect when these simulated environments are active and can evade detection accordingly. For example, some exploits such as W32.DelfInj can literally go to sleep for several days to avoid any detector that will just scan an infected system for the first several minutes.
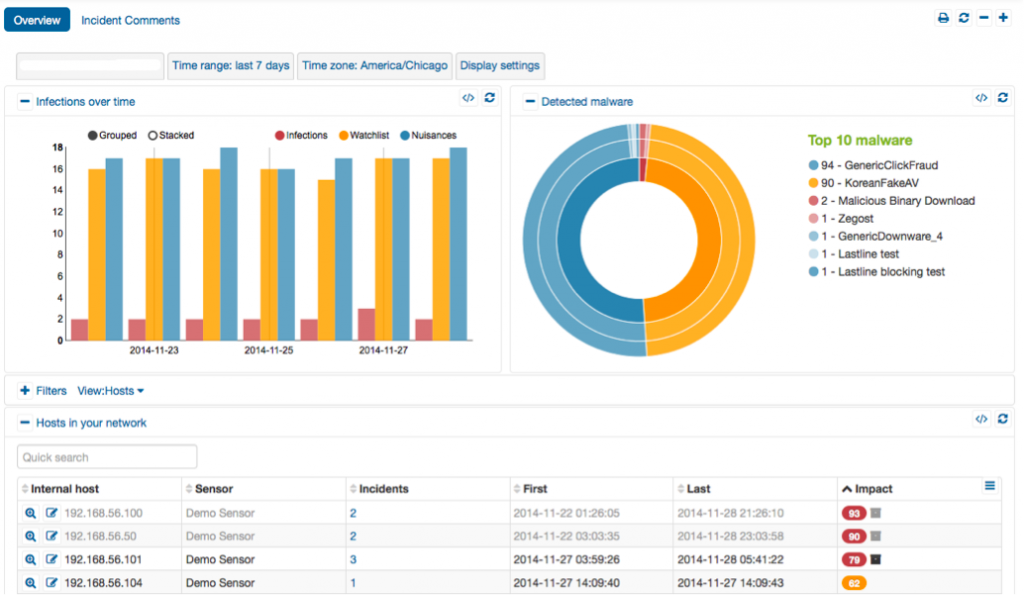 What is needed is a next-generation sandbox that can correlate a series of particular breach events add IP and object based reputation analysis and do this in near real-time. This is what the Lastline Breach Detection Platform does. What makes them unique is their range of discovery, the way they can effectively mimic actual PC or smartphone endpoints to examine malware behavior, and how they can scale up to handle very large networks with their modular and SaaS-based tools.
What is needed is a next-generation sandbox that can correlate a series of particular breach events add IP and object based reputation analysis and do this in near real-time. This is what the Lastline Breach Detection Platform does. What makes them unique is their range of discovery, the way they can effectively mimic actual PC or smartphone endpoints to examine malware behavior, and how they can scale up to handle very large networks with their modular and SaaS-based tools.

 The concept of how we collaborate is changing. Better tools are being developed that help workgroups put together documents, quickly schedule meetings and chat with each other. Today’s collaboration environment includes tools for text chats, bulletin boards, video conferencing, screen sharing and scheduling meetings. Among these are a number of lightweight products that offer quick and near-real time collaboration. I looked at three of the newcomers: Flow, Glip and Slingshot. (A screen from Flow is pictured above.)
The concept of how we collaborate is changing. Better tools are being developed that help workgroups put together documents, quickly schedule meetings and chat with each other. Today’s collaboration environment includes tools for text chats, bulletin boards, video conferencing, screen sharing and scheduling meetings. Among these are a number of lightweight products that offer quick and near-real time collaboration. I looked at three of the newcomers: Flow, Glip and Slingshot. (A screen from Flow is pictured above.)