(updated Feb 2, 2018)
My father’s father emigrated to America from Lithuania about a hundred years ago, and one day I intend to visit the Baltic region and see the land for myself, as my sister and I did earlier this year when we visited my mother’s homeland in northeast Poland. In my mind, the next best thing is to follow the activities of Estonia, a neighboring nation that is doing some interesting things online. (I know, my mind works in strange ways. But bear with me, I needed an intro for this essay.)
One reason why I am interested in Estonia is something that they have had in place for many years called the e-Resident program. Basically, this is an ID card issued by their government, for use by anyone in the world. You don’t have to ever live there, or even want to live there. More people have signed up for this ID than are actual residents of the country, so it was a smart move by their government to widen their virtual talent pool. Once you have this ID, you can register a new business in a matter of minutes. Thousands of businesses have been started by e-Residents, which also helps to bring physical businesses there too. In many countries, offshore businesses are required to have a local director or local address. Not Estonia.
So last week, after thinking more about this, I finally took the e-Resident plunge. It costs about $100, you need to take a picture of your local passport and fill out a simple form. When the ID card is ready, you have to physically go and pick it up at a local Estonia embassy (either NYC or DC would be the closest places for me, I chose NYC). You select your pickup site when you register and can’t change it.
Well, as usual, it was bad timing for me. I should have waited a little bit longer. This week we learned that there are potential exploits with the ID cards, at least the cards that have been circulating for the past several years. Almost 750,000 cards are affected. According to Estonian officials, the risk is a theoretical one and there is no evidence of anyone’s digital identity actually being misused. It might change how the IDs are used in next month’s national elections, although they haven’t decided on that. About a third of their voters do vote online.
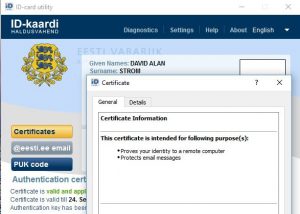 Update: They have issued a fix, which requires you to update the certs that are attached to your ID. So last week (January 2018), I went to their embassy in NYC and got my kit, which includes the ID card, a nifty little USB reader, and some very bare-bones instructions. My first attempt at installing the software on my Windows 10 laptop was met with failure. A second attempt on another Windows PC eventually worked. My biggest complaint is the tech support: an email to one address took several days for a reply, which told me to send it to another email address (in three different languages, no less). The ID card software (shown here) installs four different programs on your computer, each with somewhat similar names. The cert update process requires your full attention and a solid Internet connection: lacking either, and you will have to re-run it.
Update: They have issued a fix, which requires you to update the certs that are attached to your ID. So last week (January 2018), I went to their embassy in NYC and got my kit, which includes the ID card, a nifty little USB reader, and some very bare-bones instructions. My first attempt at installing the software on my Windows 10 laptop was met with failure. A second attempt on another Windows PC eventually worked. My biggest complaint is the tech support: an email to one address took several days for a reply, which told me to send it to another email address (in three different languages, no less). The ID card software (shown here) installs four different programs on your computer, each with somewhat similar names. The cert update process requires your full attention and a solid Internet connection: lacking either, and you will have to re-run it.
The ID card software is also somewhat finicky. It has a place for you to upload your photo, but that didn’t seem to work. You are assigned an official Estonian email address, which I wanted to try to forward to my actual email account, and instructions were lacking on how to do this.
So overall, I give Estonia a passing grade for e-Resident, but just barely. It is hard to use and still needs some work. If a member of the public isn’t computing savvy, they will have a hard time getting going with the whole process. Navigating the numerous web pages for help is tedious and daunting. If you are thinking about the program, I would recommend waiting until they work out the bugs.
Now back to my earlier blog post for some other background info.
Estonia is leading the world in other digital matters too. Lots of companies have disaster recovery data centers located far from their headquarters, but that is an issue with Estonia, which is small enough that far is a just a few minutes’ drive. So they came up with another plan to make Estonia the first government to build an off-site data center in another country. The government will make backup copies of its critical data infrastructure and store them in Luxembourg if agreements between the two countries are reached. My story in IBM’s Security Intelligence blog goes into more details of what they call their “data embassy.” They have lots of other big digital plans too, such as using 100% digitized textbooks in their education system by the end of the decade and a public sector data exchange facility with Finland they are putting in place for this year.
Earlier this year, I read about a course they offered called “Subversive Leverage and Psychological Defense” to master’s degree students at their Academy of Security Sciences. The students are preparing for positions in the Estonian Internal Security Service. The story from CSM Passcode goes into more details about how vigilant they have to be to fight Russian propaganda. These aren’t isolated examples of how sophisticated they are. They also were the first EU country to teach HTML coding in its elementary schools back in 2012, and the Skype software was developed there.
Their former Prime Minister Taavi Rõivas has even appeared on the The Daily Show with Trevor Noah to talk about these programs. Clearly, they have a strong vision, made all the more impressive by the fact that they had almost no Internet access just a few years ago when they were still part of the Soviet empire. Certainly a place to keep an eye on.




 This week Paul Gillin and I talk to Crowded Ocean’s partners
This week Paul Gillin and I talk to Crowded Ocean’s partners  Instead, Carol and Tom suggest that you examine more closely the different component skills that make up marketing, and staff accordingly. These include product management, corporate marketing, product marketing and IT fluency. The evolved CMO has the backbone of the marketing department, the breadth and understanding of the customer experience and the depth of a new key organizational growth pillar that shapes their point of view. Our guests suggest that the initial full-time marketing insider should be someone that they call “Seth” who is a 28-year-old numbers jockey who can give their sales organization demand generation data.
Instead, Carol and Tom suggest that you examine more closely the different component skills that make up marketing, and staff accordingly. These include product management, corporate marketing, product marketing and IT fluency. The evolved CMO has the backbone of the marketing department, the breadth and understanding of the customer experience and the depth of a new key organizational growth pillar that shapes their point of view. Our guests suggest that the initial full-time marketing insider should be someone that they call “Seth” who is a 28-year-old numbers jockey who can give their sales organization demand generation data. Both of the newer cameras can record ambient audio and can see a 130 degree video view in HD quality, along with night vision rather at 850 nm that can see things up to 25 feet away. You can also control a 8x zoom lens in real time. The original Arlo cameras has a 110 degree view and no audio capabilities.
Both of the newer cameras can record ambient audio and can see a 130 degree video view in HD quality, along with night vision rather at 850 nm that can see things up to 25 feet away. You can also control a 8x zoom lens in real time. The original Arlo cameras has a 110 degree view and no audio capabilities. 


 The odd thing about this person is that he is still a kid, an 11-year-old to be exact. His name is Reuben Paul and he lives in Austin. Reuben already has spoken at numerous infosec conferences around the world, and he “owned the room,” as one of the generals who runs one of the security services mentioned in a subsequent speech. What made Reuben (I can’t quite bring myself to use his last name as common style dictates, sorry) so potent a speaker is that he was funny and self-depreciating as well as informative. He was both entertaining as well as instructive. He did his signature story, as we in the speaking biz like to call it, a routine where he hacks into a plush toy teddy bear (shown here sitting next to him on the couch along with Janice Glover-Jones, who is the CIO for the Defense Intelligence Agency) using a Raspberry Pi connected to his Mac.
The odd thing about this person is that he is still a kid, an 11-year-old to be exact. His name is Reuben Paul and he lives in Austin. Reuben already has spoken at numerous infosec conferences around the world, and he “owned the room,” as one of the generals who runs one of the security services mentioned in a subsequent speech. What made Reuben (I can’t quite bring myself to use his last name as common style dictates, sorry) so potent a speaker is that he was funny and self-depreciating as well as informative. He was both entertaining as well as instructive. He did his signature story, as we in the speaking biz like to call it, a routine where he hacks into a plush toy teddy bear (shown here sitting next to him on the couch along with Janice Glover-Jones, who is the CIO for the Defense Intelligence Agency) using a Raspberry Pi connected to his Mac.