I have been living with Tinnitus for 20 years, but until recently, I didn’t own it. Before I tell you how this came to be, a little background.
In 1998, I was diagnosed with Meniere’s Disease. I was experiencing intense dizzy spells, and many of you who are readers of this journal have heard or lived through what follows: dietary changes, a series of unsatisfying visits to various MDs, and a great deal of frustration. Back then, it wasn’t easy to do Internet research, but eventually my attacks stopped. What I got out of that experience was a case of Tinnitus.
My situation is a bit unique: I have been deaf in my left ear since birth. My right ear hears just fine – except for this continuous tone that sometimes is louder, sometimes is softer, but is always there. Over the years, I have learned to deal with it, but owning it? Nope. Sometimes I would hold a pity party for myself, sometimes it was more than annoying, especially when I was in crowded noisy rooms or restaurants. I remember one time I was at a professional conference of about 300 people. For dinner, we were seated at a very long tables and the noise was literally deafening. I quickly ate my meal and literally ran back to my room, in pain from the noise. I know it looked odd to my dinner companions.
I have been a member of ATA for most of those decades, and appreciate the amount of knowledge that the association provides its members in trying to understand and cope with this disease. But I didn’t own my Tinnitus. That is, until I went to the Iowa conference this past summer.
The conference is small – less than 100 attendees and that includes many of the speakers over two very full days. The audience is 90% professionals, including nurses, MDs and audiologists, with a few of us patients scattered in and allowed to participate. It was very worthwhile, and I want to describe some of the things that I learned during the event. I was surprised at how much I didn’t know, and it wasn’t just learning medical jargon, but actual, actionable, useful stuff that helped me begin to own my disease.
What does owning mean? It means that you control it, rather than it controlling you. You aren’t defined by your Tinnitus, you aren’t at its mercy, and you manage your own treatment and your own response to the disease. The noise you and I hear may be all in our heads, but we have to use our brains to figure out a way to cope and live our lives. Many of the stories here in this journal have carried this theme, but for some reason I didn’t really understand what they were getting at until I was sitting in the conference, listening to the various presentations. Then it all clicked, so to speak. (Sorry for that pun.)
Here are a few other things that I heard and took away from the event.
While I knew that Tinnitus is different for everyone, I didn’t realize how different it was. Meeting others who have it and hearing their stories was good to understand its individuality and the different paths that patients have taken to understand and cope with Tinnitus. When you see the breadth and depth of variations of research that is going on around the world, you begin to understand this is a huge problem – or many problems – to solve. You can get some of this by attending one of the local ATA support groups, too.
Another thing that I liked about the Iowa conference is that you get to put yourself in your doctor’s shoes and see Tinnitus from his or her perspective. This is helpful in understanding how they will treat you and respond to your needs and concerns. There were several presentations from audiologists, therapists, and other professionals so again you could appreciate their different points of view.
Meeting the ATA staff and board members attending the conference (ATA is one of the sponsors) was also a treat. It helps to put a face with the organization, and also gave me an opportunity to thank them personally for all their hard work in helping us.
The conference is also a good place to get first-hand knowledge about cutting-edge research, particularly by the University of Iowa team that has been involved in Tinnitus work for decades. By the end of the two days, you feel like you know these folks quite well.
At the conference, vendors present their devices and explain how they are used and whom they are intended. During one of these sessions, I learned that hearing aids are ways to manage Tinnitus, even if you don’t have much in the way of hearing loss. This is because they ca be programmed to block out the frequencies that you think you are hearing with your Tinnitus noise(s). Now I know I am a bit of an unusual situation – no hearing in one ear, and the opposite in the other. Not to worry – there are specific kinds of aids for this problem. Years ago I investigated in using a BAHA hearing aid, which involves implanting a microphone in the side of your skull (in my case, the left side) and transmitting the sound through your bones to your hearing ear. When I tried on the sample aid back then, I could actually hear stereo and locate the source of the sound coming from behind me – both of these for the first time. I opted not to use the aid then. But the advances of technology with regards to digital signal processing are significant, and now there are wireless CROS aids that can work with your cellphone via Bluetooth connections. At the conference, I could talk to audiologists who have installed both BAHA and CROS aids and get their first-hand experience. That kind of insight would be nearly impossible as an ordinary patient.
As patients, we tend to interact with the medical/industrial complex at the moment when we have a problem: we break a bone, we want it fixed. We have an infection, we want to get rid of it. But the single point of contact with our doctors method doesn’t work with a chronic condition such as Tinnitus (or Meniere’s or whatever). That is because research is ongoing: new drugs, new procedures, new devices, and so forth. We aren’t watching the medical literature like our doctors are doing, because we are busy living our lives. And even if we are willing to put the time into doing Internet research, we aren’t going to medical conferences and learning about many of the latest technologies and techniques. Until I attended the Iowa conference, my knowledge of Tinnitus was limited to what I read in this journal. While that is great it can’t provide me with everything that is going on in the world. The Iowa conference can quickly bring you up to speed in a way that doing your own net-based research or reading a medical journal article, even one intended for patients, can’t easily do.
Now, most medical conferences are way beyond my skills and knowledge (or so I imagine), and probably yours as well. The jargon of just understanding the different parts of the human body alone is daunting enough. The Iowa conference certainly had its moments when I was totally lost. But it had plenty of other moments when I got useful information that was clearly explained and in terms that any layperson could understand.
Next summer, put Iowa City on your calendar and plan on coming to the conference. You will be welcomed, and you might get to understand more about our common affliction. The cost is minimal for the benefits I received.

 I wrote a series of papers for TechTarget, sponsored by Veeam, mainly about ransomware. Here are links to download each paper (reg. req.):
I wrote a series of papers for TechTarget, sponsored by Veeam, mainly about ransomware. Here are links to download each paper (reg. req.): In this
In this  There were some standout reports that I will recommend. First, if you are new to email encryption, the best general source that I have found is
There were some standout reports that I will recommend. First, if you are new to email encryption, the best general source that I have found is  Autodesk is the company behind AutoCAD and some 170 other products that are based on that industry segment. When you first see how many blogs they have, you think: that can’t possibly be the right strategy for them. But the more you look into what they are doing, the more you understand that this is actually brilliant. These different blogs (some of which you can see in the screen capture here) show something more than just quantity. For example, each Autodesk product and blog has its own dedicated marketing team, so it’s up to each to decide how to structure its operation and tell it’s own story. So as you are examining what Autodesk is doing, here are a few pointers.
Autodesk is the company behind AutoCAD and some 170 other products that are based on that industry segment. When you first see how many blogs they have, you think: that can’t possibly be the right strategy for them. But the more you look into what they are doing, the more you understand that this is actually brilliant. These different blogs (some of which you can see in the screen capture here) show something more than just quantity. For example, each Autodesk product and blog has its own dedicated marketing team, so it’s up to each to decide how to structure its operation and tell it’s own story. So as you are examining what Autodesk is doing, here are a few pointers.
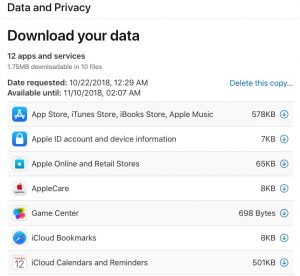
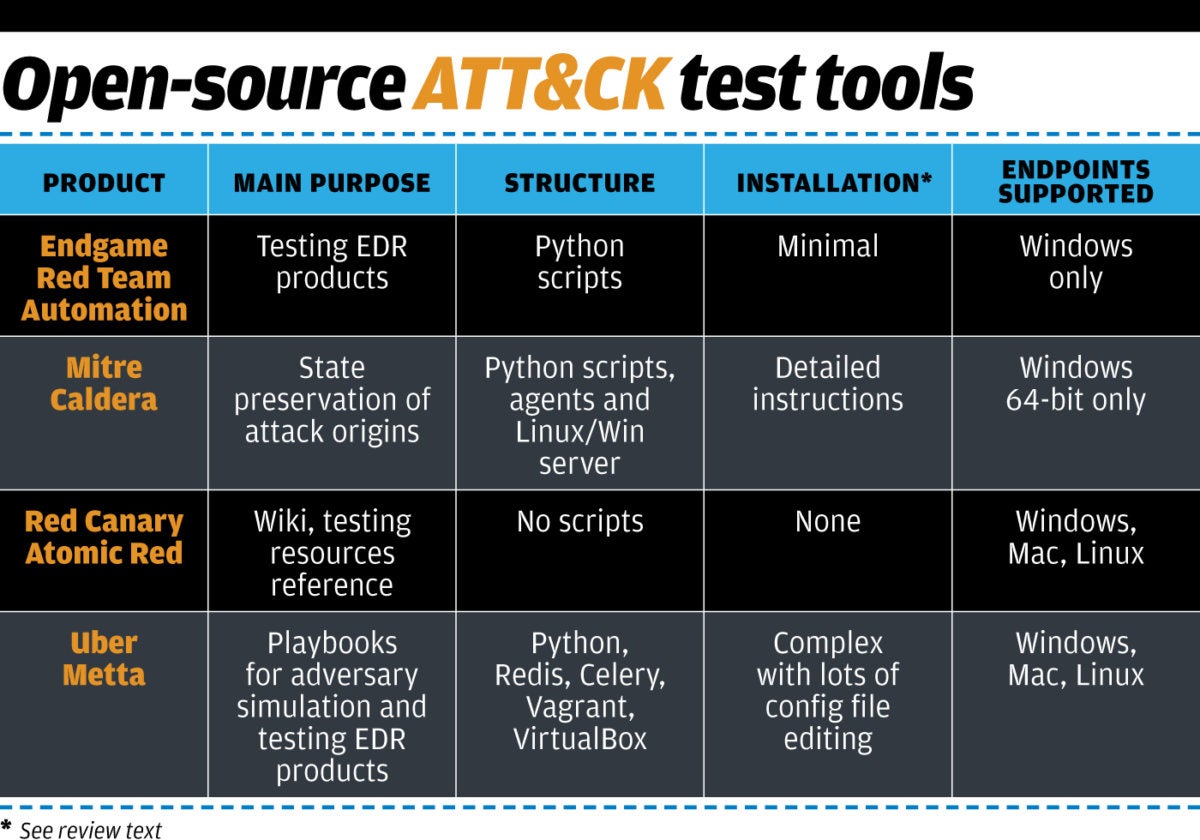 In an article that I wrote last week for CSOonline, I d
In an article that I wrote last week for CSOonline, I d