Honeypots are once again in the news. If you stopped by the Watchguard booth at last month’s RSA Conference in San Francisco, chances are good that you connected with one of its Wifi hotspots. Those hotspots were there to log how many people would try to connect to an open network. Watchguard found that the average length of time spent connected was more than enough to compromise the connection. Recently, researcher Doug Rickert has been experimenting with the open source Cowrie SSH honeypot, writing about it on Medium. He found an average of at least 200 daily attempts, a few of them from serious hackers who tried to penetrate his honeypot further.
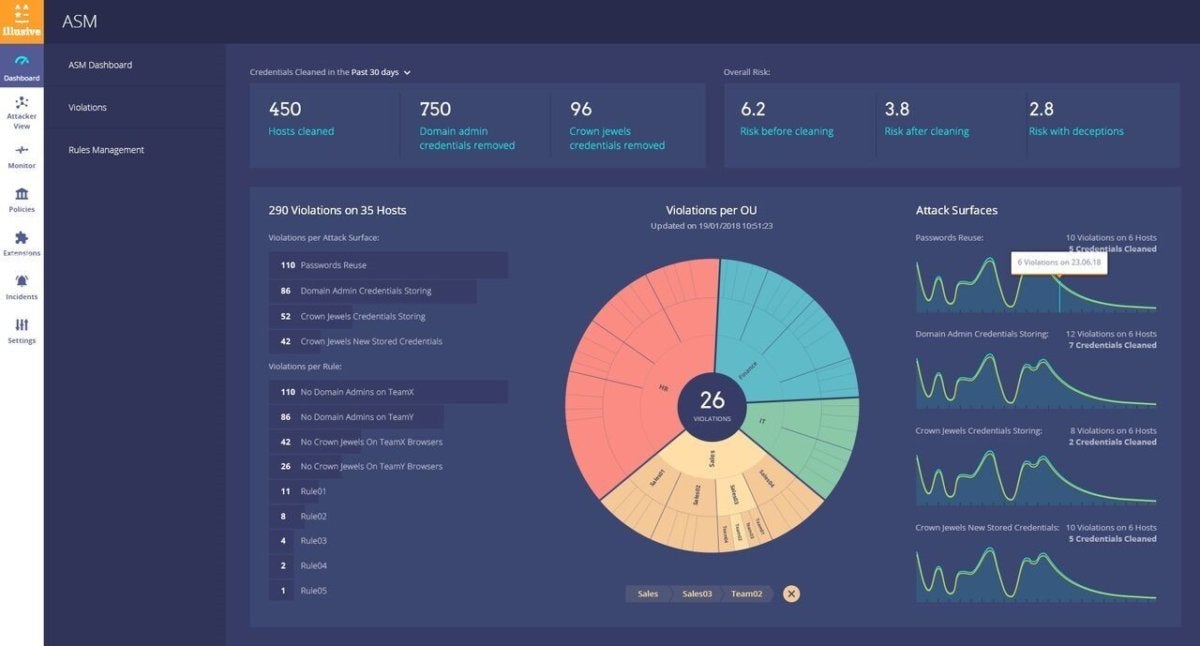 In this post for CSOonline, I talk about what makes honeypots so compelling as a security solution, what are some things to look for when you are thinking about purchasing a more thorough commercial deception package, different types of honeypots, and a table that links to some of the more popular solutions.
In this post for CSOonline, I talk about what makes honeypots so compelling as a security solution, what are some things to look for when you are thinking about purchasing a more thorough commercial deception package, different types of honeypots, and a table that links to some of the more popular solutions.
Here is a new idea for a “tarpit,” a trap for LLM trainer/scrapers that sucks the scraper code into wasting a lot of CPU resources.