In today’s installment, I look at the Philips Hue lighting system. This has four main components: a network-attached bridge or controller, the smart bulbs themselves, web-based software and the smartphone software that is used to turn your lights on and off. We tested the product in the same suburban home location outside of St. Louis where we tested our earlier products, connecting Hue to both the Alexa Echo Dot and the Google Home hubs.
Hue comes with three different kinds of bulbs: white-only, white ambiance and multi-color, which includes white. The White Ambiance allows you to do more than just dim up and down at the one color temperature and gives you access to 50,000 shades of white light. I tested the multi-color. Both come with built with radios that communicate via the ZigBee LightLink protocols back to the bridge.
To me, a lamp is a necessary evil and something that doesn’t require a great deal of thought. This is because I am someone with zero sense of interior design. I tell you this upfront, which is one of the reasons I was testing these products at a home where both residents have a lot more design-savvy and understanding of lighting placement and mood creation.
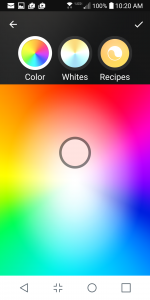 If you are a design philistine like me, then you probably won’t get much out of this product and should just stick with ordinary lamps. But if you do take the plunge, make sure you are buying what Philips calls “gen 3” bulbs (which is what I tested). These bulbs have deeper green, cyan and blue for even better mood setting. Philips claims the bulbs can deliver 16 million different colors, but since I am colorblind I couldn’t verify this claim. Nevertheless, you have a wide color palette that you can play with on your smartphone and have a lot of fun finding that exact color to match your mood, your decor, what your spouse is wearing, or whatnot. All the bulbs are LEDs, so are very energy-efficient. They all fit into a standard base and (unlike the early CF bulbs) are small enough to fit in most ordinary lamp housings.
If you are a design philistine like me, then you probably won’t get much out of this product and should just stick with ordinary lamps. But if you do take the plunge, make sure you are buying what Philips calls “gen 3” bulbs (which is what I tested). These bulbs have deeper green, cyan and blue for even better mood setting. Philips claims the bulbs can deliver 16 million different colors, but since I am colorblind I couldn’t verify this claim. Nevertheless, you have a wide color palette that you can play with on your smartphone and have a lot of fun finding that exact color to match your mood, your decor, what your spouse is wearing, or whatnot. All the bulbs are LEDs, so are very energy-efficient. They all fit into a standard base and (unlike the early CF bulbs) are small enough to fit in most ordinary lamp housings.
Why bother with smart bulbs? Several reasons. First, you can remotely turn them on and off, both instantly and on a specified schedule, to make your home more comfortable and secure. Second, you can set various moods by having them dim or brighten appropriately. And finally, you have bragging rights when you have your friends over for dinner or parties. By now many of you have already bought your own smart hub: this gives you the first practical application that can readily demonstrate its utility.
When I first got the Hue kit I thought it was mostly “nice to have” but not an essential use case. The more I and my test couple used them, the more we liked them and the more we came to rely on the ability to control them at will and to set different moods. I think this bears emphasis: Hue is creating something new and really giving you a new dimension on how you live and consume lighting in your home.
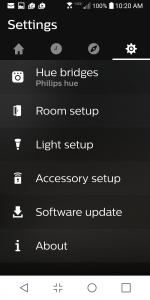 You don’t need a smart hub to operate your Hue lights, because you can control them via the smartphone app (shown here) or you can also purchase a variety of hardware controllers that can fit inside a standard light switch receptacle or sit on your coffee table if you want a physical object. That is all well and good, but really that gear is just a glorified “Clapper” device that is about as exciting. But using the Alexa or Google Home hubs means you have voice commands for your lights. This means you don’t have to look for your phone and can just turn your lights on or off quickly as you enter a room.
You don’t need a smart hub to operate your Hue lights, because you can control them via the smartphone app (shown here) or you can also purchase a variety of hardware controllers that can fit inside a standard light switch receptacle or sit on your coffee table if you want a physical object. That is all well and good, but really that gear is just a glorified “Clapper” device that is about as exciting. But using the Alexa or Google Home hubs means you have voice commands for your lights. This means you don’t have to look for your phone and can just turn your lights on or off quickly as you enter a room.
Getting setup from scratch took about 15 minutes on either hub, using a very similar process. The biggest issue I faced was switching my lighting system from the Amazon to the Google hub, which a normal user wouldn’t necessarily do. If you are going to change hub vendors, you should do a factory reset to make things easier. The controller/bridge connects to your home network via Wi-Fi, and it also works with Apple Home Kit hubs too.
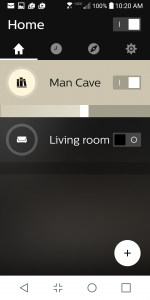 The most important part of the hub-related setup is naming your various rooms where the bulbs will be located. The workflow for doing this is different in Amazon Alexa versus the Google Home. With Alexa, it picks up this information from the Hue app. In Google, you have to create your room names on its app.
The most important part of the hub-related setup is naming your various rooms where the bulbs will be located. The workflow for doing this is different in Amazon Alexa versus the Google Home. With Alexa, it picks up this information from the Hue app. In Google, you have to create your room names on its app.
For the most part, the Hue bulbs worked fine with either Alexa or Google Home. But sometimes Alexa would make a mistake, thinking a particular bulb was on when it was off, or vice-versa. And sometimes Alexa would turn on a bulb in the wrong room. We couldn’t reproduce these errors. It isn’t clear who is at fault here: because sometimes the app shows a bulb is on when it is off. For the majority of time though, things work as intended.
If you are just going to control your lights locally — meaning while you are in your home — then you don’t have to worry about the web server piece of the product. This is needed for two purposes: first for controlling your lights when you are away from home, and second to integrate with any Nest products and other home automation web services. For either purpose you will need to create an account on meethue.com and then use that login on your smartphone app. As with other smart home products, only one account (meaning one email address) per home is allowed. If you want multiple family members to have lighting controls, you might want to create a special email address that everyone can access. Philips is looking into having multiple accounts with different access rights at some point in the future.
Once you get going with the standard bulbs, Philips makes a bunch of different other bulb sizes that can you expand your horizons and play interior decorator. I didn’t test any of these. You can purchase a rechargeable portable light source called Go and lights that come with a variety of their own decorative bases. Given that Philips has been making electric lights for more than a century, this is not unexpected that there will be others joining its Hue product line in the near future.
Hue comes in various product configurations, the basic white-only starter kit with two bulbs and the controller is $70. It is available online and in a variety of electronics and lighting stores too.
 I take a look at the Linksys Velop Wi-Fi access points. This is the third in my series of reviews for Network World on smart home devices. If you are going to invest in smart home tech, you want a solidly performing wireless network throughout your house. While I had some minor issues, the Velop delivered solid performance and I recommend its use, particularly if you have existing radio dead spots in your home or have to use multiple networks to cover your entire property. You can
I take a look at the Linksys Velop Wi-Fi access points. This is the third in my series of reviews for Network World on smart home devices. If you are going to invest in smart home tech, you want a solidly performing wireless network throughout your house. While I had some minor issues, the Velop delivered solid performance and I recommend its use, particularly if you have existing radio dead spots in your home or have to use multiple networks to cover your entire property. You can 
 Today I begin a series of reviews in Network World around smarter home products. Last year we saw the weaponized smart device as the
Today I begin a series of reviews in Network World around smarter home products. Last year we saw the weaponized smart device as the  Back in the early 2000’s, I
Back in the early 2000’s, I

 The on-premises and cloud editions of Skype for Business Server and the Cloud PBX are promising and less-expensive alternatives to traditional phone systems, but come in a complex array of options and require integration. The software has gained some promising features along with growing support for third-party software, hardware and services. In my
The on-premises and cloud editions of Skype for Business Server and the Cloud PBX are promising and less-expensive alternatives to traditional phone systems, but come in a complex array of options and require integration. The software has gained some promising features along with growing support for third-party software, hardware and services. In my  This month the updated Windows 10 Anniversary Edition is now available for download. (Here is a
This month the updated Windows 10 Anniversary Edition is now available for download. (Here is a