 Few businesses create a completely different product every couple of weeks, not to mention take their product team on the road and set up a completely new IT system on the fly. Yet, this is what the team at Red Bull Racing do each and every day.
Few businesses create a completely different product every couple of weeks, not to mention take their product team on the road and set up a completely new IT system on the fly. Yet, this is what the team at Red Bull Racing do each and every day.
A video featuring the racing company’s staff and its ultra-fast pace was featured at Citrix Synergy conference in Orlando earlier this summer. When I saw it, I wanted to find out more about what happens behind the scenes. Indeed, during the week of Synergy, they were busy at one of the 20 different races they participate in around the world each year. “We design and manufacture all of our cars and go through some 30,000 engineering changes a year,” says Matt Cadieux, CIO of Red Bull Racing, “We create new car parts for every race because all of our cars get torn apart and rebuilt to new specifications that are designed to make the car go faster.”
The typical race week starts out with the team showing up several days ahead of the green flag, ready to unload 40 tons of equipment on the first day. The next day, the communications networks are connected and the cars assembled. “We don’t have time to debug things, we have to be up and running and do that in 20 different places around the world,” he said.
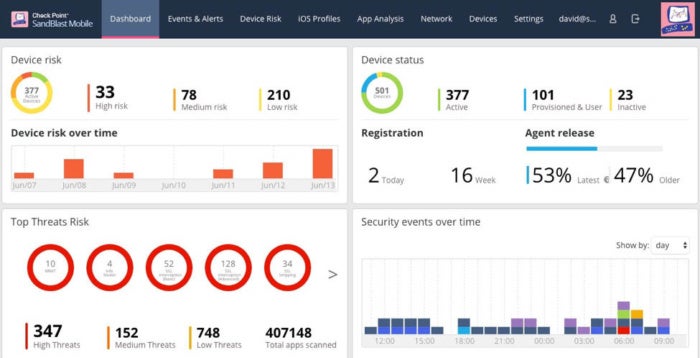
The company is based in the UK, where they have a very space-age data center. And it should! They designed it based on the look and feel of NASA’s mission control room in Houston. “We have one of the largest video walls in Europe,” said Cadieux. The data center houses three Linux clusters, a Windows cluster, and uses IBM Spectrum Storage to manage all their resources.
All that video isn’t just for showing pretty pictures. They have some serious data visualizations, where they are tracking in real time more than 200 different car metrics dealing with its performance. “It is very graphically intensive, and behind the graphics are some pretty large databases too,” Cadieux said.
Getting these graphically-rich screens sent to the racing team at the track requires some serious computing horsepower and a very dependable remote desktop experience, and that is where Citrix comes into play. “If we didn’t have Citrix, there is no way we could manage these apps effectively,” he said. The racing company uses a combination of XenDesktop and XenServer along with NetScaler to provide firewalls and load balancing. As their infrastructure has gotten more complex, they have been able to add functionality from this collection of products easily.
 That is one of the reasons why Red Bull Racing has worked with Citrix for many years. “We always had great tech support from them and they always exceed our expectations. We have access to their developers and early code releases. For our use cases, we are always pushing technical boundaries, because we not afraid to try new things. We give a lot of blunt and honest feedback to their product teams, too.”
That is one of the reasons why Red Bull Racing has worked with Citrix for many years. “We always had great tech support from them and they always exceed our expectations. We have access to their developers and early code releases. For our use cases, we are always pushing technical boundaries, because we not afraid to try new things. We give a lot of blunt and honest feedback to their product teams, too.”
As you might imagine, using all these graphical screens places a burden on having the lowest possible network latencies when those bits are shipped all over the planet. “We needed to take some heavyweight apps and use them in remote places, and that means we need some solid networks too.” They make use of AT&T VPN technologies to provide their global connectivity.
For example, when they are in Australia, they can get less than 380 ms round trip latencies back to their data center in the UK. “Sometimes, users can feel that delay, but they still can use our apps. When we are running races in Europe, you almost can’t tell the difference between the remote session and being back inside our data center,” he said.
The support team that they bring to each race used to be bigger, but thanks to XenDesktop they have managed to leave several key team members back in the UK. “We still can have the collaboration between people at the track and at home with XenDesktop. The result is that we can make better and more informed decisions,” he said. There is also a limit on the number of team members that can be present on the track as part of the racing staffing regulations.
Red Bull Racing has been around for more than a decade and, as you might assume, their current technology portfolio is “massively different” when compared to what they used back then. “When we first started, our operations room was the size of a broom closet and our simulations had almost no correlation to what we observed in the real world. Back then it was more of a science project than something that could make appropriate business decisions. Now, our math models are much more complex and we do a better job with visualizing our data. The size of our models and the infrastructure required to run them has also exploded over time.” As he mentions in this Network World article, “It allows us to get a very under-the-covers view of the health of the car, where you can understand forces, or you can see things overheating, or you can see, aerodynamically, what’s happening and whether our predictions in computational fluid dynamics and the wind tunnel are what really happens in the real world.”
Red Bull Racing have also been able to be more responsive; now, they can instrument a problem, track down a solution, and have it ready for race day all in a matter of hours. “We can now react to changes and surprises and deal with them in a more data-driven way,” he said.
Cadieux came from a Detroit-area traditional automaker before he moved across the pond and started supporting race cars. The two businesses have more in common than you might think, because ultimately they are all about making engineering decisions around the cars themselves. “We build our cars for performance, rater than for the mass market, that’s all. The software problems are similar.” Well, maybe he is just being modest.
Does Cadieux have one of the best jobs in IT? Certainly. “It is a very cool job and I am very lucky to have it. We get to solve some very interesting problems and be at the forefront of using tech to improve our business. It is great to work with such a cohesive team and be able to move very quickly, and merge engineering with our business needs.”
 In the intervening years since that story, tracking technology has gotten better and Internet privacy has all but effectively disappeared. At the DEFCON trade show a few weeks ago in Vegas, researchers presented a paper on how easy it can be to track down folks based on their digital breadcrumbs. The researchers set up a phony marketing consulting firm and requested anonymous clickstream data to analyze. They were able to actually tie real users to the data through a series of well-known tricks, described in this report in Naked Security. They found that if they could correlate personal information across ten different domains, they could figure out who was the common user visiting those sites, as shown in this diagram published in the article.
In the intervening years since that story, tracking technology has gotten better and Internet privacy has all but effectively disappeared. At the DEFCON trade show a few weeks ago in Vegas, researchers presented a paper on how easy it can be to track down folks based on their digital breadcrumbs. The researchers set up a phony marketing consulting firm and requested anonymous clickstream data to analyze. They were able to actually tie real users to the data through a series of well-known tricks, described in this report in Naked Security. They found that if they could correlate personal information across ten different domains, they could figure out who was the common user visiting those sites, as shown in this diagram published in the article. So is this just some artifact of gung-ho security researchers, or does this have any real-world implications? Sadly, it is very much a reality. Last week Disney was served legal papers about secretly collecting kid’s usage data of their mobile apps, saying that the apps (which don’t ask parents permission for the kids to use, which is illegal) can track the kids across multiple games. All in the interest of serving up targeted ads. The full list of 43 apps that have this tracking data can be found here, including the one shown at right.
So is this just some artifact of gung-ho security researchers, or does this have any real-world implications? Sadly, it is very much a reality. Last week Disney was served legal papers about secretly collecting kid’s usage data of their mobile apps, saying that the apps (which don’t ask parents permission for the kids to use, which is illegal) can track the kids across multiple games. All in the interest of serving up targeted ads. The full list of 43 apps that have this tracking data can be found here, including the one shown at right.
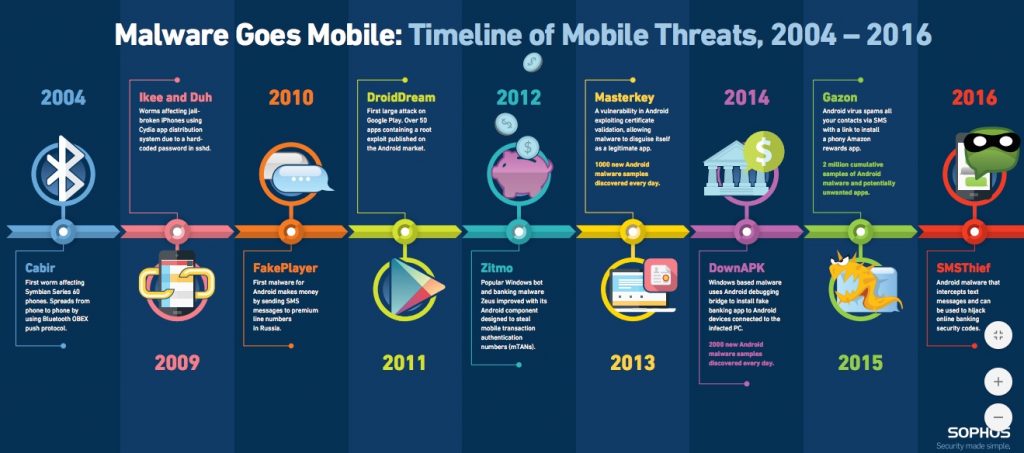
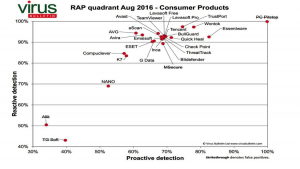
 Paul Gillin and I talk to
Paul Gillin and I talk to 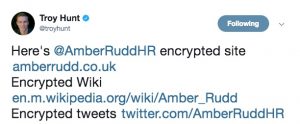
 Few businesses create a completely different product every couple of weeks, not to mention take their product team on the road and set up a completely new IT system on the fly. Yet, this is what the team at Red Bull Racing do each and every day.
Few businesses create a completely different product every couple of weeks, not to mention take their product team on the road and set up a completely new IT system on the fly. Yet, this is what the team at Red Bull Racing do each and every day.