 AOL is eliminating its AIM service after a 20 year run. It is sort of an ignominious end to the once-popular IM platform. Many of us were teens (or parents thereof) when AIM was in its heyday, and I was a big user back in the early 2000s when I worked at CMP to communicate with our far-flung staff (and even the folks sitting a few feet away from me too). That brings up how IM can bring together work teams to collaborate, and how IM has been an essential tool with many of my jobs since then. Just this morning I was using IM to “talk” to my editor in Pittsburgh and another researcher in Europe for my Inside Security newsletter. Like many of you, I take these conversations for granted and like many tech companies, Inside.com has standardized on Slack, and indeed I participate in numerous other Slack groups now.
AOL is eliminating its AIM service after a 20 year run. It is sort of an ignominious end to the once-popular IM platform. Many of us were teens (or parents thereof) when AIM was in its heyday, and I was a big user back in the early 2000s when I worked at CMP to communicate with our far-flung staff (and even the folks sitting a few feet away from me too). That brings up how IM can bring together work teams to collaborate, and how IM has been an essential tool with many of my jobs since then. Just this morning I was using IM to “talk” to my editor in Pittsburgh and another researcher in Europe for my Inside Security newsletter. Like many of you, I take these conversations for granted and like many tech companies, Inside.com has standardized on Slack, and indeed I participate in numerous other Slack groups now.
More than ten years ago, I wrote this story for the NY Times, The I.M. Generation Is Changing the Way Business Talks. In it, I describe the opportunities and challenges that IM faced in the modern business. To me, the timing of this article points out that there still were plenty of businesses that hadn’t even considered any IM tools. IBM was quoted in the piece as using its own IM tool for sending millions of messages daily, and eliminating voice mail tag. In my article, I called IM “the new black,” meaning it was trendy back then.
Today my phone rarely rings — to the point that I haven’t had a “desk” office phone in so long that I can’t even remember. Between IM and emails, there really isn’t any need to “talk” to anyone anymore.
One of the reasons why businesses loved IM is that its own workers literally grew up on the service. “AIM was a domain parents didn’t understand, giving it a feeling of clandestine cool.” This is from Tech Crunch, which has this tribute. In that link is a clip with a reminder of its pernicious sound effects. Boy does that bring back memories. One of my favorites was when my daughter was a pre-teen, deeply steeped into using AIM to communicate with 100 of her closest friends. I had trouble getting her to sign off when it was bed time, and so told her that she was going to get kicked off the system promptly at 10 pm. I had set up a firewall rule on our home router to block access to IP port 5190 at that time. She didn’t think I could do that, and after a few warnings I remember her realizing that I meant business when the hour struck. Being a parent back in that era was a lot easier than today, to be sure.
Speaking of pre-teens, I found this awkward story about making dating decisions using AIM. Again, a typical use case from back in that era.
But while AIM set the standard for IM, it didn’t keep up with the times. Ironically, as more users became mobile, they migrated to other IM tools because AOL’s mobile clients were late to the party and under-powered. They were slow to provide APIs, something Slack does in spades and one of the reasons you can find Slack “bots” for all sorts of add-on applications. And as users migrated to other IM services, AOL itself stopped using the service for its own internal communications, at one point using Slack itself. That is bad news when you can’t even find the tool capable for your own people.
AIM was also victim to SMS services and smartphones. As more people used both, the use cases blurred further between personal and corporate messaging. My daughter, who is now in her late 20s, told me that she hasn’t used AIM in years. Now she uses WhatsApp for both business and personal reasons, and that can be an issue when she is trying to get her work done and can’t easily find a conversation.
Well before Facebook-stalking was a thing, AIM profile stalking became slang for many users. This Ars writer recalls he had his “first taste of how the Internet could enable asynchronous self-expression and personal broadcasting amid a tight-knit social group.” That was before blogs, before MySpace even. So while I haven’t used AIM in a long time, I am sad that it is actually getting turned off soon.
 To provide better spam and phishing protection, a number of ways to improve on email message authentication have been available for years, and are being steadily implemented. However, it is a difficult path to make these methods work. Part of the problem is because there are multiple standards and sadly, you need to understand how these different standards interact and complement each other. Ultimately, you are going to need to deploy all of them.
To provide better spam and phishing protection, a number of ways to improve on email message authentication have been available for years, and are being steadily implemented. However, it is a difficult path to make these methods work. Part of the problem is because there are multiple standards and sadly, you need to understand how these different standards interact and complement each other. Ultimately, you are going to need to deploy all of them.
 Part of this timing element is also how you deal with bugs and what happens when they occur. Yes, all software has bugs. But do you tell your user what a particular bug means? Sometimes you do, sometimes you put up some random error message that just annoys your users.
Part of this timing element is also how you deal with bugs and what happens when they occur. Yes, all software has bugs. But do you tell your user what a particular bug means? Sometimes you do, sometimes you put up some random error message that just annoys your users. An old scam to separate people from their money has been gaining more popularity. It uses a cellphone protocol called
An old scam to separate people from their money has been gaining more popularity. It uses a cellphone protocol called 
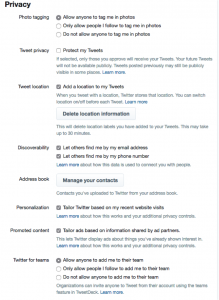 Balancing anonymity and privacy isn’t an either/or situation. There are many shades of gray, and it is more of an art than science. Making sure your users understand the distinction between the two terms and setting their appropriate expectations of both should be a critical part of any job managing IT security.
Balancing anonymity and privacy isn’t an either/or situation. There are many shades of gray, and it is more of an art than science. Making sure your users understand the distinction between the two terms and setting their appropriate expectations of both should be a critical part of any job managing IT security.