It is an origin story that has been told numerous times: a group of computer nerds meets in college and goes on to build a software startup, eventually selling their company. But this is a story with a twist: four of the team members met more than 20 years ago when they were undergrad engineers at Carnegie Mellon University. Together with a fifth team member they would go on to have five different and successful exits at various tech startups.
The team includes Peter Pezaris (CEO and developer), David Hersh (product manager), James Price (devops), Michael Gersh (marketing/analytics) and latecomer Claudio Pinkus (who joined the others 13 years ago).
Their projects included:
- Codestream, a devops collaboration platform which was founded in 2017. Earlier this summer, NewRelic announced they were acquiring the company this week.
- Glip.com, a team collaboration platform acquired by RingCentral in 2015.
- Multiply.com, a social commerce platform acquired by Naspers in 2010.
- Commissioner.com, one of the first online fantasy sports platforms, which was acquired by CBS/Sportsline, and
- Ask.com, acquired by IAC in 2005.
What is intriguing about the group is how well they worked together in these various companies. The group eventually settled into specific roles – Pezaris has been the CEO and chief coder in the last three ventures – and have worked from different locations well before the pandemic made remote work the norm for many of us.
Because the team has been geographically remote, they have tended to focus on building better collaboration tools over the years as they built their various enterprises. This is most obvious with their latest venture, Codestream, a free open-source implementation which allows developers to collaborate on writing code. It works with integrated development environments (IDEs) JetBrains, VS Code and Visual Studio and supports pull requests from GitHub/GitLab and BitBucket and integrates with other code management and messaging tools such as Jira, Slack and Asana.
That is a lot of integration, but the goal was to provide a richer request interface and annotation mechanism to make code reviews more meaningful, and to check out and run builds more quickly. Prior to Codestream, software engineering teams couldn’t easily talk to each other, particularly if they were using different IDEs or code editors and particularly if they wanted to comment on each other’s code in near real-time. The idea for the company was born out of doing cumbersome things, such as taking screenshots of one’s code and then sending it as an attachment in Slack. “This was a natural progression for us to applying messaging to our own daily use case,” said Pezaris. “We wanted to connect coding teams that don’t use the same IDE, especially if they are a larger team. There is always some odd person who is using a different editor.”
One of the notable differences with the team is how they used the Silicon Valley Y Combinator pitch competition to focus their business strategy. “The application process forces you to address how to turn your project into a real business, and by answering the questions it will get you to think more carefully about your market and customer acquisition,” said Pezaris. The team was frustrated because two of their past companies (Multiply and Glip) were precursors of Facebook and Slack respectively, both of which had done better jobs of integrating with Silicon Valley culture and of course had much better market positioning.
This shows that while a great idea can form a solid foundation for a startup, you need more than just the idea and some snappy app. You must put together how to create a business too. The Y Combinator competition brought the Codestream team to this next level.
Initially, they applied to the competition on a whim and almost didn’t finish their application in time. Pezaris told me that he was working on their final piece of their application, to create a one-minute video clip explaining their company. He was working on it in an airport hours before the deadline, and literally uploading the file as he was walking down the jetbridge to board his flight. They were accepted in the winter 2018 class. “While there is a very low chance you will be accepted, it is a golden ticket,” he said.
Another notable aspect of Codestream was how the company was founded on creating an open source offering. There are numerous success stories of other open source efforts that have been acquired by Red Hat, Oracle, and Microsoft, showing that this can sometimes be a pathway towards success.
Finally, the team never anticipated their eventual suitors going into each project. Multiply, for example, was bought by a South African media company that was interested in expanding to customers in emerging markets. “Each acquisition has been very different, and we have tried to stay on after the deal has closed. Some of the acquisitions brought up red flags that turned out to be nothing burgers, but the important point is that we all went through them together,” Pezaris said.
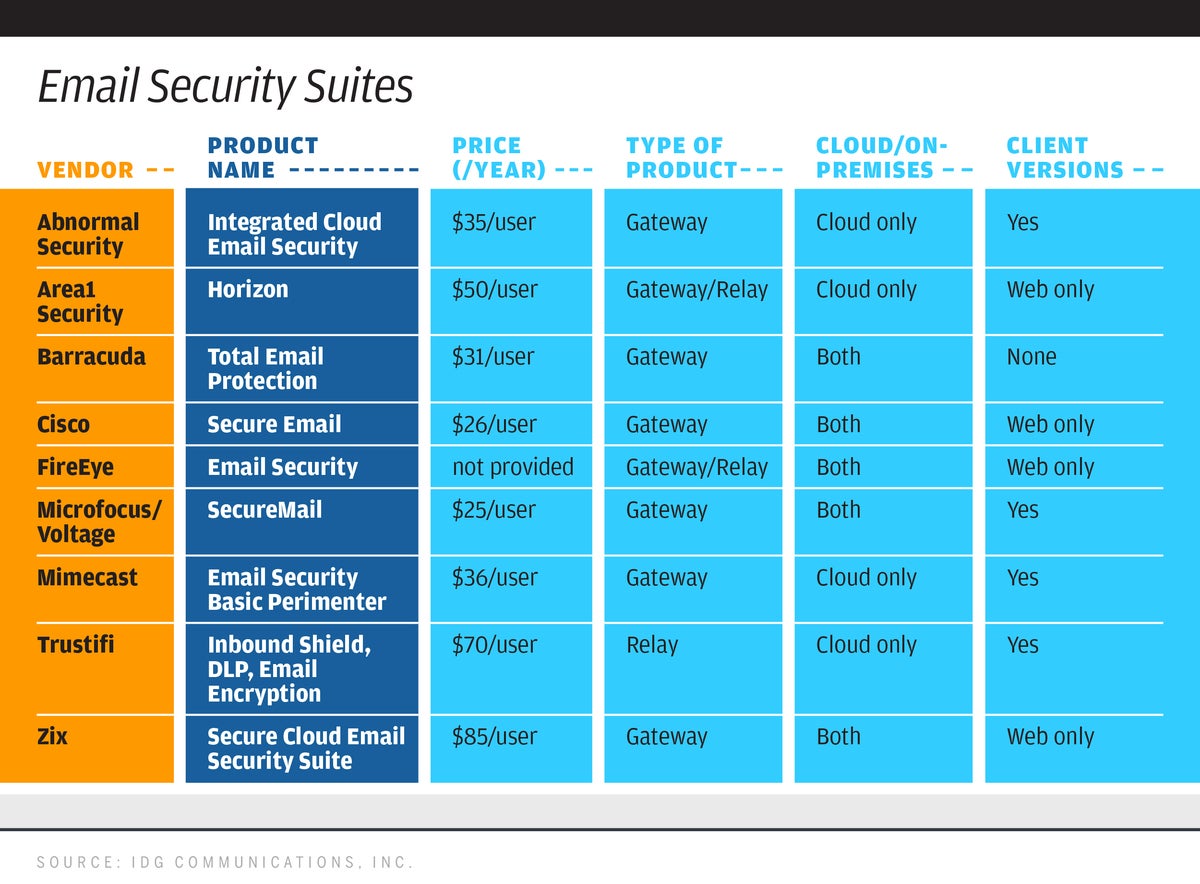
 One of the speakers was Dawn Song, a computer science professor at the University of California at Berkeley. She outlined a four-part framework for responsible data use by AI that includes:
One of the speakers was Dawn Song, a computer science professor at the University of California at Berkeley. She outlined a four-part framework for responsible data use by AI that includes: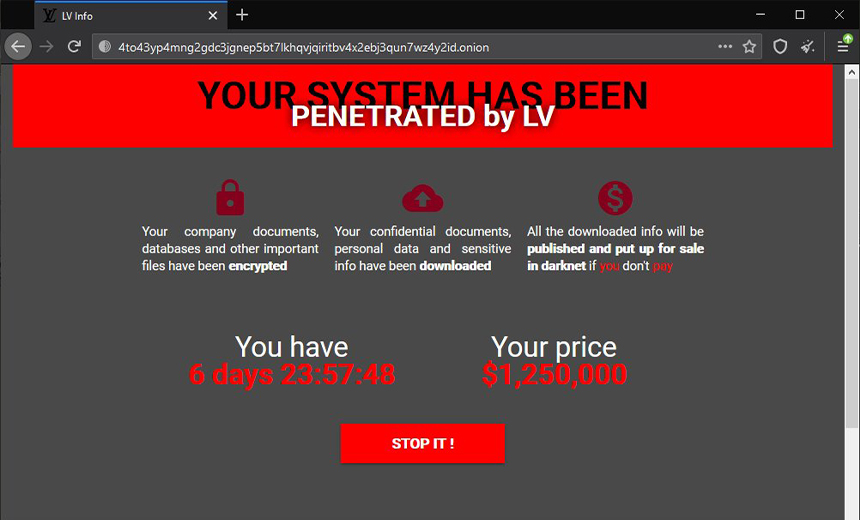
 A consortium of A-list reporters from 17 major American and Euro news outlets have begun publishing what they have learned from the documents unearthed by whistleblower Frances Haugen. The trove is a redacted copy of what was given to various legislative and watchdog US and UK agencies. The story collection is being
A consortium of A-list reporters from 17 major American and Euro news outlets have begun publishing what they have learned from the documents unearthed by whistleblower Frances Haugen. The trove is a redacted copy of what was given to various legislative and watchdog US and UK agencies. The story collection is being 