A number of countries — and now individual US states — are planning or have rolled out their smartphone-based contact tracing apps, in the hopes of gaining insight into the spread of infections. As you might imagine, this brings up all sorts of privacy implications and challenges. Before I review where in the world you can find an ailing Carmen San Diego, let’s look at the four major development projects that are now underway.
- The most well-known is a joint project from Google/Alphabet and Apple that is more a framework than an actual app. Vaughan-Nichols explains the actual mechanics and The Verge answers some of the questions about this effort. The UK is poised to test their app based on this framework sometime soon. Both vendors have stated that these protocols will be incorporated into later releases of Android and iOS later this summer.
- An open-source EU-based effort called DP-3T has developed an Apache/Python reference implementation here on Github. There are sample apps for Android and iOS too.
- A second joint EU-based closed-source effort called PEPP-PT has gotten support from 130 organizations in eight different countries. No current apps are yet available to my knowledge on either EU effort.
- Finally is something called BlueTrace/OpenTrace which is open source code developed by Singapore that is part of their tracing app called Trace Together. This was launched in late March. So far no one else has made use of their code.
All four proposals — I hesitate to call them implementations — are based a few common principles:
- When a match with a known infected user is made, all data is collected and stored locally. The idea is to preserve a user’s privacy, but still give public health officials some insight into the users’ movements. Some of the implementations combine local and centralized health data, such as the PEPP framework and Singapore’s app.
- The contacts are found through the use of Bluetooth low energy queries from your phone to nearby phones. These can reach up to a hundred feet in open air. The ACLU is worried that this data isn’t all that accurate, and has raised other privacy issues in this paper.
- There are various encryption protocols and layers, some better than others. The goal here is to anonymize the user data and keep hackers at bay. Some information and interfaces are documented, some things aren’t yet published or won’t be made public. And of course no system is 100% fail safe.
- The apps all rely on the GPS network, which limits their utility given that precise locations aren’t really possible. Some efforts are more sophisticated in cross-checking with the user’s common locations and Bluetooth contacts, but this is very much an inexact science. Taiwan tries to get around this by having the user call the health department and cross-check their own location history against this repository and request a test if there was an intersection.
- Usually, the local health agency interacts with the tracking data — that is the whole point of these things. But as in the case of Singapore, do we really want a central point where potential privacy abuse could happen? How long does the agency keep this location data, for example?
You can see where I am going with this analysis. We have a lot of things to juggle to make these apps really useful. One of the biggest issues is the need to combine tracking with testing to verify the spread of infection. This paper from Harvard goes into some of the details about how many tests will be needed for tracking to be effective. As you can guess, it is a lot more testing than we have done in the US.
Yes, many of us are now sticking at home, and obeying the recommendations or in some cases the varying local rules. (Israel, for example, doesn’t allow anyone to travel very far from their homes.) But some of us aren’t obeying, or have to travel for specific reasons. And what about folks who have gotten the virus and haven’t gotten sick? Should they be allowed to travel with some sort of document or (as Bill Gates has suggested, a digital signature)?
 This page on Wikipedia (while I don’t like citing them, folks seem to be keeping the page updated) lists more than a dozen countries where have apps deployed. India has multiple app deployments from various state agencies. There are also apps available in China, Israel, Norway, Ghana, the Czech Republic and Australia. You should take a look at the various links and make your own comparisons.
This page on Wikipedia (while I don’t like citing them, folks seem to be keeping the page updated) lists more than a dozen countries where have apps deployed. India has multiple app deployments from various state agencies. There are also apps available in China, Israel, Norway, Ghana, the Czech Republic and Australia. You should take a look at the various links and make your own comparisons.
What should you do? In many places, you don’t have much choice, particularly if you recently returned home from outside the country. For those of us that have a choice, if you don’t like the idea, then don’t install any of these apps, and when the phone operating systems update over the summer, remember to turn off the “contact tracing” setting. If any of you are active in the efforts cited here, please drop me a note, I would love to talk to you and learn more.

 Application security is the process of making apps more secure by finding, fixing, and enhancing the security of apps. Much of this happens during the development phase, but it includes tools and methods to protect apps once they are deployed. This is becoming more important as hackers increasingly target applications with their attacks.
Application security is the process of making apps more secure by finding, fixing, and enhancing the security of apps. Much of this happens during the development phase, but it includes tools and methods to protect apps once they are deployed. This is becoming more important as hackers increasingly target applications with their attacks.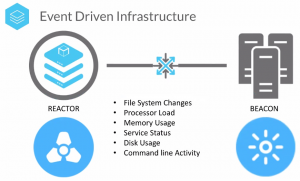
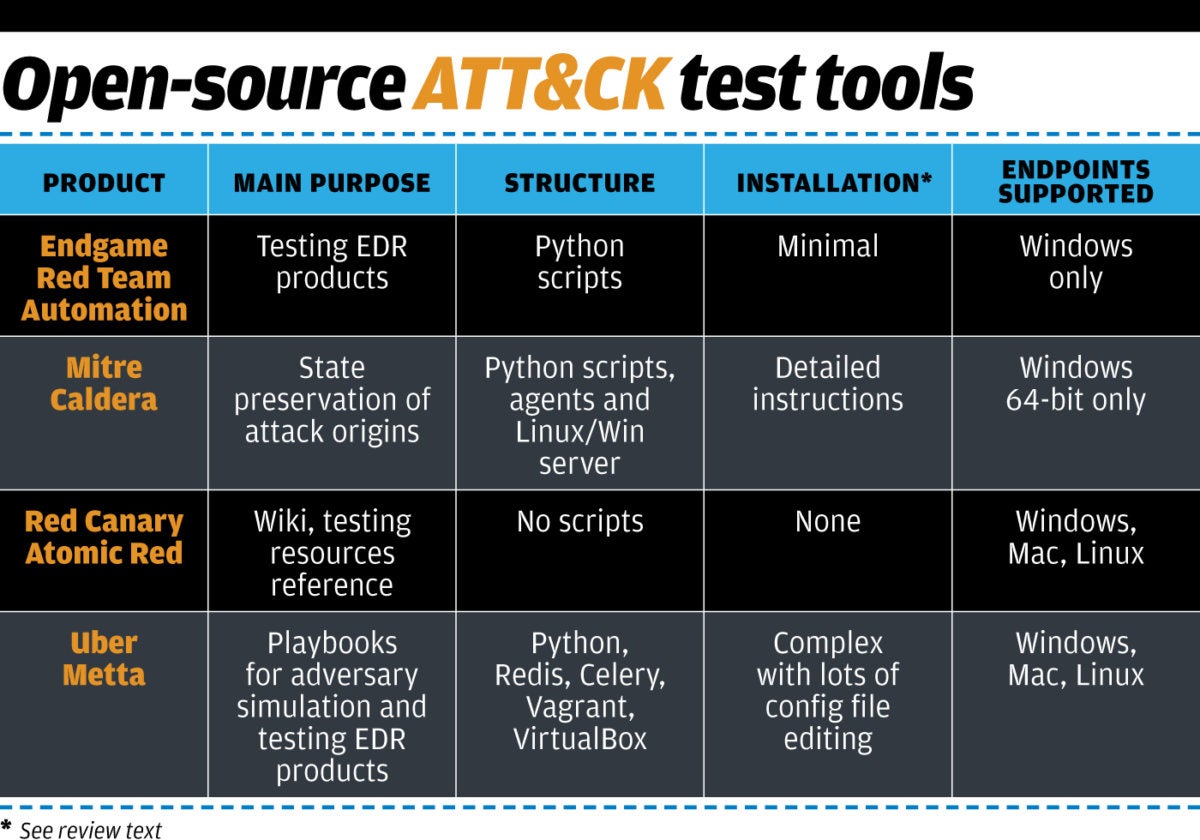 In an article that I wrote last week for CSOonline, I d
In an article that I wrote last week for CSOonline, I d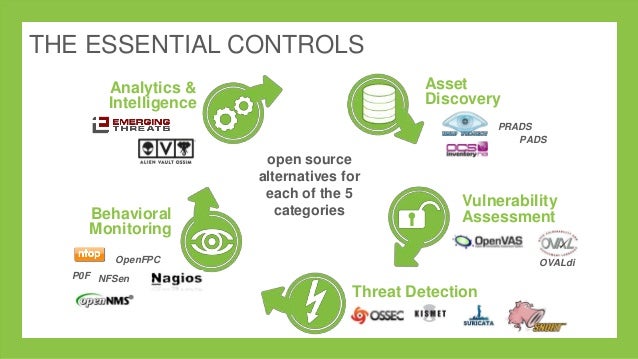 Times have certainly changed. Yes, software costs are still a factor, and while it is generally true that open source can save money, it isn’t the only reason nowadays to adopt it. While application deployment costs have risen, the direct software cost is a small part of the overall development budget, often
Times have certainly changed. Yes, software costs are still a factor, and while it is generally true that open source can save money, it isn’t the only reason nowadays to adopt it. While application deployment costs have risen, the direct software cost is a small part of the overall development budget, often