The online advertising world is undergoing a massive transition right now, trying to cope with an increasing technology war between the advertisers and us, the people that view their advertising. It is messy, it is contentious, and no one really knows what is going to happen in the coming months and years.
Recently, Facebook made changes to the way it works with displaying online ads. They say in that linked post, “We’ve all experienced a lot of bad ads: ads that obscure the content we’re trying to read, ads that slow down load times or ads that try to sell us things we have no interest in buying. Bad ads are disruptive and a waste of our time.”
Here is the problem: one person’s “bad” ad is another person’s opportunity to sell you something that maybe you might want. So they have attempted to clarify the issue, and give users more control over their ad experience. So far, it hasn’t been good.
How many of you Facebook users know about this page to control your ad preferences? I don’t see many hands being electronically raised. Take a moment, click on the above link, and spend a few minutes browsing around to see what they have done. You will be surprised.
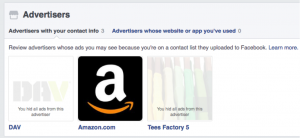
The page is full of confusing controls and has a really poor user experience. For example, as you can see from the screen shot, I have given my personal information to three different advertisers, two of whom that I didn’t recognize. When I deleted these two – because I don’t want to hear from them ever again – they first fade, before disappearing from view if I would return back to this page.
Andrew Bosworth, a VP at Facebook, says, “Some ad blocking companies accept money in exchange for showing ads that they previously blocked — a practice that is at best confusing to people and that reduces the funding needed to support the journalism and other free services that we enjoy on the web.” (my emphasis added) That is a lofty thought.
But let’s not just blame Facebook. At least they are trying to take control over the situation and make improvements, so that users will click on more relevant ads and they will be able to charge more for them. How about the traditional news generators, like newspapers and other media companies? What are they doing about online ads?
The short answer is that they are selling every square pixel they can and finding new ways to pop-up, pre-roll, roll over, mix sponsored and editorial content, and in general pollute the overall browsing experience of their online properties. Just about every publication that I want to read places some obstacle (and that is what I think about them) in my way when I try to click on an article that I want to read. Their home pages automatically start playing noisy videos that have me using the mute button on my PC as a default setting, just so I can have some peace and quiet when I am reading in the mornings.
I know, they have to make money. Print advertisers are leaving in droves, subscribers are few and far between, and newsrooms are ghost towns.
So a few years ago, technology comes to the rescue and creates browser plug-ins called ad blockers. These sense pop-ups and other devious methods, and prevent them from displaying ads. It is a great idea, and most modern browsers have incorporated some of their features too.
However, the problem is the blockers worked too well. So Facebook and other major sites who benefit from advertising revenue have decided to block the blockers. Now we have a cat-and-mouse game, where as one side adds new features, the other side figures out a way around them. Malware authors have been doing this for decades.
“More publishers will have to look to more innovative ways to incorporate their commerce with their content.” So says TechCrunch, who ran this story not too long ago. They proposed a sensible argument for how ad blockers can improve the overall experience and at least eliminate the cheesy online ads. But what is happening is that innovation has turned into just using as many ways as possible to put up online ads.
The pre-eminent ad blocking company is called Ad Block Plus. On their blog, they announced a new version of their software that is used by hundreds of millions of users. It is called “Acceptable Ads Platform.” Basically, they get to choose which ads are “good” and which aren’t. They will continue to block the bad ads, but allow good ads by default. You can change this setting and not allow any ads whatsoever.
The New York Times has said, “instead of blocking bad ads, AdBlock allowed ads it deemed acceptable to be seen, often for a price.” This strikes me as something we used to call “bait and switch.” The Ad Block Plus company now wants to be known as a “web customizing” company. This seems a bit naïve, or misleading, or both. It also puts this company in the hot seat to decide what is acceptable and what is not. They claim to be putting together a panel of judges. We’ll see how well that will work.
As I said, this is all early days for what will come. While the web has been with us for decades, and online advertising too, it seems we need to work together to figure out how to best serve up ads that won’t block the editorial content that we were trying to view and still allow the publishers and media companies to make money from our interests. So far, it is sub-optimal for nearly everyone involved.
To hear more about this matter, listen to our latest podcast from Paul Gillin and I where we discuss this issue. Or leave your comments here.
 The first decision you need to make in your smart home journey is selecting the right ecosystem. By ecosystem, I mean the voice-activated smart hub that is used to deliver audio content from the Internet (such as news, weather, and answers to other queries) as well as the main interface with a variety of other smart home devices, such as lighting, thermostats and TVs. In this review I look at two of the three main hubs from Google (the white-topped taller unit on the right) and Amazon (the smaller black unit on the left) and how they stack up.
The first decision you need to make in your smart home journey is selecting the right ecosystem. By ecosystem, I mean the voice-activated smart hub that is used to deliver audio content from the Internet (such as news, weather, and answers to other queries) as well as the main interface with a variety of other smart home devices, such as lighting, thermostats and TVs. In this review I look at two of the three main hubs from Google (the white-topped taller unit on the right) and Amazon (the smaller black unit on the left) and how they stack up. Today I begin a series of reviews in Network World around smarter home products. Last year we saw the weaponized smart device as the
Today I begin a series of reviews in Network World around smarter home products. Last year we saw the weaponized smart device as the  Back in the early 2000’s, I
Back in the early 2000’s, I Today, the issue of digital equity is receiving more attention than ever. For good reason; Internet access is no longer a luxury, it is a daily necessity in how we live, work and play. Still, we are far from the
Today, the issue of digital equity is receiving more attention than ever. For good reason; Internet access is no longer a luxury, it is a daily necessity in how we live, work and play. Still, we are far from the  The researchers from Ben Gurion University in Israel describe how an attacker could
The researchers from Ben Gurion University in Israel describe how an attacker could