I wrote this piece with Greg Matusky, the head of the Gregory FCA agency.
As a marketer of a security firm, you know that surveys can serve as high-impact marketing tools when shared with clients, used to power top-of-the-funnel lead gen campaigns, punch up sales literature, incorporated into white papers, and create great content for any number of channels.
But when it comes to gaining media attention for your survey, well, that can be a struggle. The media is inundated with corporate-funded surveys and often turn a jaundiced eye to them precisely because of their inbred biases.
Gaining exposure in the media or by having the results “go viral” on social media requires you to create surveys that deliver results that withstand media scrutiny. But these surveys also must meet the definition of what is new, what is newsworthy, and what is interesting to an audience eager to better understand the changing world of cybersecurity. Above all, you need to put away your marketer’s hat and assume a reporter’s perspective in order to create results welcomed, not ignored by the media.
If you would rather listen than read, check out this podcast episode that Paul Gillin and I did about surveys, from our FIR B2B series.
Here’s what you need to know.
Man Bites Dog. Findings should be unexpected, counter-intuitive, unusual, or all three.
Having a survey that repeats common wisdom is a sure way for reporters to instantly hit the delete key.
This Barracuda survey found that 74 percent of respondents stated that security concerns restrict their organization’s migration to the public cloud and have prevented widespread cloud adoption. So tell me something new! The results might have been news back in 2000, but not now. A great survey breaks new ground. It adds to the common knowledge and doesn’t just repeat it. Push your organization to formulate questions that produce the unexpected, counter-intuitive findings that media love.
Bigger is Better!
Sample sizes need to be big enough to impress – and be meaningful. Sample sizes of a few hundred participants, based on some non-random selection, such as people filling out a SurveyMonkey form, isn’t going to cut it. You can’t fool the media. They want statistical validity and the credibility that comes from large sample sizes.
Want a prime example? Consider Kaspersky Lab and B2B International release of a survey that drew on 5,000 companies of all sizes from 30 countries. Now that carries heft, and indeed, the results were cited in several places, including that the average cost of a data breach for enterprise businesses in North America is $1.3M. Another survey from Bitdefender interviewed 1,050 IT professionals in several countries to find out their cloud security purchase decisions. Both of these surveys are keepers.
Compare those surveys to a Beyond Trust study of nearly 500 IT professionals and concluded the “5 Deadly Sins” within organizations that ultimately increase the risks of a data breach. Yes, that will be conclusive – not. You are cherry picking the results here for sure.
But sample size isn’t enough. Take for instance a recent survey conducted by One Identity. It asked 900 IT security professionals for their thoughts. Seems like a promising sample size. But the results talk about inadequate IT processes around user access by disgruntled former employees and other nefarious actors — providing a widespread opportunity to steal usernames and passwords, risking the infiltration of their entire IT network. That brings us to our next point.
Blind them with science!
Make sure you ask the right evidence-based questions. Many surveys focus on “soft” assessments, such as “Do you believe your cybersecurity is better/worse this year when compared to last year?” Can anyone really answer that question with hard facts? Probably not. To win media coverage, show the reporters the evidence behind the questions, or ask for specific information that can be based on more than just a “feeling.” As an example of what not to do: “Most organizations are worried that the technical skills gap will leave them exposed to security vulnerabilities,” which is from a Tripwire survey.
Here is another result from that same Tripwire survey that doesn’t really have any solid data behind it: “Seventy-nine percent believe the need for technical skills among security staff has increased over the past two years.” Where did they get their beliefs from?
And then there is this survey from ABI Research, which finds that 40% of respondents believe that data security is the leading barrier to adopting innovative technologies. Again, how did the participants rank their beliefs and come up with this conclusion? This survey says nothing.
Consider the source of the discontent.
Sometimes having surveys come from surprising places, such as academic researchers, is a sexy way to interest media. Third parties make the findings more newsworthy and citable. Here is a report about the relative security of swiping patterns versus a six-digit PIN code that was done for the US Naval Academy. They surveyed more than a thousand people to find out that “shoulder surfers” (busybodies who look over our shoulders at crowded places) can remember the swipe patterns better than the numeric PINs. It also provides an unexpected result too. Could your organization team with a similarly credible third party to tell its story?
The best surveys use data that isn’t easily available.
Data such as server logs or actual threat data that show particular trends is useful and notable. Many security vendors now report on data from their own networks, using their monitoring tools that track what is actually being observed “out in the wild.” There is no belief system required: This is cold, hard data. The king of these kinds of surveys is the Verizon Data Breach Investigations Report, which has been coming out for the past decade. This report examines the actual attacks and isn’t asking for anyone’s opinion or feelings. It is encyclopedic, comprehensive, thoughtful, and analytical. Because it has been around for so long, the analysts can pull together trends from its historical records. And, at least until Verizon was itself breached, the data came from a solid brand too.
As you can see, there are some surveys that are worthwhile. The best ones take time and cost money to pull off properly. But they are worth it in terms of great media coverage.
 The hijacking legitimate but obscure Windows services is a tough exploit to detect. Here are two lesser known Windows services that could be vulnerable to malware attacks. You might think you can tell the difference between benign and malicious Windows services, but some of these services are pretty obscure. Do you know what ASLR and BITS are? Exactly.
The hijacking legitimate but obscure Windows services is a tough exploit to detect. Here are two lesser known Windows services that could be vulnerable to malware attacks. You might think you can tell the difference between benign and malicious Windows services, but some of these services are pretty obscure. Do you know what ASLR and BITS are? Exactly.
 Minitel? That French videotext terminal thing from the 1980s and 1990s? Didn’t that die an ignominious death from the Internet? Yes, that is all true. But for its day, it was ahead of its time and ahead of today’s Internet in some aspects too. You’ll see what I mean when you consider its content and micropayments, network infrastructure, and its hybrid public/private ownership model. Let’s dive in.
Minitel? That French videotext terminal thing from the 1980s and 1990s? Didn’t that die an ignominious death from the Internet? Yes, that is all true. But for its day, it was ahead of its time and ahead of today’s Internet in some aspects too. You’ll see what I mean when you consider its content and micropayments, network infrastructure, and its hybrid public/private ownership model. Let’s dive in.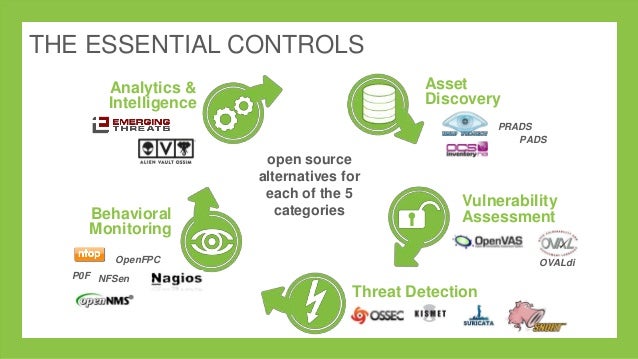 Times have certainly changed. Yes, software costs are still a factor, and while it is generally true that open source can save money, it isn’t the only reason nowadays to adopt it. While application deployment costs have risen, the direct software cost is a small part of the overall development budget, often
Times have certainly changed. Yes, software costs are still a factor, and while it is generally true that open source can save money, it isn’t the only reason nowadays to adopt it. While application deployment costs have risen, the direct software cost is a small part of the overall development budget, often 
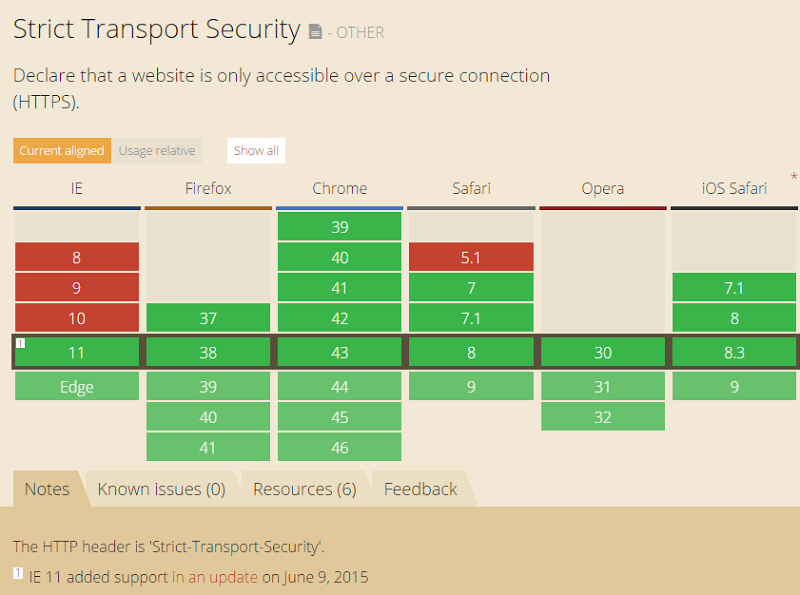
 Israel is becoming a major center for connected car research. Fueled by government-backed military research, test labs established by automakers and numerous connected car startups, the country has attracted top talent from around the world and provided innovative technologies in
Israel is becoming a major center for connected car research. Fueled by government-backed military research, test labs established by automakers and numerous connected car startups, the country has attracted top talent from around the world and provided innovative technologies in 
 I haven’t used a bank ATM for years, thanks to the fact that I usually don’t carry cash (and when I need it, my lovely wife normally has some handy). I still remember one time when I was in Canada and stuck my card in one of the cash machines, and was amazed that Canadian money was dispensed. I was amazed at how the machine “knew” what I needed, until I realized that it was only loaded with that currency.
I haven’t used a bank ATM for years, thanks to the fact that I usually don’t carry cash (and when I need it, my lovely wife normally has some handy). I still remember one time when I was in Canada and stuck my card in one of the cash machines, and was amazed that Canadian money was dispensed. I was amazed at how the machine “knew” what I needed, until I realized that it was only loaded with that currency.