I was watching a fascinating movie on Amazon called All In. It documents voting suppression history in the US. While we have had various laws, including several Constitutional amendments, their implementation is mostly a local matter. Some local officials have done what they can to deny the vote over the years. For the most part, the documentary is accurate. It features numerous interviews with Stacey Abrams, who lost the Georgia governor’s race in 2018.
I was watching a fascinating movie on Amazon called All In. It documents voting suppression history in the US. While we have had various laws, including several Constitutional amendments, their implementation is mostly a local matter. Some local officials have done what they can to deny the vote over the years. For the most part, the documentary is accurate. It features numerous interviews with Stacey Abrams, who lost the Georgia governor’s race in 2018.
The movie comes at an interesting time. In my blog post for Avast this week, I summarize many of the voter suppression efforts that we have seen in the past several years, including leading up to the 2016 and 2018 national elections. There was a lot of data on suppression collected by Mueller. His report showed that more than 3,500 ads on Facebook were placed by the Russian Internet Research Agency to try to convince potential Black voters to stay home during the 2016 elections. The same group also posted a series of anti-Muslim ads and organized concurrent protest rallies in Texas on opposite political sides. My Avast post has more details on the recent suppression efforts seen this year.
There are efforts to try to encourage everyone to vote, including a major ad spend by a new non-profit group called National Council on Election Integrity.
In the Amazon All In documentary, one person suggests the 2016 efforts should be called “Jim Crow v2.0,” referencing the pre-60s laws (and more recent changes) that made voting difficult by instituting literacy tests and poll taxes. You can see some archived examples of 1960s-era literacy tests here. These tests are almost impossible to pass, even f you have a graduate degree in American Studies.
I want to take things a step further: I think we are now in the Jim Crow v3.0 era. The new literacy test is the result of a confusing series of mail-in and absentee ballot regulations and shifting court challenges that are now happening across our country. My wife and I voted via mail-in ballots in Missouri: it took a lot of re-reading the various instructions, figuring out the steps involved, getting our ballots notarized and then mailed in. Each ballot has to be returned in a matching envelope and is tagged with a QR code that you can scan to check on its progress, to ensure that the elections board received it. (They did.) A good resource is what the Washington Post has put together that tells you when and how you can vote in your state.
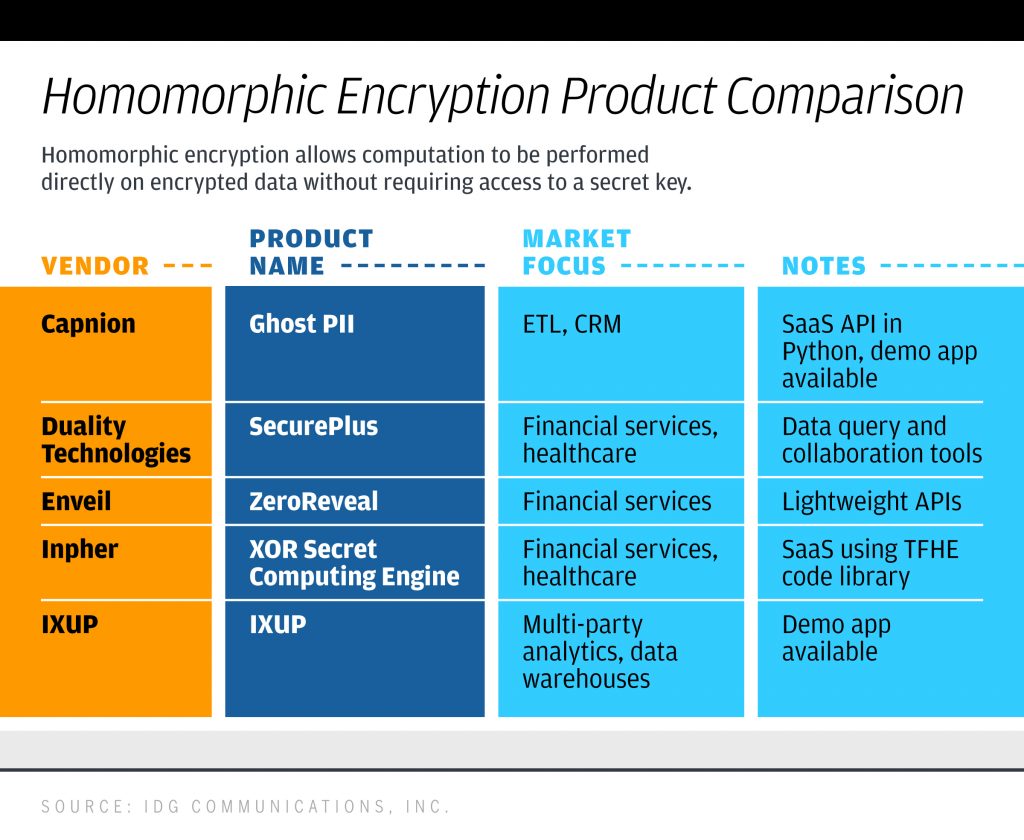
But there is a subtle difference between mail-in (which anyone in Missouri can do) and absentee (which you have to certify that you aren’t going to make it to the polls). They have different deadlines and other requirements. For my Avast blog, I got to talk directly to Trevor Timmons, the CIO for the Colorado Department of State, the agency that supervises its elections. In its June 2020 primary, more than 99% of registered voters submitted mail-in ballots. Colorado is one of those “universal” mail-in states, meaning that every registered voter will receive a mail-in ballot. You can come and vote in person, but most people don’t. You can also register and vote on election day, something only a few states have.
After I had mailed in our ballots, I had a senior moment where I thought I swapped my ballot and put it in my wife’s return envelope, and vice-versa. Timmons told me that they specifically look out for these situations and still validate both ballots: “It is a common error that takes manual intervention to resolve, but it is resolved quickly.”
What about fraud with mail-in votes? If you examine this page from the Heritage Foundation, you can see their dashboard of fraud has found 1,300 cases. That sounds like a lot but not when you compare that with the hundreds of millions of votes cast. Timmons is more worried about election security, and has put a series of measures in place, such as MFA required for all election judge since 2013), applying current software patches and using other endpoint detection tools to stop malware attacks. “We have seen ransomware incidents in some of our counties that compromised other agencies. We detected them when the attacks attempted to move to the elections boards and we were able to stop their spread.”
Meanwhile, October hasn’t been without its election systems hiccups. Voter registration systems were overwhelmed in Florida. Georgia’s electronic voting machines had some issues on the first days of early in-person voting, and Virginia’s and Pennsylvania’s online registration systems were both down thanks to a construction crew cutting a fiber cable and a systems crash in a data center, respectively.
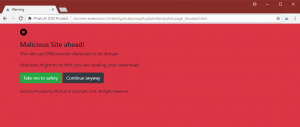 When the Internet was first created, it was based on using Roman alphabet characters in domain names. This is the character set that is used by many of the world’s languages, but not all of them. As the Internet expanded across the globe, it connected countries where other alphabets were in use, such as Arabic or Mandarin.
When the Internet was first created, it was based on using Roman alphabet characters in domain names. This is the character set that is used by many of the world’s languages, but not all of them. As the Internet expanded across the globe, it connected countries where other alphabets were in use, such as Arabic or Mandarin.