(This article originally appeared in the newsletter of the St. Louis Publishers Assn. It is part of a speech that I gave in July 2018 about marketing books by self-publishers.)
The most important phase of writing your book has nothing to do with the actual act of writing. It is in finding the right people who will promote the book to the world and turn potential readers into your buyers.
Back in the old days, before the Internet became popular, book authors hired publicists to promote authors, get them booked on talk shows and for book tours. They still exist, but there are other paths towards promotions. And what is good is that you can largely do much of this work on your own, if you have some self-promotional skills. The biggest part of that is in understanding how social media influencers work. (Here is a link to start your research.)
These influencers are the people that have the right kinds of followers in their networks. And they can become very powerful allies in your book marketing plan, and the cost to use them is pretty much just your time, and tenacity.
So how do you find these folks? The first thing is looking at your own social media networks, and making a list of the people that would be relevant to the topic of your book. What, you don’t have many friends on your networks? Now is the time to get busy friending people, and seeking out folks that could become pathways to promotion. You don’t need thousands of names, but you do need to approach this task on a regular basis, and friend new people every day. For those of us who are introverts, this can be painful, and can run counter to our instincts to hide behind our computer screens. Try to fight this, and reach out to people across your neighbors, your work colleagues, your church or other social organizations, and so forth.
One thing you don’t want to do is to buy lists of names. While this is certainly possible, you don’t know the quality of the names you are getting, and chances are many of these names aren’t going to be helpful to your book promotion anyway. Save your money.
Next, figure out the keywords that describe your audience, topic, focus, and what they are interested in and why they would buy your book. This means using these keywords to do many Google searches. Many means hundreds. Sometimes, you want to combine two or three keywords to be more effective.
 Next, pick your social media network where your audience will hang out. If your book has a visual component, then stick with Pinterest or Instagram. If you have news-related content, Twitter. If it is general interest fiction, Facebook. Business-related topics, LinkedIn. These aren’t hard and fast choices, and feel free to experiment with more than one social network if you have the time. This doesn’t mean you need to craft a separate collection of Tweets, Pinterest Pins, etc. In fact, you can share announcements across multiple social networks. A good tool to do this is Hootsuite (shown here).
Next, pick your social media network where your audience will hang out. If your book has a visual component, then stick with Pinterest or Instagram. If you have news-related content, Twitter. If it is general interest fiction, Facebook. Business-related topics, LinkedIn. These aren’t hard and fast choices, and feel free to experiment with more than one social network if you have the time. This doesn’t mean you need to craft a separate collection of Tweets, Pinterest Pins, etc. In fact, you can share announcements across multiple social networks. A good tool to do this is Hootsuite (shown here).
While you are doing all of this, you should settle on your book title and domain name for your book’s website. Yes, you need a website. Part of that website should be an email newsletter, where you tell your potential readers what is going on with your book, so they can get involved in its writing and production. You should commit to writing one post every week in the months leading up to your book launch on your website. After all, you are a writer!
Next, start collecting email addresses from your social media connections and use them to populate an email list. There are plenty of low-cost web hosting providers out there, and plenty of choices with email server companies such as MailChimp, ConstantContact, SendGrid, and others. Many of these services have free plans if your list is small, so take advantage of them. You can send out a new email with a copy of each blog post to save time if you wish.
Finally, start thinking about collecting reviewers. There is an entire universe of Amazon influencers, but I won’t get into that here.Look at NetGalley, especially if you want to join the IBPA. This is a website that is used to promote new books to a list of active readers and reviewers. Good luck with your marketing!
 This week we take a trip down memory lane to discuss the highlights of our 60-some odd collective years of working as B2B journalists in the technology field. There are some great stories, such as Meeting Bill Gates (Paul at a press junket, David at an industry conference) and working with Greg Gianforte, now a member of Congress from Montana after making several fortunes starting technology businesses. Being a tech journalist has its risks: Charles Wang, when he was chairman of Computer Associates, campaigned to get Paul fired from Computerworld, but the two later became friends. David’s parody of Miss Manners got him a cease-and-desist letter from the columnist’s lawyers. We both recall what the introduction of the web did for our industry and our world back in 1994, and how quickly the publishing market changed as a result. David recalls with fondness his interaction with Bob Metcalfe, the inventor of Ethernet and
This week we take a trip down memory lane to discuss the highlights of our 60-some odd collective years of working as B2B journalists in the technology field. There are some great stories, such as Meeting Bill Gates (Paul at a press junket, David at an industry conference) and working with Greg Gianforte, now a member of Congress from Montana after making several fortunes starting technology businesses. Being a tech journalist has its risks: Charles Wang, when he was chairman of Computer Associates, campaigned to get Paul fired from Computerworld, but the two later became friends. David’s parody of Miss Manners got him a cease-and-desist letter from the columnist’s lawyers. We both recall what the introduction of the web did for our industry and our world back in 1994, and how quickly the publishing market changed as a result. David recalls with fondness his interaction with Bob Metcalfe, the inventor of Ethernet and 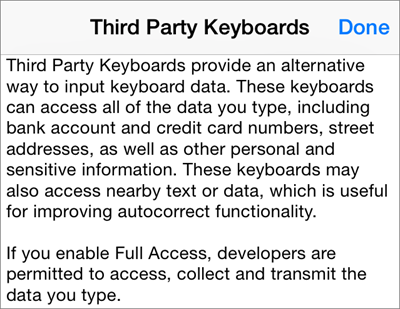 Here is the thing. In order to install one of these keyboard apps, you have to grant it access to your phone. This seems like common sense, but sadly, this also grants the app access to pretty much everything you type, every piece of data on your phone, and every contact of yours too. Apple calls this full access, and they require these keyboards to ask explicitly for this permission after they are installed and before you use them for the first time. Many of us don’t read the fine print and just click yes and go about our merry way.
Here is the thing. In order to install one of these keyboard apps, you have to grant it access to your phone. This seems like common sense, but sadly, this also grants the app access to pretty much everything you type, every piece of data on your phone, and every contact of yours too. Apple calls this full access, and they require these keyboards to ask explicitly for this permission after they are installed and before you use them for the first time. Many of us don’t read the fine print and just click yes and go about our merry way.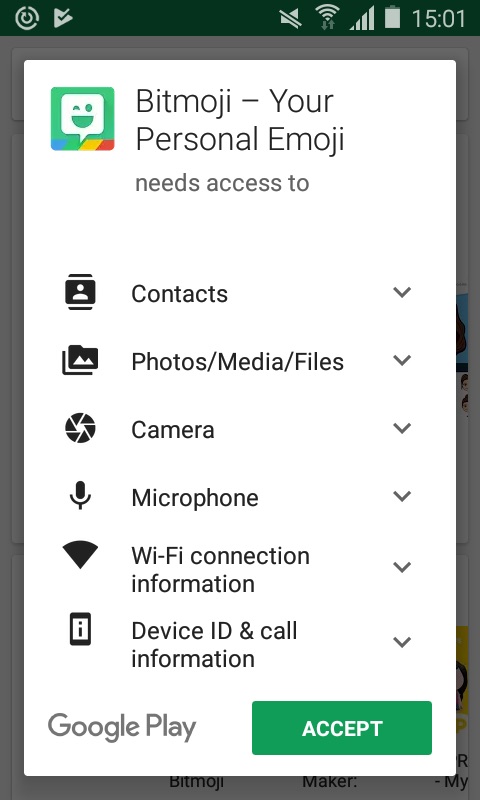 On Android phones, the permissions are a bit more granular, as you can see in this screenshot. This is actually just half of the overall permissions that are required.
On Android phones, the permissions are a bit more granular, as you can see in this screenshot. This is actually just half of the overall permissions that are required.

 The world has changed significantly in the past two years, and so have the rules around assessing cyber security risk. A combination of greater digital business penetration, a wider array of risks, and bigger consequences of cyber threats have made the world of risk management both more complex and more important than ever. Sadly, word hasn’t yet gotten out that risk management is an essential part of today’s business operations. According to this
The world has changed significantly in the past two years, and so have the rules around assessing cyber security risk. A combination of greater digital business penetration, a wider array of risks, and bigger consequences of cyber threats have made the world of risk management both more complex and more important than ever. Sadly, word hasn’t yet gotten out that risk management is an essential part of today’s business operations. According to this 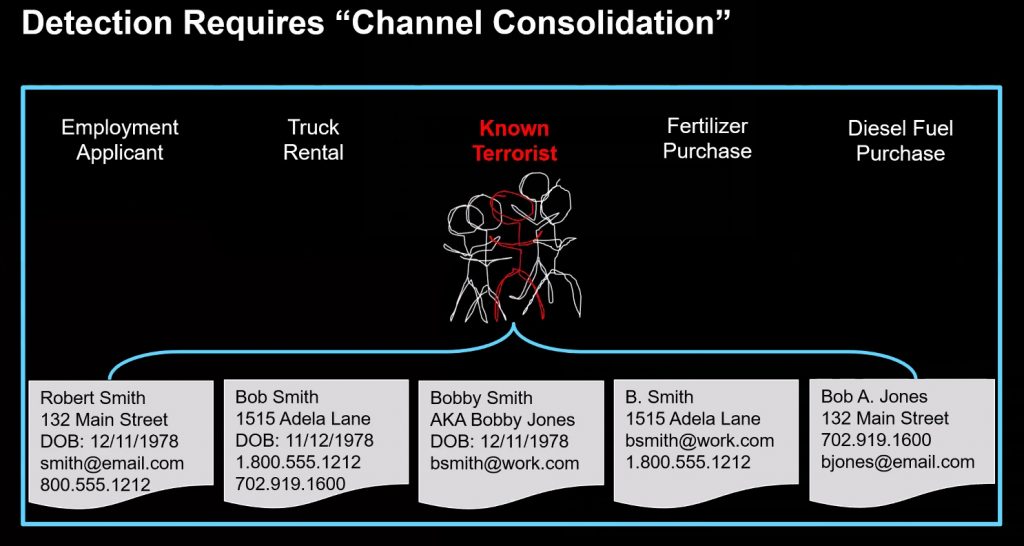
 Jonas started working on this many years ago at IBM. He is trying to disrupt the entity resolution market and eventually spun out Senzing with his tool. The goal is that you have all this data and you want to link it together, eliminate or find duplicates, or near-duplicates. Take our criminal, who is going to rent a truck, buy fuel oil and fertilizer, and so forth. He does so using the sample identities shown at the bottom of the graphic. Senzing’s software can parse all this data and within a matter of a few minutes, figure out who Bob Smith really is. In effect, they merge all the different channels of information into a single, coherent whole, so you can make better decisions.
Jonas started working on this many years ago at IBM. He is trying to disrupt the entity resolution market and eventually spun out Senzing with his tool. The goal is that you have all this data and you want to link it together, eliminate or find duplicates, or near-duplicates. Take our criminal, who is going to rent a truck, buy fuel oil and fertilizer, and so forth. He does so using the sample identities shown at the bottom of the graphic. Senzing’s software can parse all this data and within a matter of a few minutes, figure out who Bob Smith really is. In effect, they merge all the different channels of information into a single, coherent whole, so you can make better decisions.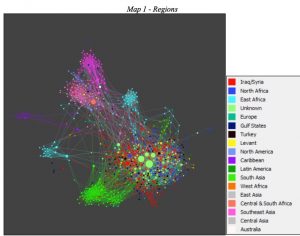
 Why isn’t marketing attracting more college grads? That’s the topic Paul Gillin and I explore this week, starting with the results of a study commissioned by
Why isn’t marketing attracting more college grads? That’s the topic Paul Gillin and I explore this week, starting with the results of a study commissioned by