If you want to completely cut the cable cord, it isn’t easy. I have been waiting for technology to become spousal-ready, and we are still about a year or two away. Today you have a lot of choices in the $40/month range that rival what the cable companies offer you for TV programming. The trouble is you have to make a choice between user interface and great TV resolution: you can’t yet have something that delivers both, other than your cable company.
I pay AT&T Uverse $125/mo. for my TV programming. That includes two receivers, one of which is a DVR and a boatload of various taxes and fees. Is it worth it to move to one of the online TV providers and save $85 a month? Eventually, I decided no, after trying two services, You Tube TV and Hulu Live TV. You can follow along with this column if you are brave enough: both offer a free trial of their services for a week, after which the monthly subscription starts. There are other services; my patience wore thin after experimenting with these two however.
Let’s first look at the user interface and mindset of the two online providers. You can obtain your TV programming in one of two ways: either by selecting your shows using a channel via your web browser or via an app that runs on your TV equipment. The web browser has the better UI because the developers working at the providers have more to work with and are more used to building web apps these days. And, you have a real keyboard for input, unlike your TV where you have to navigate around an on-screen one that can be infuriating.
 So how do you get the audio and video signals from your computer to your living room TV? Two ways: either by connecting your computer directly to your TV with an HDMI cable or using one of several devices like Google’s Chromecast that does this for you wirelessly. If you use the direct cable connection from your computer, you will have to figure out a wireless keyboard and mouse to control it. If you use Chromecast, you will have to figure out the sequence of controls using the three apps that Google has (Google’s Chrome browser, Google Home and the Chromecast app itself) to get it setup. The workflow isn’t immediately obvious, and I suggest you learn the process before bringing your spouse into the room for the demo.
So how do you get the audio and video signals from your computer to your living room TV? Two ways: either by connecting your computer directly to your TV with an HDMI cable or using one of several devices like Google’s Chromecast that does this for you wirelessly. If you use the direct cable connection from your computer, you will have to figure out a wireless keyboard and mouse to control it. If you use Chromecast, you will have to figure out the sequence of controls using the three apps that Google has (Google’s Chrome browser, Google Home and the Chromecast app itself) to get it setup. The workflow isn’t immediately obvious, and I suggest you learn the process before bringing your spouse into the room for the demo.
The nice thing about Chromecast is that any content that is displayed in a browser tab can be quickly transmitted to your TV by clicking a few buttons. I say a few: my wife got immediately weary of the process when I showed her what was involved. Your own experience may be similar. The bad thing about Chromecast is that the resolution is poor: nowhere near HD quality and even below SD video quality. Even if you have an old living room TV (and mine is more than five years old), you will be disappointed with the Chromecast video quality. And by the way, Google sells two different versions of Chromecast: one is for audio only; the other is for video and comes with the HDMI connector. Make sure you buy the right one.
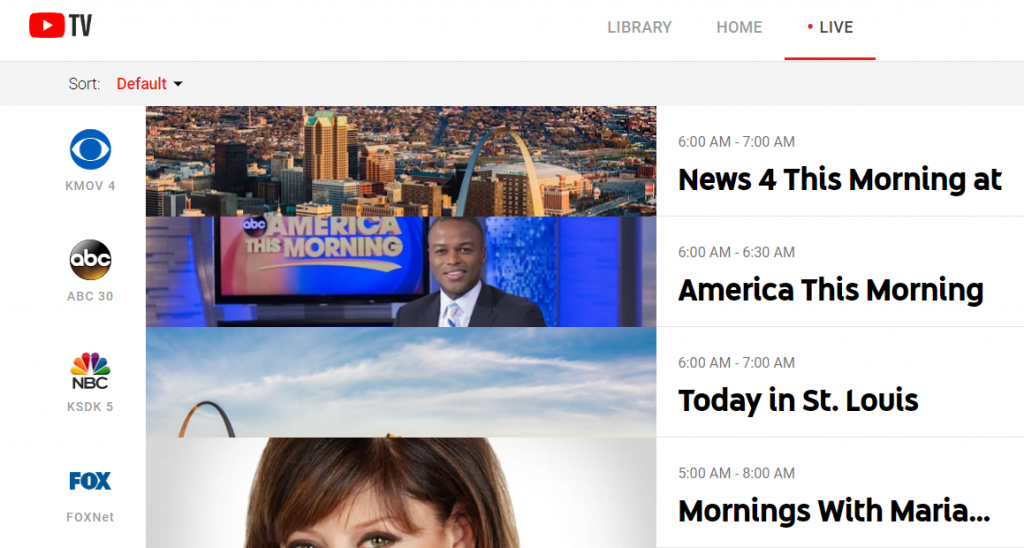 Another difference is how you access TV shows that have previously aired. Hulu’s web UI is very akin to the Amazon and Netflix web UI. In order to get the entire season’s worth of episodes, you have to click on the name of the show in the “My Stuff” guide. You can’t reorder the shows listed. If you click on the video itself, you are taken to the current episode. You Tube TV lists each episode as separate videos, much like the way ordinary You Tube does for its videos. (You can see the web version of the live TV guide above.)
Another difference is how you access TV shows that have previously aired. Hulu’s web UI is very akin to the Amazon and Netflix web UI. In order to get the entire season’s worth of episodes, you have to click on the name of the show in the “My Stuff” guide. You can’t reorder the shows listed. If you click on the video itself, you are taken to the current episode. You Tube TV lists each episode as separate videos, much like the way ordinary You Tube does for its videos. (You can see the web version of the live TV guide above.)
So far I have only talked about using the web clients of You Tube and Hulu. There is a second method, which uses the native apps that run on your TV equipment. If you have a new TV, chances are it comes with apps for a variety of video providers, including Amazon, Netflix, You Tube and Hulu. I tried the apps that ran on my Samsung Blu-ray player: it didn’t have a You Tube app, again because it was more than five years old.
Sadly, there are UI differences between what you see with your web browser and the TV-based app clients, with the TV apps being far less capable than their web cousins. One big difference is how the onscreen channel or movie guide is shown. Netflix has the longest experience with developing its apps, and there are major interface and stability differences between its Android, iOS, web and embedded TV apps. On my Samsung device, the Netflix app frequently can’t find the Internet, or just quits working entirely. On the web client, that rarely happens.
Like Netflix, You Tube TV and Hulu both allow you to segregate your family’s preferences, so you can keep track of your individual tastes and what you have already watched. You Tube allows up to six different family members. Hulu is more restrictive and confusing, and there is also an unlimited extra-cost option.
Speaking of extra cost options, this is where the two providers are showing their relative youth. If you don’t want to watch live TV programming, Hulu has plans that start at $8/mo., or $12/mo. if you want to skip most commercials. If you want everyone to watch different streams concurrently, that will cost another $15/mo. There are also premium channel fees for HBO, Showtime and Cinemax. You Tube TV has Fox Sports, Starz, AMC, Sundance and Showtime premium add-on channels.
Finally, Hulu with Live TV doesn’t support viewing live TV streams on all of its devices, according to this very confusing webpage. I read over the caveat several times and didn’t really understand what they were saying.
Alright, let’s move on to discussing the real benefit with using the TV apps from the online providers (or Blu-ray player, in my case). Your video quality will be as good as anything else you run on the TV, full HD. But you have to put up with a sub-par UI to get it.
So, what should you do? First, if you are in the market for a new TV, sign up for at least one of the online TV providers before you go shopping, and set up a simple temporary login password too. Go to your store and login to your provider, using the embedded app on the TV, and see for yourself if the UI is going to give you fits in selecting your programming with a couple of sets that you are interested in. If you really want a true A/B test, buy a Chromecast and bring that along with your laptop and see what the resolution will be if you don’t believe me.
If you just bought a TV within the last couple of years, try my experiment at home and see if you get better results that I did with my tests. The apps could be better than I experienced. If you have a large family and many different TV sets scattered throughout your home, you will probably end up sticking with your cable provider.
 This week we talk about new ways that machine learning and artificial intelligence can benefit marketing organizations. While these three news items are all different aspects of this technology, they show collectively how these new technologies are changing the way marketing is done.
This week we talk about new ways that machine learning and artificial intelligence can benefit marketing organizations. While these three news items are all different aspects of this technology, they show collectively how these new technologies are changing the way marketing is done. Organizations are becoming increasingly digital in their operations, products and services offerings, as well as with their business methods. This means they are introducing more technology into their environment. At the same time, they have shrunk their IT shops – in particular, their infosec teams – and have less visibility into their environment and operations. While they are trying to do more with fewer staff, they are also falling behind in terms of tracking potential security alerts and understanding how attackers enter their networks. Unfortunately, threats are more complex as criminals use a variety of paths such as web, email, mobile, cloud, and native Windows exploits to insert malware and steal a company’s data and funds.
Organizations are becoming increasingly digital in their operations, products and services offerings, as well as with their business methods. This means they are introducing more technology into their environment. At the same time, they have shrunk their IT shops – in particular, their infosec teams – and have less visibility into their environment and operations. While they are trying to do more with fewer staff, they are also falling behind in terms of tracking potential security alerts and understanding how attackers enter their networks. Unfortunately, threats are more complex as criminals use a variety of paths such as web, email, mobile, cloud, and native Windows exploits to insert malware and steal a company’s data and funds. So how do you get the audio and video signals from your computer to your living room TV? Two ways: either by connecting your computer directly to your TV with an HDMI cable or using one of several devices like Google’s Chromecast that does this for you wirelessly. If you use the direct cable connection from your computer, you will have to figure out a wireless keyboard and mouse to control it. If you use Chromecast, you will have to figure out the sequence of controls using the three apps that Google has (Google’s Chrome browser, Google Home and the Chromecast app itself) to get it setup. The workflow isn’t immediately obvious, and I suggest you learn the process before bringing your spouse into the room for the demo.
So how do you get the audio and video signals from your computer to your living room TV? Two ways: either by connecting your computer directly to your TV with an HDMI cable or using one of several devices like Google’s Chromecast that does this for you wirelessly. If you use the direct cable connection from your computer, you will have to figure out a wireless keyboard and mouse to control it. If you use Chromecast, you will have to figure out the sequence of controls using the three apps that Google has (Google’s Chrome browser, Google Home and the Chromecast app itself) to get it setup. The workflow isn’t immediately obvious, and I suggest you learn the process before bringing your spouse into the room for the demo.
 What should you use? I use my own hosted WordPress site, and it is a good tool to learn anyway, since many sites now employ it themselves. You can
What should you use? I use my own hosted WordPress site, and it is a good tool to learn anyway, since many sites now employ it themselves. You can 

 There are some clients that just can’t seem to help themselves and have to rewrite almost everything from top to bottom. To avoid getting trapped in these situations, you need to be crystal clear about how your work will be treated once it leaves your computer. Some clients think they are better writers than you, others want to show to their bosses that they have added value to your work.
There are some clients that just can’t seem to help themselves and have to rewrite almost everything from top to bottom. To avoid getting trapped in these situations, you need to be crystal clear about how your work will be treated once it leaves your computer. Some clients think they are better writers than you, others want to show to their bosses that they have added value to your work. These efforts have been known for some time: Motherboard ran a story in April 2016, and then came out in
These efforts have been known for some time: Motherboard ran a story in April 2016, and then came out in 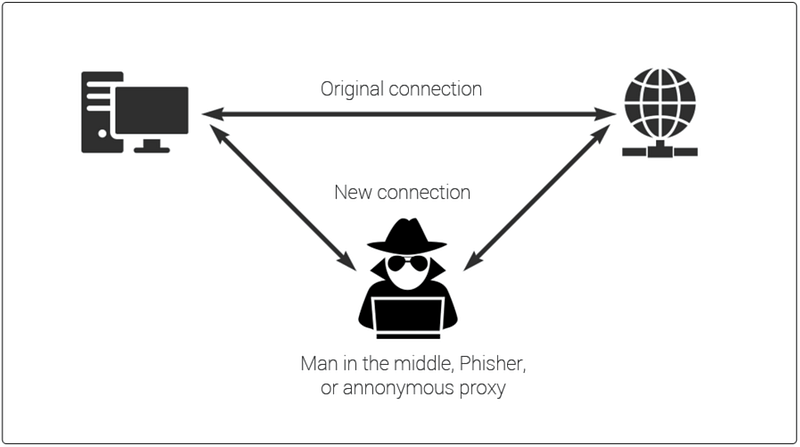 Email is inherently insecure. Sorry, it has been that way since its invention, and still is. All of us don’t give its security the attention it needs and deserves. So if you got one of these messages, or if you are worried about your exposure to a future one, I have a few suggestions.
Email is inherently insecure. Sorry, it has been that way since its invention, and still is. All of us don’t give its security the attention it needs and deserves. So if you got one of these messages, or if you are worried about your exposure to a future one, I have a few suggestions.