I am very fortunate: I have worked for myself for decades and have a great collection of clients that keep me busy with plenty of freelance writing assignments. But because our economy is in rough shape, there are lots of folks who are out of work right now. This made me think back to the time in 2006 when I got fired from my last full-time gig, running the editorial operations of the various Tom’s Hardware websites.
It wasn’t the first time I went to work and was told to pack up my things and leave that same day. It is a horrible feeling: you think you are worthless, that you will never work again. That you have failed. I was scared that I wouldn’t be able to make my mortgage payments. I had moved across the country to take that job, and now what was I going to do?
Unlike the astronauts, failure is an option. I wrote about this many years ago, where I described some of my numerous failures in my career, such as my books that didn’t sell or websites that weren’t successful at attracting interest.
 I thought of this because I am reading an interesting book by Lauren Herring, Take Control Over Your Job Search. It is all about helping you to find a new job — not that I need to or want to make changes to my current situation mind you. I am very happy with being a full-time freelancer, and thankful that I can work for such great clients. But if you are less fortunate, or if you know someone who has gotten stuck with unemployment, this book might be worth picking up. Lauren is the CEO of a coaching/recruitment firm here in St. Louis.
I thought of this because I am reading an interesting book by Lauren Herring, Take Control Over Your Job Search. It is all about helping you to find a new job — not that I need to or want to make changes to my current situation mind you. I am very happy with being a full-time freelancer, and thankful that I can work for such great clients. But if you are less fortunate, or if you know someone who has gotten stuck with unemployment, this book might be worth picking up. Lauren is the CEO of a coaching/recruitment firm here in St. Louis.
Sure, there are a lot of job-search books out there. This book has some intersections with three sources: that seminal job searching book What Color is Your Parachute, Elisabeth Kubler-Ross‘ stages of grief and the mindfulness work by Jon Kabat-Zinn. But what I found interesting in Herring’s book is that she addresses the biggest issue of today’s unemployed: your emotional state of mind. Yes, you can fill out all of the Parachute’s exercises and have a sparkling resume. You can meditate daily and figure out whether you are in denial or still bargaining with your newfound unemployment. But if you approach your virtual interviews with a lack of confidence, or too much confidence, or can’t even leave your house without a boatload of fear, you won’t get anywhere. “The ability to notice, understand, and process your emotions is more critical to success and happiness today more than ever before,” she writes.
Herring describes how to respond to ten different emotions (that’s the multi-step Kubler-Ross stuff) of grief, anger, and frustration with ways to respond to them and Parachute-style exercises to get you to discover your own state of mind and ways that you can move through the paralysis towards more positive outcomes (a la mindfulness). Along the way you will be using a group of what she calls your “super team” of supporters to help you role play and arrive at better outcomes and write journal entries of your reactions. “The goal of this book is to replicate the live experience of working with a career coach as best as possible,” she writes.
Take fear, for example.To fight it, she cites several case studies of the jobless that she or her company has coached. “Potential employers can sense your fear about your job search,” which as you might imagine doesn’t bode well to get callbacks or offers. And if you find yourself taking rejection personally and feeling resentful, you need to reset these feelings. For example, you should do some research and find out if you have your facts straight.
One of the more interesting aspects is shaping your personal brand, which is something that I have written about several times, and part of some of my own career coaching presentations. Your brand needs to come through in all your digital elements: LinkedIn profile, your resume and so forth. “This is one of the most uplifting tactics your can do during your job search,” she writes, and a good way to counter some of the negative emotions you are experiencing. Being clear on your brand is a great way to define your next job, and to ensure that your performance once you get that job will measure up to the expectations of you and your manager too. It is great advice for folks who have jobs and want to move ahead too.
One missing element from this book is some specific strategies in these times when we are working from home. While some of her methods can be easily modified and she does mention things like virtual interviews, I think the topic deserves its own special chapter. Perhaps she’ll include this on her website as a supplement.
 In this blog post for Avast, I review what is going on with election security since we last covered the topic during the March primaries. There have been numerous events in the past week that have brought new context to the intersection of technology and our elections. And I also mention several presentations given at Black Hat and DEFCON that bring us up to date on what is happening with election security.
In this blog post for Avast, I review what is going on with election security since we last covered the topic during the March primaries. There have been numerous events in the past week that have brought new context to the intersection of technology and our elections. And I also mention several presentations given at Black Hat and DEFCON that bring us up to date on what is happening with election security. We all know that phishing and email spam are the biggest opportunity for hackers to enter our networks. If a single user clicks on some malicious email attachment, it can compromise an entire enterprise with ransomware, cryptojacking, data leakages or privilege escalation exploits. Over the years a number of security protocols have been invented to try to reduce these opportunities. This is especially needed today, as more of us are working from home and need all the email protection we can muster. In my l
We all know that phishing and email spam are the biggest opportunity for hackers to enter our networks. If a single user clicks on some malicious email attachment, it can compromise an entire enterprise with ransomware, cryptojacking, data leakages or privilege escalation exploits. Over the years a number of security protocols have been invented to try to reduce these opportunities. This is especially needed today, as more of us are working from home and need all the email protection we can muster. In my l Late last month, security researchers
Late last month, security researchers  I thought of this because I am reading an interesting book by Lauren Herring,
I thought of this because I am reading an interesting book by Lauren Herring, 
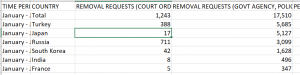
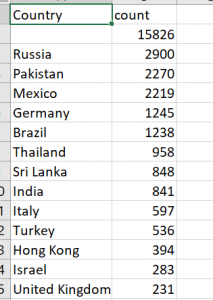 Facebook has a similar spreadsheet, and Russia tops their list, but Turkey is in the top 15. Here are
Facebook has a similar spreadsheet, and Russia tops their list, but Turkey is in the top 15. Here are  Now that more of us are working from home (WFH), one of the key technologies that can cause problems is surprisingly our networked printers. Hackers target these devices frequently, which is why many IT departments have taken steps to prevent home laptops from connecting to them.
Now that more of us are working from home (WFH), one of the key technologies that can cause problems is surprisingly our networked printers. Hackers target these devices frequently, which is why many IT departments have taken steps to prevent home laptops from connecting to them. 