I have been reading David McCullough’s books on the Wright brothers and the building of the Brooklyn Bridge. Both give a very vivid picture of what the life of an engineer was more than a century ago. This life was a very different one from what we know of today. What fascinates me about how both the Wright brothers and the Roeblings (first John, then his son Washington, the engineers behind the bridge) that built things back in the day. Let’s look into their toolsets, their work habits, and their thinking processes.
First and foremost for both situations was the power of observation. Wilbur Wright spent countless hours watching how birds flew, and then tried to figure out a collection of materials that could mimic them. Within a decade people were building airplanes out of paper and wood, what we would consider mere toys today. But using some of those early calculations enabled us to build 747s and SR-71s that fly fast and are built with very advanced materials. And are anything but toys, to be sure.
Second was understanding your materials. The Wright flyer worked because it was extremely light and flexible. The Brooklyn Bridge worked because it was heavier than previous bridges: that it could withstand and distribute the loads properly. The bridge is still in great shape, more than 100 years later. We tear down lesser structures after a decade.
Washington Roebling spent his days watching his bridge being built from a nearby house. He was severely injured from getting a bad case of the bends before anyone knew what this was. Perhaps this could be the first attributed case of remote work, although the distance was covered using a telescope rather than a VPN, Slack and email. His father was also injured on the job from a ferry accident and dies shortly thereafter. All four men got in the middle of things and spent lots of hands-on time to refine their calculations and their drawings and their builds.
About those calculations. We are talking about basic math, using pencil and paper. We tend to forget how easy it is to revise things now that we have powerful computers that can instantly spot grammatical or coding errors and even suggest changes as we type. Back in those days, it was a lot more work and required often starting from scratch.
The slide rule was about as fancy as things got back then, something that I used when I first began my college education. When I went to grad school in the late 1970s, computers were still the size of rooms. Look at the evolution of IBM, from making those roomfuls of computers to changing the desktop world with its PC business, which was eventually sold to a Chinese company. Now IBM is a software and services company.

The first airplanes and bridges were built in the era before electricity. If you ever have an opportunity to visit the Detroit area, you should see the actual bicycle shop that the Wrights used to machine their parts. It isn’t recognizable because it ran on steam power, with these long leather belts that rotated the equipment. Now we think nothing of plugging something into the wall, and complain if the cord isn’t long enough. (You might remember my post about the invention of the electric light bulb and other wonders on display at the Henry Ford Museum.)
Engineers are taught how to solve problems. What is interesting about the stories in both books is how the context of the problems is explained in clear language, with gripping narratives about the various lives involved and the decisions made. You are there with the Wrights on a desolate barrier island as they struggle to figure things out, or inside the bridge piers or watching the cables being strung across the river. They are tales that have stood the test of time.
One reason is that both these books (as well as a third one on the building of the Panama Canal) are extraordinarily researched and well-written. I really enjoyed watching this interview McCullough did with Librarian of Congress James Billington on another of his books, the first part devoted to his writing tips.
 MLB began using holograms back in 2001,
MLB began using holograms back in 2001,  Roughly a third of all connected devices have insecure defaults, such as no or weak password protection or poor software design, that make them ripe for exploits.
Roughly a third of all connected devices have insecure defaults, such as no or weak password protection or poor software design, that make them ripe for exploits. Last week, an 18-year old hacker used social engineering techniques to compromise Uber’s network. He compromised an employee’s Slack login and then used it to send a message to Uber employees announcing that it had suffered a data breach.
Last week, an 18-year old hacker used social engineering techniques to compromise Uber’s network. He compromised an employee’s Slack login and then used it to send a message to Uber employees announcing that it had suffered a data breach. 
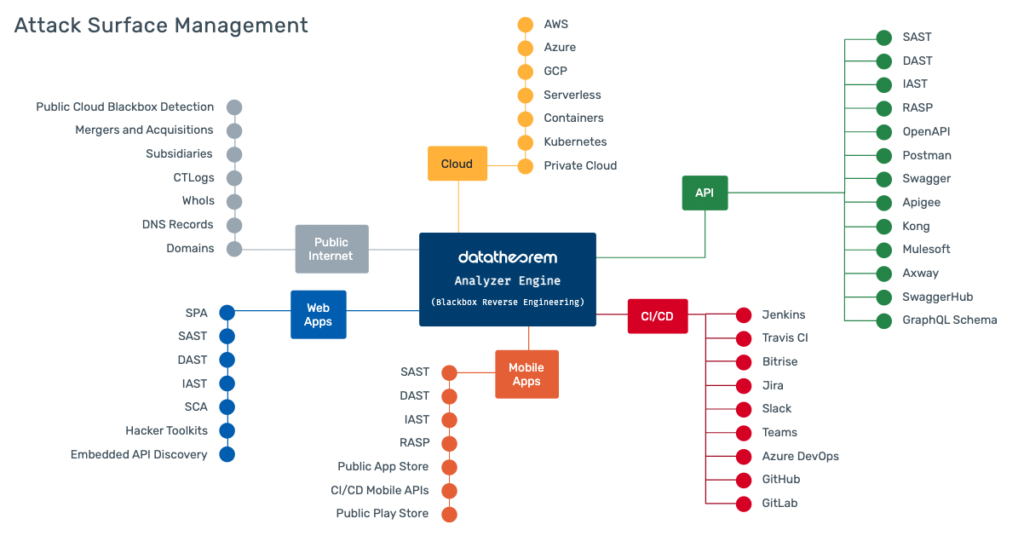
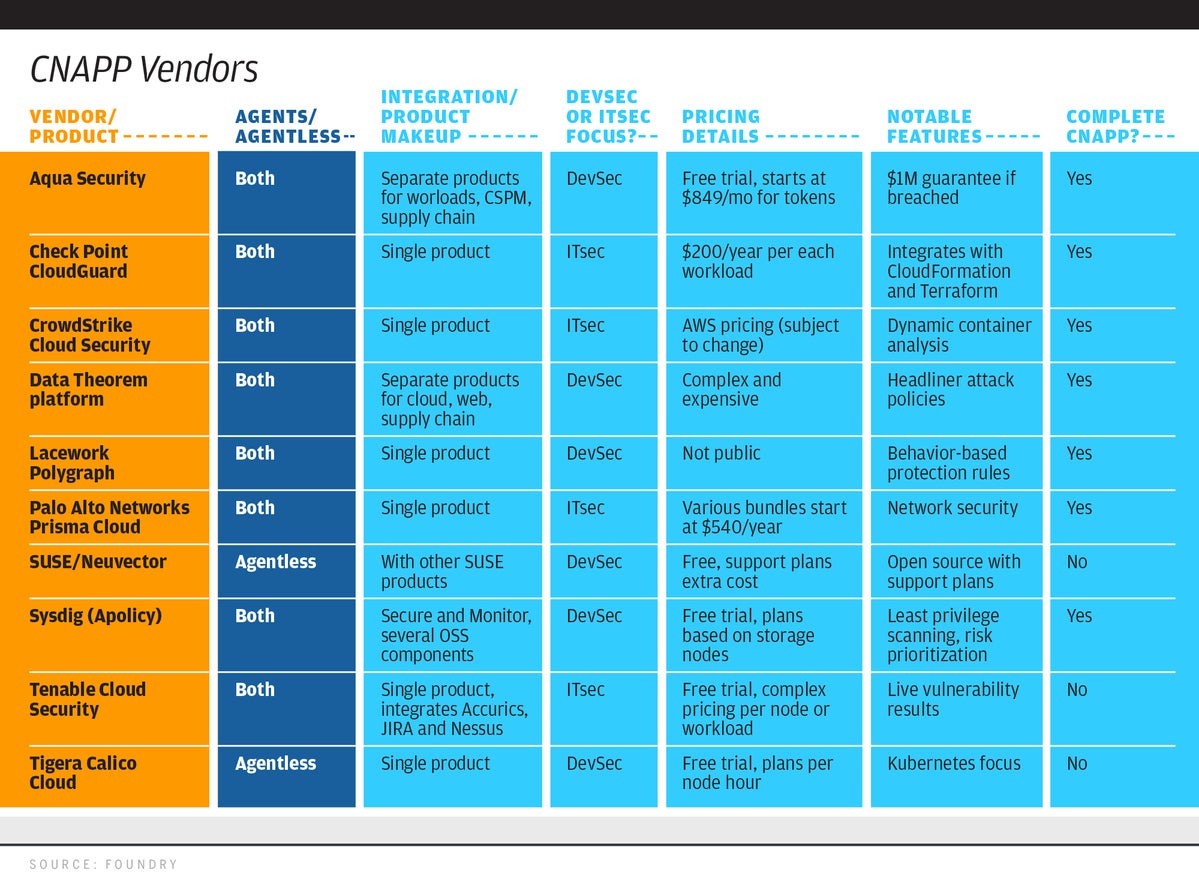 Even still, that is a lot of software to manage, integrate, and understand. However, almost none of the products that claim to be CNAPP have a full set of features that incorporate all four of these categories. In this
Even still, that is a lot of software to manage, integrate, and understand. However, almost none of the products that claim to be CNAPP have a full set of features that incorporate all four of these categories. In this