 This novel by William Landay has plot points that approach numerous other thrillers — such as the missing title character in Gone Girl — but takes things just a bit further in telling the tale of a missing mom who is presumed killed by her husband. You hear from various family members in the first person, but again it is done to introduce some interesting plot twists that I don’t want to spoil you with here. Initially I was a bit annoyed by the mixed narrator style but came to appreciate it about halfway through the novel. The narrative arc covers decades as we move way beyond the actual missing/murder conundrum and into the finer aspects of the children and other family members’ personalities, relationships, and whether they think the dad did the deed or not. Having the dad as a criminal defense lawyer is also a nice touch too!. Highly recommended.
This novel by William Landay has plot points that approach numerous other thrillers — such as the missing title character in Gone Girl — but takes things just a bit further in telling the tale of a missing mom who is presumed killed by her husband. You hear from various family members in the first person, but again it is done to introduce some interesting plot twists that I don’t want to spoil you with here. Initially I was a bit annoyed by the mixed narrator style but came to appreciate it about halfway through the novel. The narrative arc covers decades as we move way beyond the actual missing/murder conundrum and into the finer aspects of the children and other family members’ personalities, relationships, and whether they think the dad did the deed or not. Having the dad as a criminal defense lawyer is also a nice touch too!. Highly recommended.
How is that right to be forgotten going?
 The right to be forgotten isn’t part of the US Constitution, or for that matter in any other country’s founding documents. But it is part of the more recent regulations, which define how this data is collected, how it is processed, and mostly importantly, how and when it is erased. The phrase refers to where individuals can ask to have their personal data removed from various digital repositories under certain circumstances.
The right to be forgotten isn’t part of the US Constitution, or for that matter in any other country’s founding documents. But it is part of the more recent regulations, which define how this data is collected, how it is processed, and mostly importantly, how and when it is erased. The phrase refers to where individuals can ask to have their personal data removed from various digital repositories under certain circumstances.
It is not a new term. Indeed, the EU got going on this almost ten years ago, eventually enshrining rules in its General Data Protection Regulation (GDPR), which have been around now for almost five years. This motivated a few (and I emphasize very few — so far that number is five) states here in the US to enact their own privacy laws, including California’s Consumer Privacy Act (CCPA) and others that mention the “forgotten” rights. Here is a handy comparison chart of what the five states have passed so far.
Security blogger David Froud also wrote about the issue more than four years ago. He pointed out then that the term forgotten doesn’t necessarily mean total erasure of your data, such as the hypothetical case of a convicted criminal in applying for a job. But then, should the stain of that conviction follow someone for the rest of their life? Hard to say. And this is the problem with this right: the subtleties are significant, hard to define, and harder still to create a solid legal framework.
What got me thinking about this issue is a recent survey by Surfshark of the actual progress of the forgotten actions across European countries. They found that residents of France alone accounted for a quarter of the actions recorded by both Google and Microsoft’s search portals, with England and Germany residents together accounted for another quarter of cases. These requests are on the rise since the onset of Covid, and both Cyprus and Portugal have seen a 300% increase in requests since 2020. Interestingly, Estonia (which is a leader in implementing all sorts of other digital tech across the board) had the largest proportion of cases with 53 per 10,000 residents. Compare that to Bulgaria, which had 5.6 requests per 10,000 residents. At the bottom of the page linked above, you can see references to the various search portals’ request removal forms, and yes, you have to submit separate requests for each vendor (here is Google’s link). The EU “suggests” that the process from request to its fulfillment should take about a month, but the way they word it means there is no legal response time encoded in the GDPR. According to the Surfshark report, millions of requests have been filed since the law went into effect.
As the authors of the survey say, “Time will only tell which countries will join the fight for online privacy and to what ends our data is private online. Is the right to be forgotten a universal truth or a way to hide the past indefinitely?” I don’t honestly know.
Temper the Surfshark report with the results of a Spanish university research study that looked at the 500 most-visited websites in that country. They found a huge collection of tracking technologies that were hidden from any user consent, with less than nine percent of the sites actually obtaining any user consent.
But tech doesn’t stand still, and the right to be forgotten has taken on new meaning as the rise of AI chatbots such as ChatGPT that can seek out and find your personal data as a way to train their machine learning models. As my colleague Emma McGowen mentions in her Avast blog from last month, there is no simple mechanism to request removal of your data once the AI has found it online. You don’t know where your data is online, and even if you do there isn’t any simple form that you can fill out to request deletion.
Note: OpenAI released this opt-out form after I wrote this essay.
If you have ever tried to put a credit freeze on your accounts at the four major credit bureaus, you have some idea of the chore involved here. At least there are only four places that process your credit data. There are hundreds if not thousands of potential data collections that you would have seek out and try to get any action. Chances are your data is out there somewhere, and not just in Google’s clutches but on some hard drive running in some darker corner. Good luck tracking this down.
So where does that leave this right to privacy? It is a good sign that more countries and some US states are taking this seriously. But, each state has slightly different takes on what the right means and what consumers can do to remove their data. And for those you happily chatting up your AI bots, be careful about what private info you have them go searching for, lest you unwittingly add more data that you don’t want others to find about you.
FIR B2B PODCAST #158: ANNA GRIFFIN ON MARKETING IN UNCERTAIN TIMES

Anna told us about how marketers have to be careful not to let their organization appear to be a cost center. Rather, they should believe and demonstrate that they are a necessary and valuable asset to the company. Take advantage of a downturn by leaning in and focusing on customers so that the company can craft a message that’s more relevant to their needs. She suggested that marketers should fight for their budgets and focus on high-value activities that will help the company grow. “Someone has to grow, even in lean times,” she said.
Anna spoke about how she has embraced many of the tenets of B2C marketing, even though she has spent more of her career in the B2B world. “I believe that is true since the beginning of time; we are selling human-to-human after all.” Maybe we should start using the term H2H?
“We should remove any frictions in the purchasing process by understanding that community is the new B2B playbook and that customers want things now,” she said. The sales organization needs to be part of the marketing effort, and marketers should be sure playbooks are coordinated.
Being a market leader isn’t just about touting your company’s presence on some “magic quadrant” because customers don’t buy MQs, Anna said. “We have to show more specifics about how we can solve the actual customers’ problems. This means we have to be more targeted in how we can add value for them on day one.”
Book review: Who Will Accompany You by Meg Stafford

This book is the work of a mother’s separate travels with her two daughters: one visits Nepal and Bhutan, the other to Colombia. The two kids take the trips for specific reasons: to learn about total happiness and to work for an NGO that is helping with war-torn conflicts. The travels are enlightening for all parties concerned and are what Meg Stafford — who has written a regular column for years — says is an ongoing kaleidoscope of learning together with her daughters. She is a therapist, so her work listening and analyzing people comes through quite loudly in this memoir.
The travels aren’t your usual tourist romps through colorful foreign lands, but offer real insights into both the people they encounter along the way and the lessons they have learned about themselves and their own family relationships. “The more we know ourselves, the easier it is to connect with others, and the more connected we are with them,” she writes.
Regarding happiness, “the best way to predict it is to follow the example of someone who is currently where you will be in the future.”
There is also a lot describing problem-solving. “everything depends on how you use your mind. The way to solve the problems in your life is to open your heart to others.”
And this insight: “Parents cannot eliminate risk. We can shore up our children so that when they encounter it they can make better and more informed choices.
The women learn that tragedy is the same in any language, but humor doesn’t translate so easily, and there are lots of moments across this spectrum.
The title comes from answering the question about who we will accompany, not just in physical travel across the world but across our life. “We cannot always know but we can hold them close when they are near, so we can still hold them when they are far with arms outstretched.”
For those who enjoy memoirs and appreciate travel, this is a very appealing book.
Red Cross blog: Jim Gallagher and Hurricane Ian’s response
What skill does a retired journalist have in common with an American Red Cross disaster action team volunteer? This is not a rhetorical question: the two jobs both require you to listen to people carefully and be empathetic to their needs. This is the story about Jim Gallagher, who spent more than 27 years working for the St. Louis Post-Dispatch, mainly as a business reporter. “As a reporter you want to get people to open up to you, but that same skill in listening to people certainly helps when you are deployed. In both circumstances, you have to project sympathy,” he said. Both he and his wife have volunteered on a number of deployments. He responded to the aftermath of Hurricane Ian in central Florida last fall. Both helped out with those displaced by the California wildfires and helped ease the transition of unaccompanied minors crossing the southern border in 2021. In addition to his Red Cross activities, they also volunteer at a local food bank regularly.
You can read more about Jim and his volunteer activities on the Red Cross blog here.
Disinformation mercenaries for hire
In the past week I have seen a number of reports that range from unsettling to depressing. The reports document a three-pronged foundation of the darkest parts of the online world: disinformation, cyber-terrorism, and the difficulty in trying to craft better legal approaches to stop both.
Let’s start with the disinformation. A consortium of journalists from around the world wrote about a team of Israeli contractors (called “Team Jorge”) who claim to have covertly influenced more than 30 elections and placed stories to help improve the online reputations of numerous private business clients around the world. They did this by using hacking, sabotage and automated disinformation tools. Call it disinformation-mercenaries-for-hire. If this sounds familiar, it is another news product from the French-based ForbiddenStories group that broke the series of Pegasus-related stories back in the summer of 2021 that I have written about for Avast here. The group labels this effort “Story Killers” and you can read the various pieces here.
What is depressing is how adept this industry has become: by comparison, the Russian Internet Research Agency’s antics in meddling with our 2016 election looks crude and mere child’s play. The reporters uncovered a wide-ranging collection of automated tools to quickly create hundreds of fake social media accounts and generate all kinds of fake posts that are then amplified by the social networks and search engines. “We must be able to recount the life of the characters, their past, their personality,” said one mercenary. “When it’s a small agency, it’s done in a rather sloppy way. If it’s well done, it’s the Israelis.”
 The Israeli company behind these operations has a wide array of services, including digital surveillance, hack-and-leak smear campaigns, influence operations, and election interference and suppression. They claim to have operated for a decade.
The Israeli company behind these operations has a wide array of services, including digital surveillance, hack-and-leak smear campaigns, influence operations, and election interference and suppression. They claim to have operated for a decade.
One of the consortium partners is The Guardian and they document one of these automated systems that is used to manage a collection of social media avatars. Called AIMS, it allows for managing 30,000 seemingly real accounts to be created for nonexistent people. These can then be deployed either as a swarm – similar to a network of bots – or as single agents. Other tools are described in this piece by Haaretz.
The disinformation mercenaries sold access to their software to various national intelligence agencies, political parties and corporate clients interested in trying to resolve business disputes. Accounts span Twitter, LinkedIn, Facebook, Telegram, Airbnb, Gmail, Instagram and YouTube. Some of the identities even have Amazon accounts with credit cards and bitcoin wallets. All of this was leveraged to stage real-world events in order to provide ammunition for social media campaigns to provoke outrage.
Let’s move on to the cyberterrorism effort. Speaking about the Russians, also released this week are two reports from the Atlantic Council, a DC-based think tank that has studied the disinformation war the Russians have waged against Ukraine. (To be clear, this is completely independent of the Story Killers effort.) It is also depressing news because you realize that unlike an actual shooting war, there is never any time when you can claim victory. The totality, scope and power of this vast collection of fake news stories, phony government documents, deep fake videos and other digital effluvia is staggering and is being used by the Russians to convince both their own citizens and the rest of the world of Putin’s agenda.
And something else to worry about with the war comes from one final report, this one from Dutch intelligence forces that was covered here. The report says, “Before and during the war, Russian intelligence and security services engaged in widespread digital espionage, sabotage and influencing against Ukraine and NATO allies. The sustained and very high pressure that Russia exerts with this requires constant vigilance from Ukrainian and Western defenders.”
Taken together, you can see that disinformation has become weaponized in both the public and private sector. So what can be done? Cue up part three, which is trying to craft better laws to control these actions. Coincidentally, the US Supreme Court heard two cases that have been moving through our judicial system, Gonzalez v. Google and Twitter v. Taamneh. Both cases involve ISIS attacks. The former involves the 2015 murder in Paris of the 23-year old American student Nohemi Gonzalez, which I wrote about in a blog for Avast last fall. The latter involves the 2017 death of Nawras Alassaf in Istanbul. The first case directly involves the Section 230 statutes, the latter the various sections of the anti-terrorism act. Both were laws passed in the mid 1990s, when the internet was young and by comparison innocent.
You can read the transcriptions of the court’s oral arguments for Gonzalez here. The oral arguments transcript for Twitter are found here. I have taken the time to read them and if you are interested in my further thoughts, email me directly or post your questions here. Making effective changes to both laws won’t be easy without drastic consequences for how online companies run their businesses, and how we legitimately use them. And that is lesson from reading all these reports: as long as the bad guys can figure out ways to exploit these technologies, we will have to deal with some dire consequences.
CSOonline: What is the Traffic Light Protocol and how it works to share threat data
Traffic Light Protocol (TLP) was created to facilitate greater sharing of potentially sensitive threat information within an organization or business and to enable more effective collaboration among security defenders, system administrators, security managers and researchers. In this piece for CSOonline, I explain the origins of the protocol, how it is used by defenders, and what IT and security managers should do to make use of it in their daily operations.
Wreaking Havoc on cybersecurity
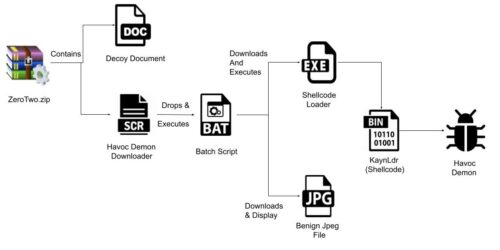 A new malware method has been identified by cybersecurity researchers. While it hasn’t yet been widely used, it is causing some concern. Ironically, it has been named Havoc.
A new malware method has been identified by cybersecurity researchers. While it hasn’t yet been widely used, it is causing some concern. Ironically, it has been named Havoc.
Why worry about it if it is a niche case? Because of its sophistication of methods and the collection of tools and techniques (shown in the diagram above from ZScaler) that it used. It doesn’t bode well for the digital world. Right now it has been observed targeting government networks.
Havoc is a command and control (C2) framework, meaning that it is used to control the progress of an attack. There are several C2 frameworks that are used by bad actors, including Manjusaka, Covenant, Merlin, Empire and the commercial Cobalt Strike (this last one is used by both attackers and red team researchers). Havoc is able to bypass the most current version of Windows 11 Defender (at least until Microsoft figures out the problem, then releases a patch, then gets us to install it). It is also able to employ various evasion and obfuscation techniques.
One reason for concern is how it works. Researchers at Reversing Labs “do not believe it poses any risk to development organizations at this point. However, its discovery underscores the growing risk of malicious packages lurking in open source repositories like npm, PyPi and GitHub.” Translated into English, this means that Havoc could become the basis of future software supply chain attacks.
In addition, the malware disables the Event Tracing for Windows (ETW) process. This is used to log various events, so is another way for the malware to hide its presence. This process can be turned on or off as needed for debugging operations, so this action by itself isn’t suspicious.
One of the common techniques is for the malware to go to sleep once it reaches a potential target PC. This makes it harder to detect, because defender teams can perhaps track when some malware entered their system but don’t necessarily find when it wakes up with further work. Another obfuscation technique is to hide or otherwise encrypt its source code. For proprietary applications, this is to be expected, but for open-source apps the underlying code should be easily viewable. However, this last technique is bare bones, according to the researchers, and easily found. The open source packages that were initially infected with Havoc have been subsequently cleansed (at least for now). Still, it is an appropriate warning for software devops groups to remain vigilant and to be on the lookout for supply chain irregularities.
One way this is being done is called static code analysis, where your code in question is run through various parsing algorithms to check for errors. What is new is using ChatGPT-like products to do the analysis for you and here is one paper that shows how it was used to find code defects. While the AI caught 85 vulnerabilities in 129 sample files (what the author said was “shockingly good”), it isn’t perfect and is more a complement to human code review and traditional code analysis tools.
25 years of ecommerce
In today’s post, I look back on the developments of ecommerce and my role in covering this technology. I was recently reminded of this history after writing last week about Paypal — this motivated one of you to recall events that happened in the early 2000s, back when the “internet bubble” was rising and then bursting.
I last took a long look back at ecommerce in 2014 with this blog post. In it I highlighted a series of other works:
- Back in the late 1990s, I tested many ecommerce products and also lectured at conferences around the world on the topic. One piece was an op-ed that I wrote for ComputerWorld back in 1999 here.
- In 2010, I looked at how hard it was to take credit card payments online in my blog.
- Then for ITworld in 2011, looking at the crop of mobile payment apps such as Square.
- And in 2013, I looked at the frustrations surrounding eWallet technology.
While the web came of age in the 1990s, it took a while for ecommerce to get into gear. The technologies were bare-bones: back then, you could learn basic HTML coding in a couple of days and easily put together a static series of web pages. The key operative words in that sentence were “static” and “basic.” The 1990s era of HTML was waiting for the language to catch up with what we wanted to do with it, but eventually the standards process got there. The real stumbling block was making a site dynamic and being able to support online inventories that were accurate, checkout pages that were secure, and having access to software interfaces that were pretty crude and simplistic. All of that required other tools outside of HTML, which is somewhat ironic. Now if you look at the code behind the average webpage, it is almost impossible to parse its logic at first glance.
Yet, here we are today with ecommerce being a very sophisticated beast. HTML is no longer as important as the accompanying and supporting constellation of web programming languages and development frameworks that require lots of study to be competent and useful. Connecting various databases and using a web front-end is both easier and more complex: the APIs are richer, but how they are implemented will require a deft touch to pull off successfully. Payment processing has numerous vendors that occupy sub-markets. (Stripe, Bill.com, and Klarna are three such examples of companies that are all involved in payments but have taken different pieces of the market.)
You might not have heard about Klarna: they are one of more than a dozen “buy now, pay later” services that pop up at checkout. No purchase is too small to be spread across a payment plan. Back in the pre-internet times, we had layaway plans that had one important aspect: you didn’t get the item until you completely paid for it. Now items arrive in days, but attached to a stream of loan payments stretching out several months. The downside is that there are potential late fees and 30% annualized interest charges too.
And then there is Amazon and Google. The former has both made it easier and more complex to do online shopping. It used to be both free and easy to return merchandise purchased on Amazon. Now it is neither. If you don’t pay attention when you are purchasing something, you could end up using one of their contract sellers, which complicates the returns process. And the cost of Prime continues to climb.
Google’s Lens technology has also transformed online shopping. If you have a picture of what you want to buy, you can quickly view what websites are selling the product with a couple of clicks on any Android or iPhone. My interior designer wife uses this tech all the time for her clients.
Before I go, I want to mention that Cris Thomas, known by his hacker handle Space Rogue, has a new book out that chronicles his rise into infosec security, including his time as one of the founders of the hacking collective L0pht. Its early days were wild by today’s standards: the members would often prowl the streets of Boston and dumpster dive in search of used computer parts. They would then clean them up and sell them at the monthly MIT electronics flea market. Dead hard drives were one of their specialties — “guaranteed to be dead or your money back if you could get them working.” None of their customers took them up on this offer, however. There are other chapters about the purchase of L0pht by @stake and Thomas’ eventual firing from the company, then taking eight years to get a college degree at age 40, along with the temporary rebirth of the Hacker News Network and going to work for Tenable and now at IBM. I review the book in this post, and highly recommend it if you are looking at reliving those early infosec days.
Book review: The exploits of Space Rogue (Cris Thomas)
![Space Rogue: How the Hackers Known As L0pht Changed the World by [Cris Thomas]](https://m.media-amazon.com/images/I/41OEoTKDqTL.jpg) The hacker Cris Thomas, known by his hacker handle Space Rogue, has a new book out that chronicles his rise into infosec security. I have interviewed him when I was writing for IBM’s Security Intelligence blog about his exploits. IBM’s X-Force has been his employer for many years now where he works for numerous corporate clients, plying the tools and techniques he refined when he was one of the founding members of the hacking collective L0pht.
The hacker Cris Thomas, known by his hacker handle Space Rogue, has a new book out that chronicles his rise into infosec security. I have interviewed him when I was writing for IBM’s Security Intelligence blog about his exploits. IBM’s X-Force has been his employer for many years now where he works for numerous corporate clients, plying the tools and techniques he refined when he was one of the founding members of the hacking collective L0pht.
My story covered his return visit to testify to Congress in 2018. Thomas and his colleagues originally testified there back in 1998. The book’s cover art shows this pivotal moment, along with the hacker handles shown as nameplates. The story of how this meeting came to pass is one of the book’s more interesting chapters, and the transcript of their testimony is included in an appendix too.
I also wrote this post about another member of L0pht named Mudge, during his time as a security consultant for Twitter. L0pht is infamous for developing a series of hacking tools, such as Windows NT password crackers (which Thomas goes into enormous detail about the evolution and enhancement of this tool) and a website called Hacker News Network. Thomas describes those formative years with plenty of wit and charm in his new book, which also serves as a reminder of how computer and network security has evolved — or not as the case may be made.
That cracking tool carried L0pht over the course of some twenty plus years. It began as “a small little piece of proof of concept code, hurriedly produced within a few weeks, and went from an exercise to prove a point, security weaknesses in a major operating system, to shareware, to a commercial success,” he writes.
One of his stories is about how L0pht had its first major penetration test of the Cambridge Technology Partners network. The company would go on to eventually purchase Novell and numerous other tech firms. The hackers managed to get all sorts of access to the CTP network, including being able to listen to voicemails about the proposed merger. The two companies were considering the acquisition of L0pht but couldn’t come to terms, and the hackers had left a backdoor in the CTP network that was never used but left on because by then their testing agreement had expired. Fun times.
The early days of L0pht were wild by today’s standards: the members would often prowl the streets of Boston and dumpster dive in search of used computer parts. They would then clean them up and sell them at the monthly MIT electronics flea market. Dead hard drives were one of their specialties — “guaranteed to be dead or your money back if you could get them working.” None of their customers took them up on this offer, however.
One point about those early hacking days — Thomas writes that the “naïveté of hackers in the late ’90s and early 2000s didn’t last long. Hackers no longer explore networks and computer systems from their parents’ basements (if they ever did); now it is often about purposeful destruction at the bequest of government agencies.”
He recounts the story of when L0pht members brought federal CyberCzar Richard Clarke to their offices in the 1990s. Clarke was sufficiently impressed and told Thomas, “we have always assumed that for a group or organization to develop the capabilities that you just showed us would take the resources only available to a state-sponsored actor. We are going to have to rethink all of our threat models.” Exactly.
There are other chapters about the purchase of L0pht by @stake and Thomas’ eventual firing from the company, then taking eight years to get a college degree at age 40, along with the temporary rebirth of the Hacker News Network and going to work for Tenable and now at IBM.
Thomas ends his book with some words of wisdom. “Hackers are not the bad guys. Most of the great inventors of our time, such as Alexander Graham Bell, Mildred Kenner, and Nichola Tesla, could easily be considered hackers. Criminal gangs who are running ransomware campaigns or are stealing credit cards are just that, criminals. They just happen to use a computer instead of a crowbar. They are not hackers, not to me anyway. L0pht’s message of bringing security issues to light and getting them fixed still echoes throughout the industry and is more important today than ever.” If you are at all interested in reading about the early days of the infosec industry, I highly recommend this book.