 The right to be forgotten isn’t part of the US Constitution, or for that matter in any other country’s founding documents. But it is part of the more recent regulations, which define how this data is collected, how it is processed, and mostly importantly, how and when it is erased. The phrase refers to where individuals can ask to have their personal data removed from various digital repositories under certain circumstances.
The right to be forgotten isn’t part of the US Constitution, or for that matter in any other country’s founding documents. But it is part of the more recent regulations, which define how this data is collected, how it is processed, and mostly importantly, how and when it is erased. The phrase refers to where individuals can ask to have their personal data removed from various digital repositories under certain circumstances.
It is not a new term. Indeed, the EU got going on this almost ten years ago, eventually enshrining rules in its General Data Protection Regulation (GDPR), which have been around now for almost five years. This motivated a few (and I emphasize very few — so far that number is five) states here in the US to enact their own privacy laws, including California’s Consumer Privacy Act (CCPA) and others that mention the “forgotten” rights. Here is a handy comparison chart of what the five states have passed so far.
Security blogger David Froud also wrote about the issue more than four years ago. He pointed out then that the term forgotten doesn’t necessarily mean total erasure of your data, such as the hypothetical case of a convicted criminal in applying for a job. But then, should the stain of that conviction follow someone for the rest of their life? Hard to say. And this is the problem with this right: the subtleties are significant, hard to define, and harder still to create a solid legal framework.
What got me thinking about this issue is a recent survey by Surfshark of the actual progress of the forgotten actions across European countries. They found that residents of France alone accounted for a quarter of the actions recorded by both Google and Microsoft’s search portals, with England and Germany residents together accounted for another quarter of cases. These requests are on the rise since the onset of Covid, and both Cyprus and Portugal have seen a 300% increase in requests since 2020. Interestingly, Estonia (which is a leader in implementing all sorts of other digital tech across the board) had the largest proportion of cases with 53 per 10,000 residents. Compare that to Bulgaria, which had 5.6 requests per 10,000 residents. At the bottom of the page linked above, you can see references to the various search portals’ request removal forms, and yes, you have to submit separate requests for each vendor (here is Google’s link). The EU “suggests” that the process from request to its fulfillment should take about a month, but the way they word it means there is no legal response time encoded in the GDPR. According to the Surfshark report, millions of requests have been filed since the law went into effect.
As the authors of the survey say, “Time will only tell which countries will join the fight for online privacy and to what ends our data is private online. Is the right to be forgotten a universal truth or a way to hide the past indefinitely?” I don’t honestly know.
Temper the Surfshark report with the results of a Spanish university research study that looked at the 500 most-visited websites in that country. They found a huge collection of tracking technologies that were hidden from any user consent, with less than nine percent of the sites actually obtaining any user consent.
But tech doesn’t stand still, and the right to be forgotten has taken on new meaning as the rise of AI chatbots such as ChatGPT that can seek out and find your personal data as a way to train their machine learning models. As my colleague Emma McGowen mentions in her Avast blog from last month, there is no simple mechanism to request removal of your data once the AI has found it online. You don’t know where your data is online, and even if you do there isn’t any simple form that you can fill out to request deletion.
Note: OpenAI released this opt-out form after I wrote this essay.
If you have ever tried to put a credit freeze on your accounts at the four major credit bureaus, you have some idea of the chore involved here. At least there are only four places that process your credit data. There are hundreds if not thousands of potential data collections that you would have seek out and try to get any action. Chances are your data is out there somewhere, and not just in Google’s clutches but on some hard drive running in some darker corner. Good luck tracking this down.
So where does that leave this right to privacy? It is a good sign that more countries and some US states are taking this seriously. But, each state has slightly different takes on what the right means and what consumers can do to remove their data. And for those you happily chatting up your AI bots, be careful about what private info you have them go searching for, lest you unwittingly add more data that you don’t want others to find about you.
 We are back after a hiatus and speaking to
We are back after a hiatus and speaking to 
 The Israeli company behind these operations has a wide array of services, including digital surveillance, hack-and-leak smear campaigns, influence operations, and election interference and suppression. They claim to have operated for a decade.
The Israeli company behind these operations has a wide array of services, including digital surveillance, hack-and-leak smear campaigns, influence operations, and election interference and suppression. They claim to have operated for a decade.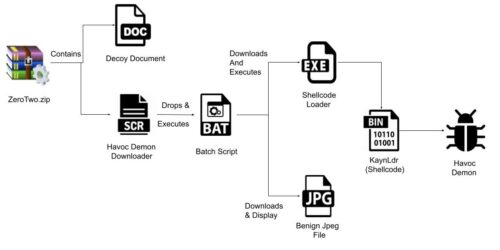 A new malware method has been identified by cybersecurity researchers. While it hasn’t yet been widely used, it is causing some concern. Ironically, it has been named Havoc.
A new malware method has been identified by cybersecurity researchers. While it hasn’t yet been widely used, it is causing some concern. Ironically, it has been named Havoc.![Space Rogue: How the Hackers Known As L0pht Changed the World by [Cris Thomas]](https://m.media-amazon.com/images/I/41OEoTKDqTL.jpg) The hacker Cris Thomas, known by his hacker handle Space Rogue, has
The hacker Cris Thomas, known by his hacker handle Space Rogue, has 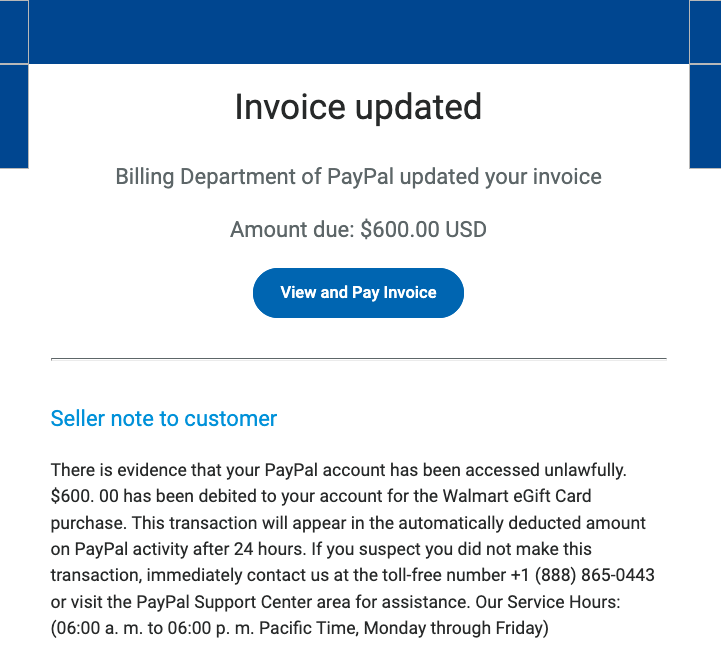 I have been a user of Paypal ever since, well, forever, but certainly for at least 25 years by my guess. Today I closed my account, thanks to having gotten several invoices from fraudsters. Today I got an invoice that I couldn’t delete. {“An error has occurred” … no kidding. I felt a great disturbance in the force.)
I have been a user of Paypal ever since, well, forever, but certainly for at least 25 years by my guess. Today I closed my account, thanks to having gotten several invoices from fraudsters. Today I got an invoice that I couldn’t delete. {“An error has occurred” … no kidding. I felt a great disturbance in the force.)