I have been testing some interesting devices to help you set up VPNs when you travel. By now most of you know not to connect to open WiFi access points, because your Internet traffic can be monitored, recorded, invaded, and used against you. The way to avoid these issues is to use a VPN. Until recently, you had a few different choices to install some software or bring your own VPN device. Both are more suitable for corporate networks, and aren’t all that easy to install and configure. These three devices attempt to make things easier for consumers. Sadly, they all aren’t quite up to the task.
- Webroot WiFi Security: $40/yr for up to three supported devices You can download the software here for Windows, Mac, iOS and Android devices.
- ButterflyVPN: $89, which supports up to ten devices. This includes a VPN subscription for three years, after which it will cost $2/mo.
- eBlocker: Starts at $99, includes three months of VPN service.
Both the Butterfly and eBlocker are small hardware devices. The Butterfly has a USB end that fits in any USB AC power adapter. The eBlocker is a cube two inches on a side with its own Ethernet and power cables to connect it up. The Webroot product is only software. You see I listed their prices above, and that is my first complaint: a consumer VPN should be priced transparently. Figuring out their prices shouldn’t take a combination of a CPA and a PI.
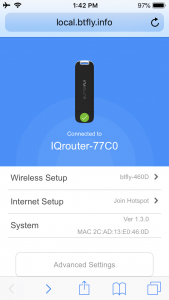 The appeal of the three products are their supposed ease of installation. However, I ran into problems on all of them. For example, the eBlocker is made in Germany, and the default menus are shown in German. If you want to change this to English menus, you have to learn enough German to navigate through the menu tree to find the switch to make this happen. The Butterfly (setup menu at left) is designed to operate with a simple open WiFi router. As you move about the world, you have to find and connect to one before you can establish your VPN connection. That is great, but you will have problems on other routers that aren’t completely open. For example, you’ll have issues if you connect to hotel or airport routers with captive wireless portals that require you to bring up a web form to acknowledge something. Also, there was no way to change the default password in any of its configuration menus, which seems like a major security shortcoming. The Webroot VPN was the easiest to install, since it was just software that runs in the background, but it had issues that I will get to below.
The appeal of the three products are their supposed ease of installation. However, I ran into problems on all of them. For example, the eBlocker is made in Germany, and the default menus are shown in German. If you want to change this to English menus, you have to learn enough German to navigate through the menu tree to find the switch to make this happen. The Butterfly (setup menu at left) is designed to operate with a simple open WiFi router. As you move about the world, you have to find and connect to one before you can establish your VPN connection. That is great, but you will have problems on other routers that aren’t completely open. For example, you’ll have issues if you connect to hotel or airport routers with captive wireless portals that require you to bring up a web form to acknowledge something. Also, there was no way to change the default password in any of its configuration menus, which seems like a major security shortcoming. The Webroot VPN was the easiest to install, since it was just software that runs in the background, but it had issues that I will get to below.
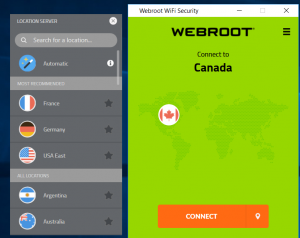 On all three, you can select various VPN endpoints for your traffic to appear to come from. At right, you can see how you can do this with Webroot, by clicking on the locations shown in the list. That has a lot of appeal — if it really worked as advertised. With eBlocker, you can also set up your Internet traffic thru the TOR network for even more privacy. I had issues with all of them when verifying the IP addresses with a public service, such as WhatisMyIP.com. They didn’t always consistently work, and despite conversations with each vendor, I couldn’t exactly tell you why.
On all three, you can select various VPN endpoints for your traffic to appear to come from. At right, you can see how you can do this with Webroot, by clicking on the locations shown in the list. That has a lot of appeal — if it really worked as advertised. With eBlocker, you can also set up your Internet traffic thru the TOR network for even more privacy. I had issues with all of them when verifying the IP addresses with a public service, such as WhatisMyIP.com. They didn’t always consistently work, and despite conversations with each vendor, I couldn’t exactly tell you why.
Webroot also allows you to select a particular VPN protocol (like IPsec or PPTP) if you need to connect to a corporate VPN. That is a nice touch.
All three also do more than just setup a VPN. Webroot does rudimentary content filtering. eBlocker can anonymize your originating IP address and block ads in your browsing sessions. It has this privacy discovery page where you can see what kind of information is being collected from your browser session, if you need reminding. Here is what its dashboard looks like:
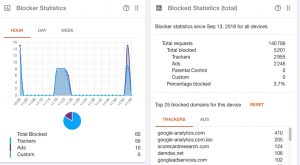 Blocking ads seems like a great idea, until you run into lots of websites that won’t deliver any content to you until you unblock them. As an example, my hometown newspaper doesn’t allow any visitors from EU countries because of potential GDPR liabilities. (That is probably a canard, but still.) There is a whitelist to add sites to try to get around this, but it didn’t seem to always function as intended.
Blocking ads seems like a great idea, until you run into lots of websites that won’t deliver any content to you until you unblock them. As an example, my hometown newspaper doesn’t allow any visitors from EU countries because of potential GDPR liabilities. (That is probably a canard, but still.) There is a whitelist to add sites to try to get around this, but it didn’t seem to always function as intended.
Using a VPN can also come in handy when you travel overseas and want to access content from the streaming video services. This is because the shows that we take for granted here in the US aren’t necessarily licensed for overseas viewing. For example, I was recently in Israel, where I was pleased to see that Amazon was streaming “The Man in the High Castle” but blocked just about every other one of their other original shows. However, none of the VPN services of the three devices would work reliably in this situation. And with Webroot’s VPN engaged, I couldn’t access any Netflix content whatsoever. It could be because of cookies set on my computer, or because of how I registered for the service, or it could be something else. The bottom line: if you want to securely access your content when you travel, you can’t depend on any of these devices.
And that is why I recommend you don’t buy any of these three items, at least until each vendor does a better job with fixing the issues I mentioned above. Consumer-grade VPNs are a great idea, especially if you travel frequently. But they are still a challenge, unless you have an IT department standing by to assist you when you run into snags on the road.
 There are more than 20 different coworking places in the St. Louis metro area where I live. I have been to many of them, even though I have my own dedicated office. Why? Because I want to be a part of the startup community and that is where many of them work. The spaces also are great meeting places.
There are more than 20 different coworking places in the St. Louis metro area where I live. I have been to many of them, even though I have my own dedicated office. Why? Because I want to be a part of the startup community and that is where many of them work. The spaces also are great meeting places.
 Eventually, I was diagnosed with
Eventually, I was diagnosed with  Your first to-do is to download all of your data that Facebook has on you. I wrote about this process earlier (and
Your first to-do is to download all of your data that Facebook has on you. I wrote about this process earlier (and 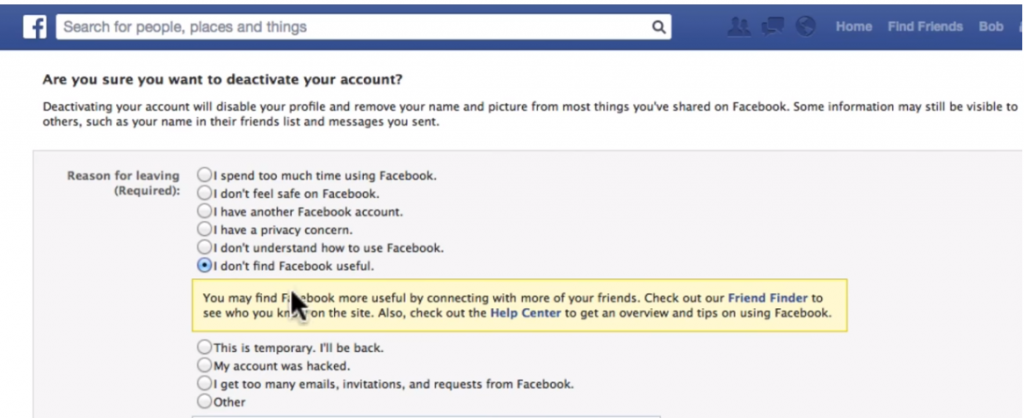
 So how do you get the audio and video signals from your computer to your living room TV? Two ways: either by connecting your computer directly to your TV with an HDMI cable or using one of several devices like Google’s Chromecast that does this for you wirelessly. If you use the direct cable connection from your computer, you will have to figure out a wireless keyboard and mouse to control it. If you use Chromecast, you will have to figure out the sequence of controls using the three apps that Google has (Google’s Chrome browser, Google Home and the Chromecast app itself) to get it setup. The workflow isn’t immediately obvious, and I suggest you learn the process before bringing your spouse into the room for the demo.
So how do you get the audio and video signals from your computer to your living room TV? Two ways: either by connecting your computer directly to your TV with an HDMI cable or using one of several devices like Google’s Chromecast that does this for you wirelessly. If you use the direct cable connection from your computer, you will have to figure out a wireless keyboard and mouse to control it. If you use Chromecast, you will have to figure out the sequence of controls using the three apps that Google has (Google’s Chrome browser, Google Home and the Chromecast app itself) to get it setup. The workflow isn’t immediately obvious, and I suggest you learn the process before bringing your spouse into the room for the demo.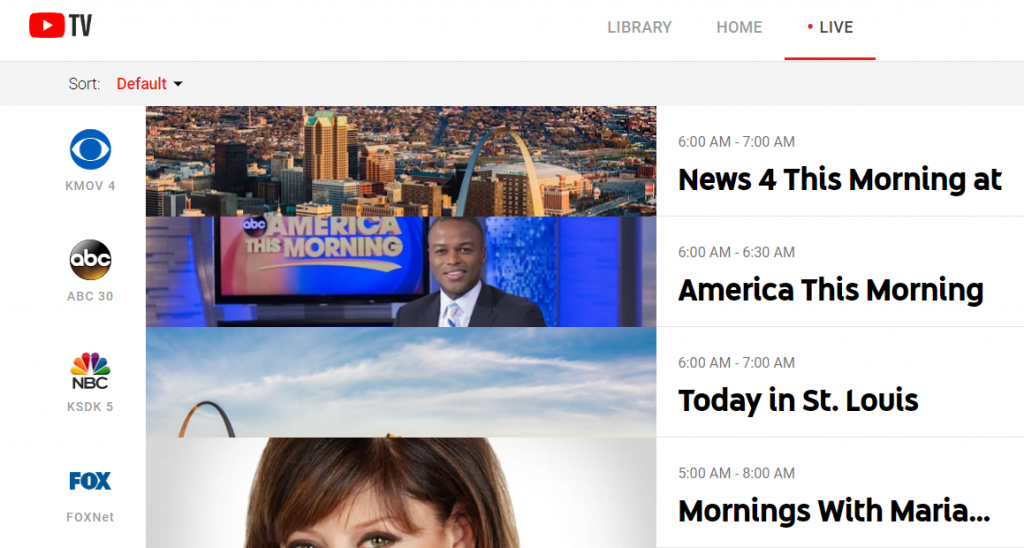
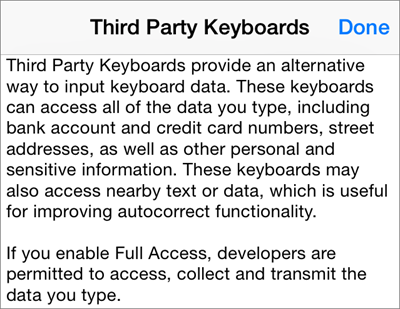 Here is the thing. In order to install one of these keyboard apps, you have to grant it access to your phone. This seems like common sense, but sadly, this also grants the app access to pretty much everything you type, every piece of data on your phone, and every contact of yours too. Apple calls this full access, and they require these keyboards to ask explicitly for this permission after they are installed and before you use them for the first time. Many of us don’t read the fine print and just click yes and go about our merry way.
Here is the thing. In order to install one of these keyboard apps, you have to grant it access to your phone. This seems like common sense, but sadly, this also grants the app access to pretty much everything you type, every piece of data on your phone, and every contact of yours too. Apple calls this full access, and they require these keyboards to ask explicitly for this permission after they are installed and before you use them for the first time. Many of us don’t read the fine print and just click yes and go about our merry way.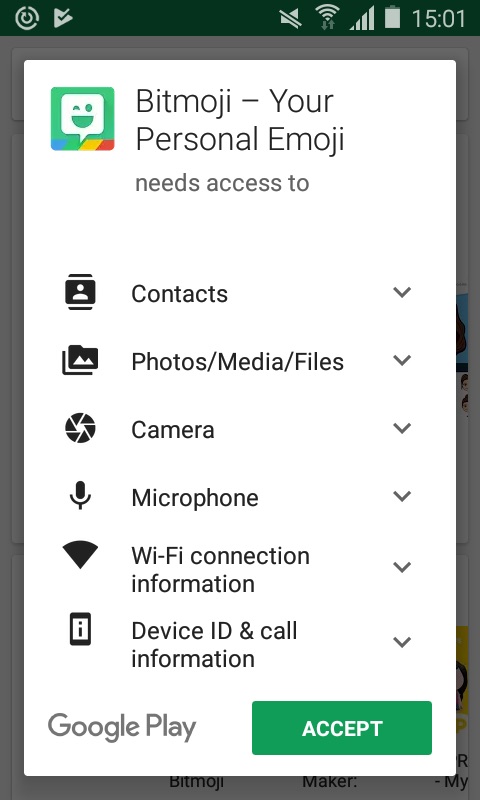 On Android phones, the permissions are a bit more granular, as you can see in this screenshot. This is actually just half of the overall permissions that are required.
On Android phones, the permissions are a bit more granular, as you can see in this screenshot. This is actually just half of the overall permissions that are required.