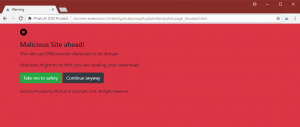
Phishing scams abound, if my own personal situation is any indication. This past weekend, I received two text messages — technically this is smishing or SMS phishing, but still. One looked like this (don’t worry, it is just a screencap):

You’ll notice a couple of tells. First is that it is addressed to me by name Usually, when my close friends and family send me texts, they don’t include my name. And the fact that a phisher knew my name is a bit concerning. The other is that it contains an active link, just waiting to be clicked on.
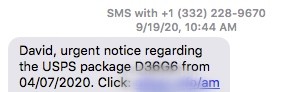 I got another text that was slightly less salacious, as you can see to the left. Again, my name is mentioned. Because of the subject, it is more insidious — now that we are ordering almost everything online the packages are coming to our doors in droves. But note this one tell — the package was mailed back in April. Granted, things are slowing down somewhat over at the USPS, but still.
I got another text that was slightly less salacious, as you can see to the left. Again, my name is mentioned. Because of the subject, it is more insidious — now that we are ordering almost everything online the packages are coming to our doors in droves. But note this one tell — the package was mailed back in April. Granted, things are slowing down somewhat over at the USPS, but still.
The FCC has issued this warning about smishing with several illustrations. And the crooks are getting more clever, with this case described by Brain Krebs on how one criminal combined smishing with using a cardless ATM transaction (meaning just using a mobile phone for withdrawals) to steal funds from victims’ accounts.
Corporate security folks are trying to get ahead of the attackers, and many regularly conduct phishing simulation or training exercises. Sometimes these misfire. The WaPost reported on a recent phishing training exercise that was completely misguided. The Tribune Co. sent around a message with “Congradulations, executives!!” in the subject line (hence my usage in today’s essay title). The email promises bonuses to come, if only the staffer would click on the enclosed link. Yes, the deliberate mistakes (spelling and duplicate exclamations) and the embedded link should be the tells that something is amiss. Whether you think this insensitive (given the number of layoffs in this industry) or just plain dumb, it still was a poor choice to demonstrate and train users. While it is true that potential phishing messages do use this particular lure, the Trib IT department should have known better.
Smishing isn’t the only lure used by hackers of course. Ironscales has compiled a collection of fake login pages that try to fool people into thinking they are authenticating their AT&T, Apple, Bank of America and more than a dozen other accounts. Their research has shown there are thousands of these fake login pages circulating around online. Ironically, the email from their PR department announcing this research was flagged by Google as risky, warning me not to click.
So here are a few pointers on how to prevent these types of attacks.
Don’t respond to any calls to action you get via texts or emails. Think before you click on the links or call the phone number listed. Better yet, don’t respond or click or call. This includes sending back a “Stop” text message. Just hit the delete key.
If you feel you have to respond, do it out of band. Go to the Fedex website directly and track your package that way. Call your bank directly to see if you have a fraud alert. Here is a Tweet stream that shows the lengths that one person went through to research and vet one text. My wife got a phishing email recently and did exactly that to find out it wasn’t genuine.
Finally, is something out of character? Is this a text or email out of the blue from some long-lost correspondent? Or does it contain (one or more) simple grammatical errors? Or is an offer of money too good to be true? That is because it isn’t. Do you really think the IRS or Social Security Administration sends you texts? News flash: they don’t.