Next week is the 20th anniversary of these essays. I wanted to take the time today to thank the various people that have guided my career, advise me and help advance my career in tech journalism. I have to start out with one of my first bosses, a man who taught me how to write and convinced me that I could become a writer, Grant Thompson. Grant and I were working at the time for a non-profit organization called the Conservation Foundation in Washington, D.C. I came there to help the organization build mathematical models for energy and environmental policy analysis, but came away from that job learning how to write. Little did I know how that would shape my career, and for all the countless hours that Grant spent marking up my drafts and teaching me my craft, I am forever grateful.
Several years later, I was working in IT for a large insurance company based in downtown LA called Transamerica Occidental Life. We had built one of the first end user computing departments to support a massive rollout of PCs. It was a great job, and I worked with Bob Zucker, Mark Will and Mike Storms there. All of them taught me to examine how people used technology in their jobs. This context would also be important to my subsequent career.
From Transamerica, I went on to work at PC Week (now eWeek) at my first editorial position. That was a dream job and I wrote about how I was hired here. I was hired by Mike Edelhart, who was a long-time Ziff Davis veteran and taught me how to become a great manager. PC Week was a massively talented organization and I learned from some of the best people in the tech journalism field, including Sam Whitmore, John Dodge, Paul Bonner, Peter Coffee, Gail Shaffer and Rob O’Regan, just to name a few.
Edelhart and I would write a book together, a book that was never published because we picked the wrong horse (OS/2) in an operating systems race that was eventually won by Microsoft WIndows. But years later I was ready to write another book when Marshall Rose asked me to collaborate with him on a book on corporate email in the late 1990s. Marshall is another brilliant man who invented the core Internet email protocols while in his early 20s. Writing a book with him was another life-changing experience for me.
After PC Week I went on to build my first publication from scratch, Network Computing. I worked for Al Perlman, and came to CMP at a time when it was starting many titles in an era when tech journalism was flourishing. I had the great fortune to learn from Mike Azzara, who was running another pub called Unix Today. Perlman went on to start many publications at CMP and elsewhere, and taught me a lot about startups.
Network Computing is still around, although online rather than in print. The team that I created from that publication has gone on to accomplish some great things, and many of those people are still in the tech community. I had the great fortune to hire Barry Gerber as my technical editor: Barry wrote articles for me at PC Week, and we would go on to work together at Tom’s Hardware, where he remained when I left there ten years ago. Barry taught me how to build and operate a test lab, and also how to be a better boss.
Over the years as a freelancer, I have had the good fortune to work for some of the best editors in the tech business, including Jackie Gavron, Rachel Parker, Jodie Naze, Neal Weinberg, Jennifer Bosavage and Stewart Alsop. Before Stewart became a VC, he was the editor at Infoworld in the early 1990s and gave me the assignment of writing a column by traveling to different businesses around North America and upgrading their networks over the weekend. These editors polished my prose and made me a better writer and it has been a blast to work for them.
Thanks everyone, including many others that I haven’t mentioned here. Next week I will write about some of the significant events that I have covered over my career and link back to some memorable columns.
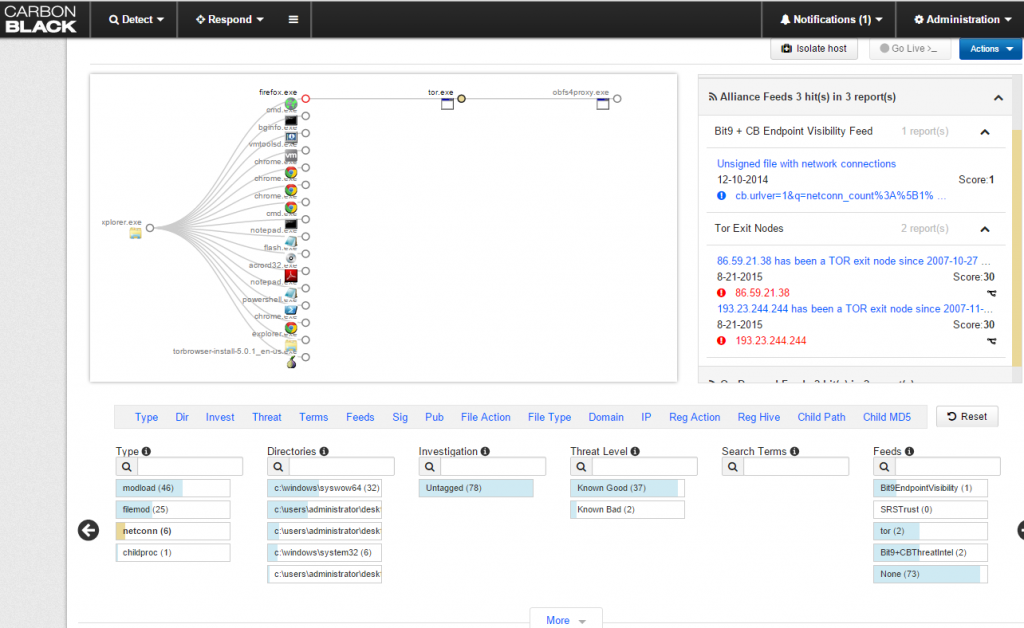
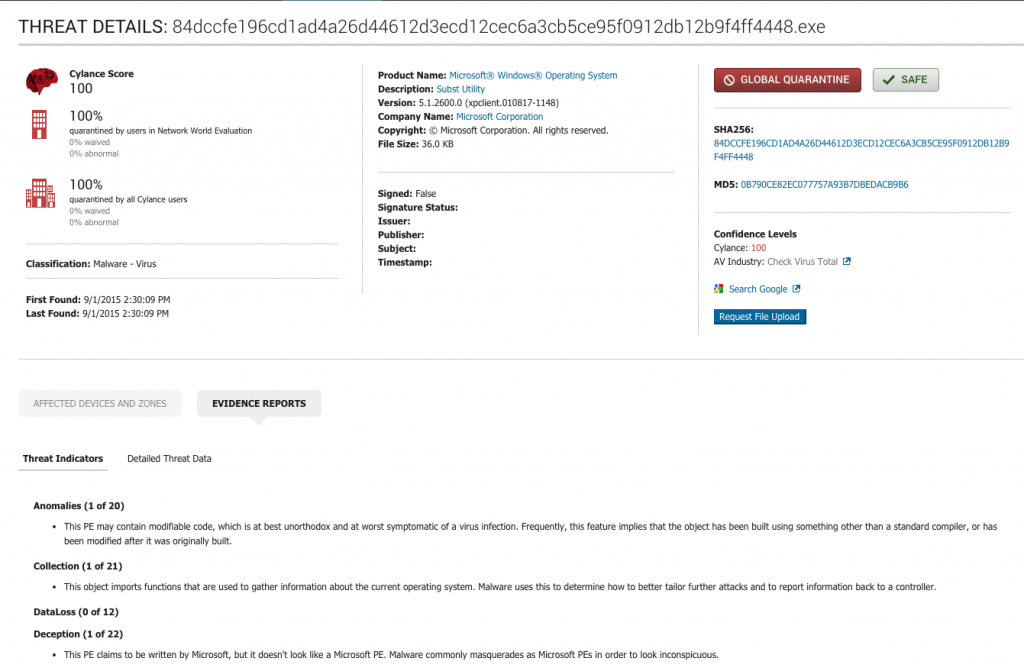
 The Security Operations Center (SOC) may be going the way of the dodo bird as security professionals outsource their protection to managed and cloud services. While many large organizations still have SOCs, smaller enterprises are finding that new technologies and better security architectures lessen the need to assemble large teams. This combination can make an IT team more proactive in protecting their infrastructure even without having a formal operations center.
The Security Operations Center (SOC) may be going the way of the dodo bird as security professionals outsource their protection to managed and cloud services. While many large organizations still have SOCs, smaller enterprises are finding that new technologies and better security architectures lessen the need to assemble large teams. This combination can make an IT team more proactive in protecting their infrastructure even without having a formal operations center.