I interviewed Arkansas-based Red Cross volunteer Mickey Shell as part of a package of stories about where other volunteers were after the 9/11 disaster. To give you an idea of the scope of the organization’s services, more than 57,000 Red Crossers from across the country served more than 14 million meals and snacks, opened dozens of shelters for people who were left stranded, and connected some 374,000 times with people to provide emotional support and health services.
Category Archives: Published work
Avast blog: Instagram bans are now being sold as crime-as-a-service
Cybercriminals are expanding their “services” by offering to ban an Instagram user for the low, low price of $60. This was recently reported by Motherboard, whose research showed that anyone on Instagram can harass or censor anyone else. The notion is actually pretty clever, because the same criminals (and their close accomplices) can then offer a “restoration” service to the victim for several thousands of dollars.
Instagram has a support page that walks you through how to protest a disabled or banned account. It isn’t very good. In my post for Avast’s blog, I mention the issues and what you can do to harden your Instagram account.
CSOonline: How to find the right testing tool for Okta, Auth0, and other SSO solutions
If you have bought a single sign-on (SSO) product, how do you know that is operating correctly? That seems like a simple question, but answering it isn’t so simple. Configuring the automated sign-ons will require understanding of the authentication protocols they use. You will also need to know how your various applications use these protocols—both on-premises and SaaS—to encode them properly in the SSO portal. It would be nice if you could run an automated testing tool to find out where you slipped up, or where your SSO software is failing. That is the subject of this post. You can read more on How to find the right testing tool for Okta, Auth0, and other SSO solutions on CSOonline here.
NokNok blog: Next level metal credit cards
 I got my first metallic credit card from Apple a few years ago. I thought it was more a curiosity than anything else. Soon after, my wife got a metallic card from Chase. American Express and Discover have both been making metal cards for years as well. Now, thanks to a partnership between NokNok and CompoSecure, you will see new types of cards that have something besides their outer skin to offer consumers: the ability to include authentication tokens and cold cryptocurrency wallets. You can read more in my blog post for NokNok here.
I got my first metallic credit card from Apple a few years ago. I thought it was more a curiosity than anything else. Soon after, my wife got a metallic card from Chase. American Express and Discover have both been making metal cards for years as well. Now, thanks to a partnership between NokNok and CompoSecure, you will see new types of cards that have something besides their outer skin to offer consumers: the ability to include authentication tokens and cold cryptocurrency wallets. You can read more in my blog post for NokNok here.
Avast blog: Protect your online store against Magecart attacks
Shopping cart malware, known as Magecart, is once again making headlines while plying its criminality across numerous ecommerce sites. Its name is in dishonor of two actions: shopping carts, and more specifically, those that make use of the open-source ecommerce platform Magento. Magecart malware compromises shopping carts in such a way that credit card data collected by the cart is transmitted to cybercriminals, who in turn resell this information to other bad actors. In my blog for Avast, I review some of the more notable attacks over the past several years and catalog the confluence of trends that have made Magecart a popular threat vector.
In addition to some suggestions on how you can strengthen your ecommerce storefront, here are a few other tips to try to prevent this from happening to your website:
- Use this browser-based tool from Trustwave to check if your site has been compromised, along with other tips listed in the blog post to help you investigate your web storefront code.
- Use isolation tools such as this one from SourceDefense to better control access rules and prevent malicious script injections.
- Finally, whatever website server software you use, make sure you apply updates as soon as possible. Magento users who were compromised by early attackers delayed these updates and the attackers found these outdated versions and took advantage of them. The software vendor lists current patches and also has a free vulnerability scanning tool too.
Book review: The Next Rules of Work
I have known Gary Bolles for decades. Back when I was putting together the first editorial staff for Network Computing magazine, Gary was one of my early hires. He had a curious resume, made even more so by the fact that his father was infamous for the “Parachute” career counseling books. He was a quick learner — so quick that when I left the magazine to start my own consulting business he was my pick to succeed me, and then went on to found other publications and eventually his own consultancy. He has written his first book, and it complements the family business by showing how we have evolved in how we approach work. His thesis is that we are in a new era, where the old rules of pre-learning isn’t sufficient, and we need to become lifelong learners with a deep portfolio of experiences, interests and job-like skills.
Part of the new rules is directed towards managers, who have to transition from being the “sage on the stage” to the “guide on the side.”
Like the Parachute series, there is assigned homework, which is just as annoying as when I read Bolles Sr. books back in the day. The model canvas can be found on Gary’s website here.
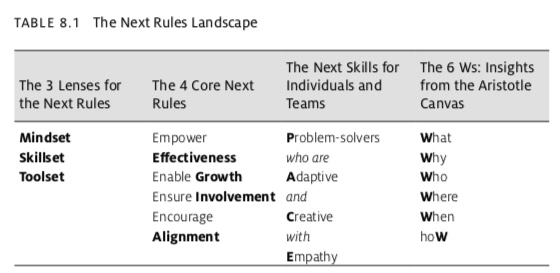 Most of his book is focused on adjusting three frames of reference for both individuals and the new companies that they work for: Mindset, toolset and skillset. You will need to adjust your mindset to handle what the world needs, what you love and are good at, and what you can actually be paid hard cash money for.) The Japanese call this Ikigai. You will need to adopt what he calls “flash problem solving” skills with an ad hoc group he calls the coalition of the willing. This may mean “unbossing” yourself, which sounds scary but millions of gig workers have already succeeded.
Most of his book is focused on adjusting three frames of reference for both individuals and the new companies that they work for: Mindset, toolset and skillset. You will need to adjust your mindset to handle what the world needs, what you love and are good at, and what you can actually be paid hard cash money for.) The Japanese call this Ikigai. You will need to adopt what he calls “flash problem solving” skills with an ad hoc group he calls the coalition of the willing. This may mean “unbossing” yourself, which sounds scary but millions of gig workers have already succeeded.
Another concept is one that I wrote about last week, how to become a life-long learner and what this means for retirement.
There are a lot more thought experiments and Venn diagrams to illustrate his points. If you are ready to make the jump and sign on to this new way of life, you might find the book a useful manual. Bolles book is available on his website, and if you are still unsure you might want to sign up and watch a couple of his classes on LinkedIn Learning ($30/mo).
Avast blog: Here’s how hackers can steal your data using light, radio, and sound waves
Most of us are familiar with the primary methods for moving data into and off of our computers: think Wi-Fi networks, USB ports, and Bluetooth connections. However, there are additional, lesser known ways in which data can be retrieved from a device. An elite group of cyber researchers from Ben-Gurion University (BGU) in Beersheva, Israel, have made it their mission to figure out more than a dozen different ways that bad actors with lots of time can extract information, even if you think your PC isn’t connected to anything obvious.
In my post for Avast’s blog, I summarize these methods and provide some advice on how to avoid these sorts of attacks.
Two new posts on cybersec certifications advice from Infosec Resources
Figuring out your appropriate certification program isn’t easy and involves almost as much studying as preparing for the certification exams themselves. But these programs can have big payouts in terms of job advancement, increases in responsibility and salary. I wrote two posts for Infosec Resources.
In our first post, we presented the issues a manager should consider in building a training program for their company. Training budgets tend to be the first ones to be cut in any economic downturn and often don’t get fully funded even when the economy is improving. But training can also have a significant impact on an enterprise: it can increase the pool of available skills, help pave the way for a department to take on new challenges, improve morale and create a sense of purpose for workers. In this first post, I talk about what are some of the benefits of training and ways to measure them, explore some of the costs, and the four different modalities that you can use to design your own training program.
In the second post, I explore the benefits and costs from the individual’s perspective and what you should expect from a certificate program and how to evaluate a program. This post also has a handy comparison chart that shows your costs and other considerations from the major infosec certs.
| Provider/Link | Cost | Other certifications to consider |
| COMPTIA Security+
|
$390 for 90-minute test | Penetration testing, cybersecurity analyst and general IT courses too |
| EC-Council Certified Ethical Hacker (CEH)
|
$1200 for four-hour test | More than a dozen cybersecurity specializations including disaster recovery, penetration testing |
| ISACA Certified Info Security Manager (CISM)
|
$760 for four-hour test for non-members but significant discounts for members, study materials extra | Courses on risk management, data privacy and auditing |
| ISC2 Certified Cloud Security Practitioner (CCSP)
|
$549 for four-hour test | Also offer numerous other cloud-based security classes and boot camps for above tests |
| Offensive Security Penetration Testing | $800 for a one year subscription | Three different levels, other certifications in web apps and devops |
| SANS Institute Network penetration testing | $8,000 for in-person instruction at various locations around the world | Dozens of courses covering a wide range of infosec topics |
Avast blog: An Ugly Truth: A book review
 New York Times reporters Sheera Frenkel and Cecilia Kang have been covering the trials and tribulations of Facebook for the past several years, and they have used their reporting to form the basis of their new book, An Ugly Truth: Inside Facebook’s Battle for Domination. The book is based on hundreds of interviews of these key players and shows the roles played by numerous staffers in various events, and how the company has acted badly towards protecting our privacy and making various decisions about the evolution of its products. Even if you have been following these events, reading this book will be an eye-opener. If you are concerned with your personal security or how your business uses its customer data, this should be on your summer reading list. The book lays out many of the global events where Facebook’s response changed the course of history.
New York Times reporters Sheera Frenkel and Cecilia Kang have been covering the trials and tribulations of Facebook for the past several years, and they have used their reporting to form the basis of their new book, An Ugly Truth: Inside Facebook’s Battle for Domination. The book is based on hundreds of interviews of these key players and shows the roles played by numerous staffers in various events, and how the company has acted badly towards protecting our privacy and making various decisions about the evolution of its products. Even if you have been following these events, reading this book will be an eye-opener. If you are concerned with your personal security or how your business uses its customer data, this should be on your summer reading list. The book lays out many of the global events where Facebook’s response changed the course of history.
My review of the book and some of the key takeaways for infosec professionals and security-minded consumers can be found here.
Avast blog: Beware of crypto exchange scams
 You may already have won! How many scams have begun with these words?
You may already have won! How many scams have begun with these words?
There is a new breed of scammers gaining popularity, thanks to the wild swings in the cryptocurrency market. I worked with Avast researcher Matěj Račinský who has tracked three different fake crypto exchanges, I show you some of the come-on messages, why their tactics are so compelling and — almost — believable — and how they ply their criminal trade, including phony news sites announcements (as shown here).
You can read more about these scammers, and ways to avoid them, in my blog post for Avast here.