An intrusion detection or prevention system can mean the difference between a safe network and a nasty breach. We’ve rounded up some of the best and most popular IDS/IPS products on the market.
Detecting and preventing network intrusions used to be the bread and butter of IT security. But over the past few years, analysts and defenders have seen a slow but steady transition from these products. They have become a component of a broader spectrum of network defensive tools, such as security information and event management (SIEM) systems, security orchestration and response (SOAR) and endpoint and network management and detection systems.
For CSO, I examined the top six commercial tools and four open source ones, explain the different approaches and form factors used, and compare how intrusion prevention fits into the overall security marketplace.
 When a veteran retires, most don’t think of setting up their homes on a military base, but that is what Jill Eaves and her family did at Missouri’s Fort Leonard Wood. The Army post is home to the Sixth Infantry Division and one of four major training centers. For the past 80 years has seen hundreds of thousands of members of all four branches of the armed forces train for active and reserve duty, including specialized engineering training. Eaves and her husband of 10 years both served in the Air Force, and when the time came for retirement, they decided to move back on a military installation. After all, with more than 63,000 acres, there is plenty of room. “It is a great place to raise my two children, too,” she said.
When a veteran retires, most don’t think of setting up their homes on a military base, but that is what Jill Eaves and her family did at Missouri’s Fort Leonard Wood. The Army post is home to the Sixth Infantry Division and one of four major training centers. For the past 80 years has seen hundreds of thousands of members of all four branches of the armed forces train for active and reserve duty, including specialized engineering training. Eaves and her husband of 10 years both served in the Air Force, and when the time came for retirement, they decided to move back on a military installation. After all, with more than 63,000 acres, there is plenty of room. “It is a great place to raise my two children, too,” she said.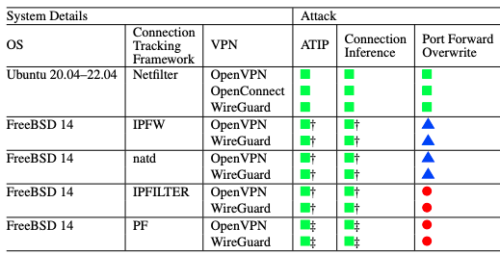 As you can see from the chart below, it goes to the way modern VPNs are designed and depends on Network Address Translation (NAT) and how the VPN software consumes NAT resources to initiate connection requests, allocates IP addresses, and sets up network routes.
As you can see from the chart below, it goes to the way modern VPNs are designed and depends on Network Address Translation (NAT) and how the VPN software consumes NAT resources to initiate connection requests, allocates IP addresses, and sets up network routes.