By now we are all too familiar with phishing attacks. They have received lots of press coverage and are at the heart of many cyberattacks. But hackers are getting more specialized and have turned towards other variations, one of which goes by the term smishing. This is a combination of social engineering techniques that are sent over SMS texts rather than using the typical emails that traditional phishing lures use. SMS phishing, get it? In Verizon’s 2020 mobile security index, they found that 15% of enterprise users encountered a smishing link in Q3 2019. In my latest post for Network Solutions’ blog, I demonstrate how these kinds of attacks work, how the criminals have upped their game, and what you can do to protect yourself.
By now we are all too familiar with phishing attacks. They have received lots of press coverage and are at the heart of many cyberattacks. But hackers are getting more specialized and have turned towards other variations, one of which goes by the term smishing. This is a combination of social engineering techniques that are sent over SMS texts rather than using the typical emails that traditional phishing lures use. SMS phishing, get it? In Verizon’s 2020 mobile security index, they found that 15% of enterprise users encountered a smishing link in Q3 2019. In my latest post for Network Solutions’ blog, I demonstrate how these kinds of attacks work, how the criminals have upped their game, and what you can do to protect yourself.
Avast blog: One mo’ election update: ransomware
We’re less than a week away from the 2020 U.S. election, and there has been news of a ransomware attack in northern Georgia. The attack hit a network that supports the Hall County government infrastructure and includes election and telephone systems. It was the first time that systems were brought down, although it wasn’t the first time election systems have been targeted by ransomware. Those happened in Louisiana and Washington State, both unsuccessful. In my blog post today for Avast, I go into the details about these attacks and some of the deficient cybersecurity practices also happening in Georgia.
Avast blog: Your data is for sale from election data brokers
By now, many of you know that your online shopping and social media usage patterns can be tracked and recorded. This includes data about your political preferences, which is especially relevant given the approaching elections. Data brokers can use and abuse this information by bundling and selling your data to third parties who are interested in targeting you as a consumer, a buyer, or as a potential voter.
You can read more about this issue in my blog for Avast today and how you can use one of their products, BreachGuard, to help hide your data from brokers and keep improve your privacy posture on social media.
Coping with Covid contention
 With the election and the holidays approaching, you may be experiencing some conflicts with family and friends when the conversation turns to Covid. It has been a hard year for all of us, whether we are under extreme lockdown or just trying to get our kids through the school day. This post will hopefully provide some pointers on how to cope. If only things were as easy as that infamous Monty Python sketch.
With the election and the holidays approaching, you may be experiencing some conflicts with family and friends when the conversation turns to Covid. It has been a hard year for all of us, whether we are under extreme lockdown or just trying to get our kids through the school day. This post will hopefully provide some pointers on how to cope. If only things were as easy as that infamous Monty Python sketch.
When I was seeing my own conflicts over the pandemic, I first thought to bring in a professional mediator. I’ve known June Jacobson for close to 20 years. We first met under very difficult circumstances: I was getting divorced and my (now) ex-wife and I had decided to try her rather than both hire our own lawyers. Our sessions with her didn’t work out, but June and I remained in occasional contact.
June continues to work almost exclusively with mediation for divorcing couples and has had several families who have come to her explicitly about resolving their Covid issues. Certainly Covid has changed the nature of her consultations. “Everything is happening online,” she told me in a recent call. “While it is true that people don’t have to travel, they may not have a home environment that can be private enough, especially if they have kids or other family members living with them. Spouses who are still living together sometimes have to share the same computer screen, which can require close physical proximity that may not feel comfortable or safe.”
This lack of compartmentalization has accelerated some issues with divorcing couples and these times are trying ones for couples that are nearing the end of their marriages. “More people want to get divorced now that they have been incarcerated with their spouse all this time.” Still, the basics of mediation haven’t changed. “Usually, when a couple first comes in to see me, they need a shared agenda and a common plan. I use some tools from therapy to help with listening to each person’s point of view, and try to facilitate communication and contribute to mutual understanding.” She has a wide spectrum of training, including social work and legal degrees. “What makes mediation successful is that there are usually overriding values that enable a couple to come to the table to reach a mutually acceptable outcome. We try to focus on the future, not get stuck in the past with trying to agree on a narrative of the history of their relationship. My job is to be non-judgmental about this historical context, to understand and respect their realities, and sometimes to hold alternative versions of reality from each partner in mind.”
Part of the Covid contention is that people start out from wildly differing fact bases. Then stir in a few conspiracy theories and what you have is truly a failure to communicate. Covid has certainly made things harder for families that have to run their businesses and schools and day care all out of a house that is maybe severely space-constrained and ill-designed for these multiple purposes.
While I was talking to June, I read this NYT article by Charlie Warzel about coping with difficult family discussions. Warzel has several tips on how to interact with your family members with Covid contention:
- Give people an understanding of their information environment
- Create a bit of common ground and lay the foundation to explore how unproven conspiracy theories differ from reality
- Fact-checking is valuable but don’t count on it to change someone’s beliefs
- Don’t debate these issues on Facebook
- Don’t be a scold — be gentle, compassionate and patient
- Know when to walk away and try another day.
These gambits sound good in theory, but in the real world it is hard to implement them in practice. But I want to end this post on a lighter note, so I will leave you with one last link, to a clip from Lewis Black’s latest comedy routine, where he touches on this contention. The clip is NSFW but very funny. Almost as funny as the Pythons’ bit.
Network Solutions blog: How to Recognize and Prevent Homograph Attacks
I have written a few times about ways to prevent brandjacking. In this blog post for Network Solutions, I discuss the use of homoglyph or homograph attacks by cybercriminals. These attacks involve exploiting international domain names and the idea is simple to explain once you know a bit of Internet history.
 When the Internet was first created, it was based on using Roman alphabet characters in domain names. This is the character set that is used by many of the world’s languages, but not all of them. As the Internet expanded across the globe, it connected countries where other alphabets were in use, such as Arabic or Mandarin.
When the Internet was first created, it was based on using Roman alphabet characters in domain names. This is the character set that is used by many of the world’s languages, but not all of them. As the Internet expanded across the globe, it connected countries where other alphabets were in use, such as Arabic or Mandarin.
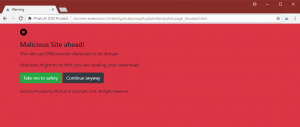
Several years ago, researchers discovered the homograph ploy, and since then all modern browsers have been updated to recognize the homograph attack methods of using “xn–80ak6aa92e.com” instead of “apple.com.” I go into the details in my blog post and you can see an example of how a browser responds above.
There is an important lesson here for IT professionals: watch out for injection-style attacks across your web infrastructure. Every element of your web pages can be compromised, even rarely-used tiny icon files. By paying attention to all possible threats today, you’ll save yourself and your organization a lot of trouble tomorrow.
Avast blog: Trying to take down Trickbot
TrickBot is a malware network that is often described as one of the world’s largest with at least a million PCs. It is once again in the news. Earlier this month, the botnet was the focus of two independent efforts to take it down: from an industry group led by Microsoft and from the US Cyber Command. The TrickBot attempted takedown is just a sign of things to come. What is interesting is how the private and public sector has worked in tandem, using new strategies such as copyright violations and military-grade operations. I go into the details in
Book review: Mirror Man
 At first glance, the plot line of this book seems tired: part clash of the clones, part “Total Recall” memory conflicts, part retread sci-fi mystery. But as you get drawn into the book, which concerns a pharma marketing exec who volunteers for an illegal cloning experiment, replacing himself with a clone for a year, you find out it is quite original and intriguing. The clone — and his body double who is locked away — are both carefully observed, although not as carefully as the scientists think. By the time you reach the end, you’ll have thoroughly enjoyed this book, and the combination of sci-fi and mystery is a nice balance. Highly recommended and I might have to rewatch the original Total Recall just to savor some of those memories, wholesale.
At first glance, the plot line of this book seems tired: part clash of the clones, part “Total Recall” memory conflicts, part retread sci-fi mystery. But as you get drawn into the book, which concerns a pharma marketing exec who volunteers for an illegal cloning experiment, replacing himself with a clone for a year, you find out it is quite original and intriguing. The clone — and his body double who is locked away — are both carefully observed, although not as carefully as the scientists think. By the time you reach the end, you’ll have thoroughly enjoyed this book, and the combination of sci-fi and mystery is a nice balance. Highly recommended and I might have to rewatch the original Total Recall just to savor some of those memories, wholesale.
Here is an excerpt from the new Jane Gilmartin novel.
Cord cutting ain’t easy
-
- The UIs are just awful for the streaming services. Maybe we got used to the cable UIs over time — which wasn’t anything to crow about. YouTubeTV has the best interface, but it is the best of a bad lot. The problem is those change-resistors that I mentioned above. And it doesn’t help matters that you don’t usually have a keyboard to navigate these UIs. While it is nice that the new Google TV and some of the other devices (Like the sticks from Roku and Amazon) come with a remote, this isn’t enough.
- If you have a mixed collection of different TV vintages, you are probably going to be switching between the web UI and the TV app UI, which will further confound the change-resistors in your family. Exhibit A is Netflix: their web UI has been perfected over a longer time than any of their app UIs, and despite all the code development, both of them are still less than satisfying.
- The app collection for your TV is disappointing. This isn’t like getting apps on Google Play or iTunes app stores. You are stuck with whatever is available for your particular generation of TV. I got a new TV last year, which is great for that TV, but unless you plan on upgrading all your home’s TVs you won’t be happy with the older vintage apps available.
- One of the bigger downfalls of the streaming services is being able to easily rewind and fast forward (including through commercials). Uverse (and just about every cable TV provider) makes this easy. Every streaming service makes this a lot harder, and in some cases you can’t skip the ads (unless you buy a premium package, and then that just lets you skip some of the ads). One of the reasons why we record our favorite programs is being able to skip ALL the ads. I also found that the time of day that you watch will determine how many ads get inserted into your programming streams.
- You need to read the fine print. Some of the streaming services have extra charges for multiple users or multiple TVs or multiple devices, to remove some of the ads, or to add additional capacity for recording your shows. A small subset of the various Hulu “add-ons” are shown in the screencap at left.
- Finally, the TV apps don’t easily maintain channel states after the TV is turned off. When I am watching channel 5 on any of my TVs — smart or not — if I turn it off and then back on, it stays on channel 5. This is not necessarily so with the apps. With my smartest and newest Samsung TV in my living room, there is a setting on the menu that I found after much poking around to enable this. But it was purely by persistence that I found it.
So I went back to Uverse over the weekend. It was an interesting experiment, and I appreciate my wife being patient as I messed around.
Live blogging at the Avast CyberSecAI conference
Last year I was fortunate enough to attend in person the CyberSecAI conference in Prague, a unique blend of academic and business researchers and practitioners involved in both cybersecurity and AI fields. This year the conference went completely virtual. I covered most of the sessions through live Tweets and wrote two blog posts that are now up on Avast’s website:
- Creating and weaponizing deep fakes. Dr. Hany Farid of UC Berkeley spoke about their evolution, the four different types of fakes, and ways that we can try to solve their challenges. I found his analysis intriguing, and his use of popular figures that were deliberately fakes brought home how sophisticated AI algorithms is needed to flag them definitively.
- Understanding bias in AI algorithms. A blue-ribbon panel of experts discussed how to reduce AI algorithmic bias. Should we hold machines at higher standards than we do of ourselves? It was moderated by venture capitalist Samir Kumar, who is the managing director of Microsoft’s internal venture fund M12 and included:
- Noel Sharkey, a retired professor at the University of Sheffield (UK) who is actively involved in various AI ventures,
- Celeste Fralick, the Chief Data Scientist at McAfee and an AI researcher,
- Sandra Wachter, an associate professor at the University of Oxford (UK) and a legal scholar, and
- Rajarshi Gupta, a VP at Avast and head of their AI and Network Security practice areas.
Part of the problem with defining bias is in separating correlation from causation, which was brought up several times during the discussion.
Mail-in ballots are the new literacy tests
 I was watching a fascinating movie on Amazon called All In. It documents voting suppression history in the US. While we have had various laws, including several Constitutional amendments, their implementation is mostly a local matter. Some local officials have done what they can to deny the vote over the years. For the most part, the documentary is accurate. It features numerous interviews with Stacey Abrams, who lost the Georgia governor’s race in 2018.
I was watching a fascinating movie on Amazon called All In. It documents voting suppression history in the US. While we have had various laws, including several Constitutional amendments, their implementation is mostly a local matter. Some local officials have done what they can to deny the vote over the years. For the most part, the documentary is accurate. It features numerous interviews with Stacey Abrams, who lost the Georgia governor’s race in 2018.
The movie comes at an interesting time. In my blog post for Avast this week, I summarize many of the voter suppression efforts that we have seen in the past several years, including leading up to the 2016 and 2018 national elections. There was a lot of data on suppression collected by Mueller. His report showed that more than 3,500 ads on Facebook were placed by the Russian Internet Research Agency to try to convince potential Black voters to stay home during the 2016 elections. The same group also posted a series of anti-Muslim ads and organized concurrent protest rallies in Texas on opposite political sides. My Avast post has more details on the recent suppression efforts seen this year.
There are efforts to try to encourage everyone to vote, including a major ad spend by a new non-profit group called National Council on Election Integrity.
In the Amazon All In documentary, one person suggests the 2016 efforts should be called “Jim Crow v2.0,” referencing the pre-60s laws (and more recent changes) that made voting difficult by instituting literacy tests and poll taxes. You can see some archived examples of 1960s-era literacy tests here. These tests are almost impossible to pass, even f you have a graduate degree in American Studies.
I want to take things a step further: I think we are now in the Jim Crow v3.0 era. The new literacy test is the result of a confusing series of mail-in and absentee ballot regulations and shifting court challenges that are now happening across our country. My wife and I voted via mail-in ballots in Missouri: it took a lot of re-reading the various instructions, figuring out the steps involved, getting our ballots notarized and then mailed in. Each ballot has to be returned in a matching envelope and is tagged with a QR code that you can scan to check on its progress, to ensure that the elections board received it. (They did.) A good resource is what the Washington Post has put together that tells you when and how you can vote in your state.
But there is a subtle difference between mail-in (which anyone in Missouri can do) and absentee (which you have to certify that you aren’t going to make it to the polls). They have different deadlines and other requirements. For my Avast blog, I got to talk directly to Trevor Timmons, the CIO for the Colorado Department of State, the agency that supervises its elections. In its June 2020 primary, more than 99% of registered voters submitted mail-in ballots. Colorado is one of those “universal” mail-in states, meaning that every registered voter will receive a mail-in ballot. You can come and vote in person, but most people don’t. You can also register and vote on election day, something only a few states have.
After I had mailed in our ballots, I had a senior moment where I thought I swapped my ballot and put it in my wife’s return envelope, and vice-versa. Timmons told me that they specifically look out for these situations and still validate both ballots: “It is a common error that takes manual intervention to resolve, but it is resolved quickly.”
What about fraud with mail-in votes? If you examine this page from the Heritage Foundation, you can see their dashboard of fraud has found 1,300 cases. That sounds like a lot but not when you compare that with the hundreds of millions of votes cast. Timmons is more worried about election security, and has put a series of measures in place, such as MFA required for all election judge since 2013), applying current software patches and using other endpoint detection tools to stop malware attacks. “We have seen ransomware incidents in some of our counties that compromised other agencies. We detected them when the attacks attempted to move to the elections boards and we were able to stop their spread.”
Meanwhile, October hasn’t been without its election systems hiccups. Voter registration systems were overwhelmed in Florida. Georgia’s electronic voting machines had some issues on the first days of early in-person voting, and Virginia’s and Pennsylvania’s online registration systems were both down thanks to a construction crew cutting a fiber cable and a systems crash in a data center, respectively.