One of the things not lacking in the information security community is the dozens of cybersecurity industry certifications that are available to burnish your qualifications. These include vendor-driven certifications from leading security companies like Cisco and Microsoft, courses that will lead towards certifications from SANS, and many others. In this post for Avast’s blog, I will guide you through this maze.
From the archives: my work for the US Congress’ Office of Technology Assessment
Seeing the attacks on our Capitol brought memories of working for Congress back in the early 1980s for this small bipartisan agency. I contributed chapters of two major research reports:
- Industrial and Commercial Cogeneration (1983) where I discussed some of the early technologies that generate heat and electric power and built a mathematical model used to guide the eventual policy recommendations
- and New Electric Power Technologies: Problems and Prospects for the 1990s (1985), where I discussed some of the issues involving interconnection and power distribution.
I am thankful that the Woodrow Wilson Center at Princeton has preserved these digital copies.
Avast blog: It’s time to consider getting a Covid-19 vaccine passport for travel
As the number of people getting vaccinated against Covid-19 rises, it’s time to review the ways that people can prove they have been inoculated when they want to cross international borders. These so-called “vaccine passports” have been in development over the past year and are starting to go through various trials and beta tests. The passports would be used by travelers to supplement their actual national passport and other border-crossing documents as they clear customs and immigration barriers. The goal would be to have your vaccination documented in a way that it could be accepted and understood across different languages and national procedures.
In my blog for Avast, I talk about how these passports (such as the CommonPass open source one being developed above) could prove to be a solution for travelers crossing borders, but they also come with their own set of challenges
Kaspersky blog: Despite all the cool tools, tech collaboration is still missing something
Since the pandemic began, organizations have been working hard on how they collaborate. But something’s still missing, and it’s to do with people. Looking at successful tech and creative collaborations of the past, common trends emerge. Any organization can use these to kickstart better collaboration within and between their teams. I highlight a few of these classic great situations, including the effort to produce new Covid vaccines, how the Unabomber was found by the FBI, the Bletchley Park code-breakers, and others for my latest blog post for Kaspersky.
Where is your phone central office?
 I have written before about my love affair with telephone central offices. This past week, we all now know where Nashville’s CO is located, and we mourn for the people of that city. Nashville is a city that I have been to numerous times, for fun and for business. Little did I realize as I walked among the honky tonk bars and restaurants on Second Street that I was passing by its main CO, which offers a wide range of communication services.
I have written before about my love affair with telephone central offices. This past week, we all now know where Nashville’s CO is located, and we mourn for the people of that city. Nashville is a city that I have been to numerous times, for fun and for business. Little did I realize as I walked among the honky tonk bars and restaurants on Second Street that I was passing by its main CO, which offers a wide range of communication services.
Like the CO that was buried by the collapse of the World Trade Center back in 2001, there was a lot of water damage from the firefighters, and the Nashville repairs were hampered by having to work around the crime scene investigators. But still, within a few days AT&T was able to get various services back up and running, including 911 and airport communications, along with wired and cellular services. The company deployed a series of portable cell towers around the region. The lines that went through this CO connected not just Nashville but areas that were in adjoining states.
This is the conundrum of the CO: in the early days of telephony, they had to be located in densely populated areas, because stringing copper lines from each termination point cost money. To shorten the lines, they had to put them near the people and businesses that they were connecting. This means that you can’t easily protect them with physical barricades a la Fort Knox (or other government buildings). Plus, there are more than 20,000 COs in the US by some estimates. That is a lot of real estate to protect or potentially relocate.
COs are also relatively easy to find, even though many of them are located in nondescript building in major urban areas. My own CO sits like Nashville’s across from a similar collection of restaurants and commercial businesses. There are websites lovingly constructed by other fans of telecom, such as this one or this one that show photos of the actual buildings (although you will have to work a bit to find their street addresses). In my blog post from 2018, I posted pictures of several COs that I have been to, including one on Long Island where I brought my high school networking class on a field trip back in 2001.
Whether or not the bomber was intentionally targeting AT&T’s CO or not, one thing is pretty clear to me: these COs are the weak points in any terror campaign. I don’t have any real solutions to offer up here, just an aching spot in my heart for the men and women that have built them and keep them running.
N.B. This is the last day of a horrible year, a year punctuated with my own personal health story that had nothing to do with Covid. I want to send out a note of thanks to all of you that took the time to send me your support, and hope that you found your own support team to help you along as well. Here is my wish that 2021 will be better for all of us, and that we can support and care for each other to make it so.
Red Cross blog: Dennis Grooms, retired no more!
 You might think that after a freak accident falling 70 feet when trying to trim one of his trees would be enough of an incentive to retire, but then you probably don’t know Dennis Grooms. Fortunately, Grooms managed to survive his 2009 fall. But in the process, he managed to break both legs and had other injuries as well as come out of a multi-day coma and chalk up a three months’ stay in the hospital. The fall did have one benefit: in his retirement, he was able to step up his volunteer efforts at various disaster deployments, both for the American Red Cross and other relief agencies.
You might think that after a freak accident falling 70 feet when trying to trim one of his trees would be enough of an incentive to retire, but then you probably don’t know Dennis Grooms. Fortunately, Grooms managed to survive his 2009 fall. But in the process, he managed to break both legs and had other injuries as well as come out of a multi-day coma and chalk up a three months’ stay in the hospital. The fall did have one benefit: in his retirement, he was able to step up his volunteer efforts at various disaster deployments, both for the American Red Cross and other relief agencies.
I wrote more about his experience with ARC and how he is anything but retired.
Who benefits most from Facebook: the right or the left?
 This piece by Adrienne LaFrance in the Atlantic goes further, saying that Facebook has become the embodiment of the “doomsday machine,” first made popular during the Cold War and the central plot device of Dr. Strangelove, a movie we should rewatch in this new context. “Facebook does not exist to seek truth and report it, or to improve civic health, or to hold the powerful to account,” she says. “It has the power to flip a switch and change what billions of people see online. No single machine should be able to control so many people.”
This piece by Adrienne LaFrance in the Atlantic goes further, saying that Facebook has become the embodiment of the “doomsday machine,” first made popular during the Cold War and the central plot device of Dr. Strangelove, a movie we should rewatch in this new context. “Facebook does not exist to seek truth and report it, or to improve civic health, or to hold the powerful to account,” she says. “It has the power to flip a switch and change what billions of people see online. No single machine should be able to control so many people.”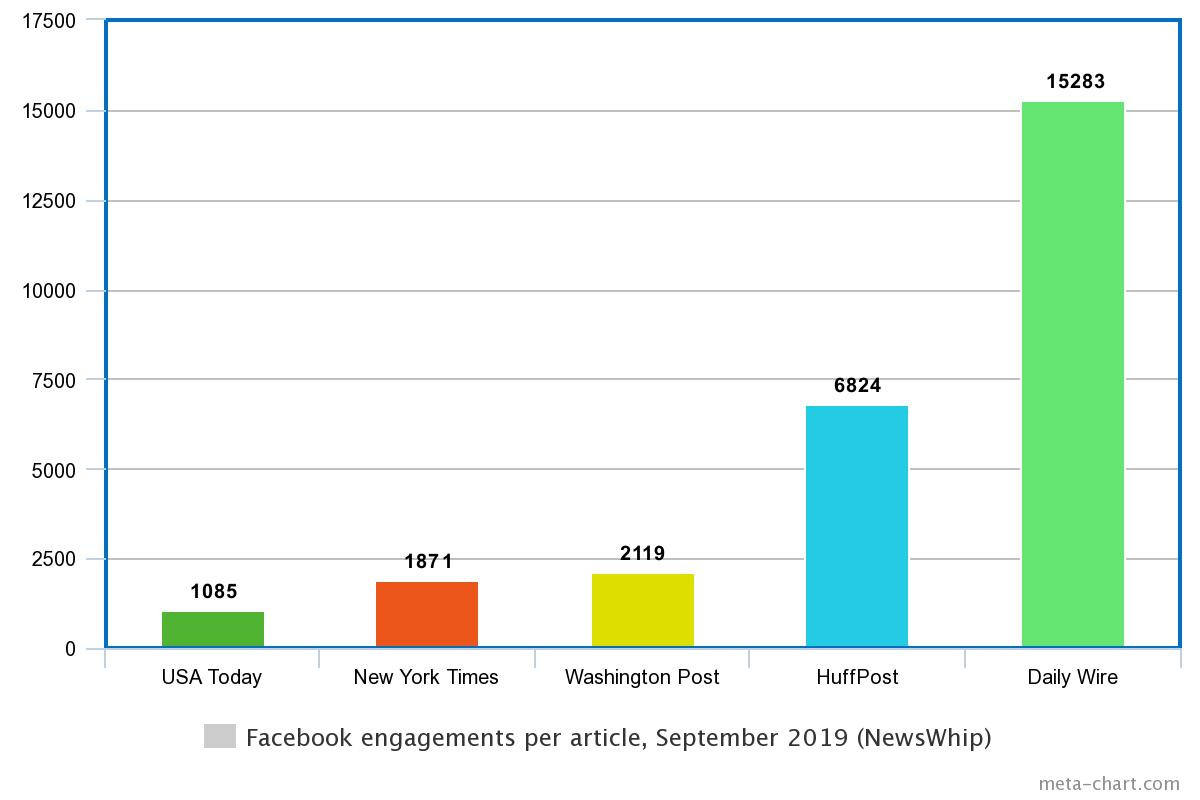
 ut this issue is getting to be old news. Just this past week, Facebook put up this web page, accompanied with full-page newspaper ads claiming that they are on the side of small businesses. They are going after Apple’s attempt to eliminate tracking cookies and make your mobile activities more private. Apple has proposed a pop-up warning when it detects a cross-site cookie, with this mockup. One analysis of the conflict says this illustrates Apple and Facebook’s different approaches to privacy and whether endusers or advertisers will foot the ultimate bill. Regardless, the irony and shameless factor from both companies is too much.
ut this issue is getting to be old news. Just this past week, Facebook put up this web page, accompanied with full-page newspaper ads claiming that they are on the side of small businesses. They are going after Apple’s attempt to eliminate tracking cookies and make your mobile activities more private. Apple has proposed a pop-up warning when it detects a cross-site cookie, with this mockup. One analysis of the conflict says this illustrates Apple and Facebook’s different approaches to privacy and whether endusers or advertisers will foot the ultimate bill. Regardless, the irony and shameless factor from both companies is too much.Avast blog: The dangers of Adrozek adware
 Microsoft has found that various browsers are being targeted with ad-injection malware called Adrozek. At the attack’s peak in August, the malware was observed on more than 30,000 devices every day, according to the researchers. The adware, as it is called, substitutes phony search results that when clicked will infect your computer.
Microsoft has found that various browsers are being targeted with ad-injection malware called Adrozek. At the attack’s peak in August, the malware was observed on more than 30,000 devices every day, according to the researchers. The adware, as it is called, substitutes phony search results that when clicked will infect your computer.
You can read my analysis of the malware and what you can to prevent it in my latest blog post for Avast here.
Network Solutions blog: The Best IT Certifications to Maximize Your Personal ROI
 As teaching methods advance and especially during the pandemic, online learning is starting to approach a physical classroom experience, and it’s great for conceptual learning. A good online learning experience should include not only content, but should also feature practice drills, integrate with real-world case studies, and contain a social component to make learning more effective. I cover some of the things to look for in selecting the right professional IT certifications to increase your potential value to your company.
As teaching methods advance and especially during the pandemic, online learning is starting to approach a physical classroom experience, and it’s great for conceptual learning. A good online learning experience should include not only content, but should also feature practice drills, integrate with real-world case studies, and contain a social component to make learning more effective. I cover some of the things to look for in selecting the right professional IT certifications to increase your potential value to your company.
You can read my blog for Network Solutions here for more about this topic.
Instant Messaging interoperability is still a big ask
 Back in 2006, I wrote various articles about the interoperability of instant messaging (IM) among various proprietary systems. Back then, we had the likes of AOL IM, Skype (before being acquired and perverted by Microsoft), Google Talk (before being perverted by Google into its Hangouts) and Apple’s iChat (before being perverted into iMessage). This was before WhatsApp and various Chinese products were even created and are now the default IM and telecom tools that are used by millions.
Back in 2006, I wrote various articles about the interoperability of instant messaging (IM) among various proprietary systems. Back then, we had the likes of AOL IM, Skype (before being acquired and perverted by Microsoft), Google Talk (before being perverted by Google into its Hangouts) and Apple’s iChat (before being perverted into iMessage). This was before WhatsApp and various Chinese products were even created and are now the default IM and telecom tools that are used by millions.
Back then, the major messaging tool was SMS. But in the US, it was only after 2000 when the various cellular providers could exchange messages across the different cellular provider networks. Fortunately, the EU had led the way in figuring out that their systems had to talk to each other, largely thanks to a single cellular standard that was then adopted around the world.
Today we have the beginnings of a new interoperability effort, once again being pushed by the EU digital regulators. This time it is under a new series of laws, one of them called the Digital Services Act. The idea is to force the various IM vendors into playing nice with each other. While the proposed EU regs haven’t yet been set, they are concerned about the concentration of power and market share by Facebook.
If the EU is going to solve IM interop, they will need to look at various dimensions, as I first defined them back in 2006:
- Text messaging, of course, among the various IM networks (as well as among the SMS networks too) — both in 1-to-1 and among various groups,
- File transfer, the ability to move digital files, such as documents and photos, from one IM network to another,
- Multi-party video and audio conferencing, with participants connecting to different IM networks,
- Audio chats, similar to regular one-to-one phone calls, and
- Chat, messaging and voice mail recording features too.
Granted, that is a big ask. But if we are going for interop, we might as well stake out the territory.
Most of the products that I mentioned back in 2006 have changed significantly as I hinted at in my introduction. They were designed in an era when interop wasn’t even thought of as a possibility. The sad reality is that it still isn’t.
As I said, the genesis of today’s IM interop is simple: Facebook now owns everything, and it is time to make a more level playing field. What the capital markets couldn’t accomplish, we will now have government to the rescue. Does anyone think this is going to work? But don’t despair, let’s look at what is happening with Microsoft. Their Teams product has begun to move in the right direction by working with ways to interop with Webex video conferencing equipment. This is because Teams is playing catchup with Webex and needs to gain market share. Teams is also competing with IP telephony, but let’s put that aside for another blog post.
There are other ways around IM interop, and one way (which was attempted back in the early 2000’s) was to have multi-lingual IM apps. Two of them that are still around are:
- Adium, which supports AOL IM, Twitter, and Google Talk and has some basic support for WhatsApp and Telegram, and
- Trillian, which requires a separate server to provide the connections among services.
They are still around largely because they have a dedicated crew of volunteer programmers willing to keep them current. Most of the other multi-lingual commercial products have gone by the wayside. Again, will EU regs help or hinder (or not have any effect) on this market? It will be interesting to watch these developments.