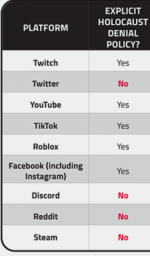
 A new report from the Anti-Defamation League has reviewed the stated hate speech policies of nine different social media platforms. Unlike other studies, it also tests their responsiveness to user reports of violations of those policies. The ADL is an organization that has been operating for more than 100 years trolling (literally) these waters. They were specifically interested in how social media propagated posts made by Holocaust deniers across their networks. They scored each platform in terms of intentions and how they performed in terms of preventing hate speech on such issues such as:
A new report from the Anti-Defamation League has reviewed the stated hate speech policies of nine different social media platforms. Unlike other studies, it also tests their responsiveness to user reports of violations of those policies. The ADL is an organization that has been operating for more than 100 years trolling (literally) these waters. They were specifically interested in how social media propagated posts made by Holocaust deniers across their networks. They scored each platform in terms of intentions and how they performed in terms of preventing hate speech on such issues such as:
- Did the platform investigate the report and promptly respond (defined as within 24 hours) to the complaint?
- Do users of each platform understand why it has made a certain content decision based on its stated policies?
- Did the platform take any actual action once something was reported?
You can see a part of their report card above. Before I get to the grades given for answering these and other questions, I want to talk about my own personal experience with Holocaust denial. About four years ago, my sister and I went to Poland to see the places where our mom’s family came from. One of our cousins did some genealogy research and found an ancestor who lived in a small town in northeast Poland who was a rabbinical judge back in the 1870s. One of the stops on our trip was to visit Auschwitz, and you can read my thoughts about that day here.
One of the exhibits at the site was about the German engineering firm that designed the mass extermination equipment. For years, the copies of the original drawings used to build this gear were kept from public view by the denier network. But eventually they were sold to someone who flipped from being a denier to someone who realized the legitimacy of these plans, and that’s how we were able to finally see them.
Several years ago I attended a lecture by Jan Grabowski, a history professor from Ottawa. He has done extensive research into Polish Holocaust history, despite the current denier political climate where he and his research associates and colleagues have been threatened and in some cases jailed for their work. Grabowski is affiliated with the Polish Center for Holocaust Research in Warsaw which is attempting to find primary source records to document what happened during those dark times. Add to this a recent survey of millennials that found that 56% of the respondents could not even identify what Auschwitz was about.
From these two personal moments, I realize that we need more evidence-based approaches and to disseminate facts rather than fiction or misdirection. That is where the social networks come into play, because they have become the superhighway of these fictions. Let’s not even glorify them by using the term “alternative facts.”
Let’s return to the report card. Sadly, only Twitter and Twitch acted against the Holocaust denial content reported. No network got any A grades across the ADL’s rubric, to no surprise. Twitch, the gaming social network, scored B’s. Twitter and You Tube got C’s. Facebook and others received grades of D.
Based on its research, the ADL has some recommendations:
- Tech companies must make changes to their products to prioritize users’ safety over engagement and reduce hateful content on their platforms.
- All the platforms need to do a better job on transparency. They should provide users with more information on how they make their decisions regarding content moderation. This is especially urgent, given the recent decisions to terminate several high-profile accounts.
You can read others at the link above. My final point: yes, censoring hate speech — whether it about the Holocaust or whatever — is destructive to our society. Just look at the mob that swarmed across our Capitol earlier this month. The social networks have to decide whether they can step up to the task. And while it bothers me that we have to censor the most dangerous of hate speakers, we do have to recognize their danger.
 You might have missed the news about a
You might have missed the news about a  One of the most popular attack methods in IT security starts with posing a simple question: How many places in your IT infrastructure have administrative access? Unfortunately, getting to the bottom of answering this question is anything but simple, but it can be instructive. This is because understanding administrative access is perhaps one of the most important ways to defend your business computing network.
One of the most popular attack methods in IT security starts with posing a simple question: How many places in your IT infrastructure have administrative access? Unfortunately, getting to the bottom of answering this question is anything but simple, but it can be instructive. This is because understanding administrative access is perhaps one of the most important ways to defend your business computing network.
 In any given week, security researchers discover caches of data on cloud servers that are completely open to the public, usually containing the most sensitive information about a company’s customers. Leaks were found earlier this summer that revealed data coming from
In any given week, security researchers discover caches of data on cloud servers that are completely open to the public, usually containing the most sensitive information about a company’s customers. Leaks were found earlier this summer that revealed data coming from  In the past week, we have seen the takedown of a social network by its largest technology partners. I refer to Parler, of course. The events weren’t entirely a surprise, but their velocity and totality were unusual.First, Apple and Google removed the Parler apps from the iTunes and Play stores. Then, its hosting partner, Amazon, shut down its servers on Amazon Web Services. I
In the past week, we have seen the takedown of a social network by its largest technology partners. I refer to Parler, of course. The events weren’t entirely a surprise, but their velocity and totality were unusual.First, Apple and Google removed the Parler apps from the iTunes and Play stores. Then, its hosting partner, Amazon, shut down its servers on Amazon Web Services. I