 I am getting close to hitting the pandemic wall. Like many of you, I have been trying to be safe, following the rules, limiting my social contacts. Not getting on planes, going to any f2f meetings or even driving very much. I think last year my wife and I put a grand total of 6,000 miles on our car. So here is my current fantasy: becoming a digital nomad and living in some foreign country.
I am getting close to hitting the pandemic wall. Like many of you, I have been trying to be safe, following the rules, limiting my social contacts. Not getting on planes, going to any f2f meetings or even driving very much. I think last year my wife and I put a grand total of 6,000 miles on our car. So here is my current fantasy: becoming a digital nomad and living in some foreign country.
It is very ironic, this fantasy, because to some extent I already am a digital nomad, just without any of the nomadic travels. I have had my own freelance writing and speaking business now for several decades, but always have had a nearby office. (Mine is across the street from my home, but it could be anywhere in the world). Yet all my work is done for clients remotely. In some cases, I haven’t ever met some of them f2f. I was talking about this with my accountant, who lives just a few miles away. She and I have worked together for more than a decade but have never physically met.
In years past, I was semi-nomadic: I did a fair amount of travel to industry events, to speak at conferences, or to work with my clients at their offices. But now, thanks to the pandemic, that is all off the table. There is also an upside to the pandemic though: some companies have loosened their remote work restrictions and no longer care where in the world you work, just as long as you have the connectivity, the tools, and the time zones that you consider part of your workday firmly in place. This last issue is important: if your employer expects to find you at your desk or online at a certain time, you need to structure your day accordingly, wherever in the world you might be.
If you are considering becoming a digital nomad, you might want to study up on how to make the transition, as well as to figure out where in the world the Global You HQ will set up shop. Now is certainly the time to think about this, especially as many countries are trying to make it easier for nomads to settle – in some cases for years or more. Here are two resources that have the most current info on which countries are offering this arrangement, one from GodSaveThePoints and one from TravelOffPath. The list is somewhat fluid, as countries are changing the rules and evolving their Covid restrictions often at the same time. You can see some countries have placed income requirements: they want to attract nomads who have resources and income to come, and who will continue to work and earn their livings there. If you are just starting to think about becoming a digital nomad, there are dozens of blogs that describe the process, such as this one on TwoWanderingSoles.
In the past, pre-pandemic, nomads usually worked in a country under the radar, using 90-day tourist visas. You can still do this, if you understand that when the time is up, you literally must pack your bags and get out of Dodge. You can then find your next post and take up another 90-day residency. But that can get tiresome. And it could be risky: in these Covid times, you might not be able to get on any flights and then you would be in trouble when you try to leave on an expired visa. So that is where the digital nomad visa comes into play. Actually, the name is somewhat misleading, because it really is a temporary residency permit for an extended period of time.
I spoke to Bryan Cooley, who is a serial tech entrepreneur that I met when he was living in St. Louis. He has lived in various places around the world and now spends half the year in Manila as a permanent resident. He has spent at least a week in more than 130 countries and dozens where he has lived at least a month. I asked Bryan about his Internet connectivity, and he told me it has never been an issue. “I have had better connectivity than back in the US, even in some very remote areas.” Certainly, Covid has disrupted his travel plans: for example, even though he is a permanent resident in the Philippines, under current rules he can’t return if he leaves during the pandemic. He is looking into getting residency in Australia. He feels the digital nomad visas are mostly marketing efforts: “There are so many people traveling and going where they want to live. It has been going on for a long time. These programs are very limited in terms of numbers.”
A tech writer colleague of mine, Sharon Fisher, decided to go nomadic last fall, and has been to both Aruba (from October to January) and is now in Bermuda with her partner. I asked her how she ended up in these two places. She said that first she examined if Americans could enter the country, how their Covid cases were being handled, and what kind of broadband internet was available. Part of her Covid research was in understanding how onerous their quarantine protocols were. “We didn’t mind testing and staying home for a while, but we didn’t want to have to each pay $5000 to be sequestered for 14 days in a specific hotel on arrival.”
Next, they looked at the AirBnB situation, and so far they have had great experiences with the hosts they stayed at. They also need to have a close time zone to US operations: “we looked at Saipan (an island in the middle of the South Pacific) but that meant having to work in the middle of their night,” she told me.
Her biggest issues so far were groceries, transportation and bandwidth. “Food is more expensive than we anticipated, milk and produce in particular. Rental cars in Aruba were expensive but necessary. There are no rental cars in Bermuda, so we take the bus. Internet has been fine in the AirBnBs, including streaming video, with two people using the Internet just about constantly.” They also have T-Mobile cellular coverage which enables international data roaming but they eventually bought local SIM cards in Aruba.
What about her travel in the time of the Covid? “Ironically, it’s actually kind of been easier because Covid has reduced the number of choices we’ve had to make, and everyplace is less crowded. But the hardest part about traveling now is the existential question of ‘should we be doing this?’ The people in Aruba were very appreciative that some travelers were still coming, because of how dependent their economy is on tourism. Also, both countries have had much lower incidences of Covid than where we were in the US, and people seem to take it far more seriously. We personally have been much safer in these countries than we would have been in the US, and we have taken all the steps we can to ensure that the people in the other countries are safe as well. We realize what a privilege we have, and we appreciate it.”
If you are thinking about becoming a nomad, here are a few more points that I want to make. First, learn as much about the expat culture of your target destination. There is a difference between expats – people from elsewhere who intend to live there for the long haul – and nomads, who might not want to stick around or who want to travel as part of their newfound freedom. Bryan mentioned these communities might not be everyone’s cup of tea: “there are a lot of nomads who don’t really know what they are doing.”
Second, look at places that are specifically focusing on startups, such as Madeira. Their website offers links to coworking places, long-term housing rentals, and other aspects of their support for digital nomads. Yes, the number of people that will be accepted to this program is small, and Americans can’t yet travel there — but it represents an interesting step in the nomad field. Next, don’t forget about your digital entertainment. If you expect your streaming services to deliver the same programming you have gotten in the US you might want to experiment with various VPNs. Also, understand the Covid vaccination program at your destination. Sharon mentioned that her “current plan is to stay in Bermuda through March, return to the US, get vaccinated, then see what options we have. If we aren’t yet able to get vaccinated, we will likely stay in Bermuda until we can. So far as I know we can stay for up to a year.”
Finally, learn about the changes that the EU has in store for its visa requirements in the near future. That could influence how your plans evolve once we are finally out of the pandemic.
 A novel experiment in deploying large-scale trusted data networks has begun in Helsinki, the capital of Finland. A variety of city services have been linked together using the open-source MyData Global solution, it was announced earlier this month. This puts city at the forefront of how it gathers data from its citizens and how it stores and uses the data. The goal is to give each person control over how their data is shared with various city agencies.
A novel experiment in deploying large-scale trusted data networks has begun in Helsinki, the capital of Finland. A variety of city services have been linked together using the open-source MyData Global solution, it was announced earlier this month. This puts city at the forefront of how it gathers data from its citizens and how it stores and uses the data. The goal is to give each person control over how their data is shared with various city agencies.

 The FDA has appointed Kevin Fu its first Acting Director of Medical Device Cybersecurity in the Center for Devices and Radiological Health. This center has several bodies, including the CyberMed Safety Board, the
The FDA has appointed Kevin Fu its first Acting Director of Medical Device Cybersecurity in the Center for Devices and Radiological Health. This center has several bodies, including the CyberMed Safety Board, the 
 Sandbox security is complementary to honeypots. It usually involves a special VM that is kept in isolation from the rest of your network resources. Its sole purpose is to be a miniature laboratory to observe malware behavior. Security researchers have been using such sandboxes to analyze malware for many years. Because the sandbox is a controlled environment, its code can be dissected line by line without worrying about potential harm to other computers.
Sandbox security is complementary to honeypots. It usually involves a special VM that is kept in isolation from the rest of your network resources. Its sole purpose is to be a miniature laboratory to observe malware behavior. Security researchers have been using such sandboxes to analyze malware for many years. Because the sandbox is a controlled environment, its code can be dissected line by line without worrying about potential harm to other computers.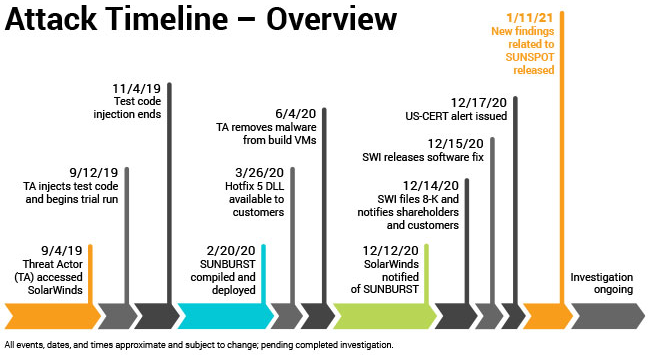

 The results of Paul’s informal census is that folks can’t wait to get back to F2F. We all have been in our pandemic bubbles for far too long and the urge to have human contact and serendipitous hallway meetings is a big reason to return to the rubber chicken circuit. But we’ve all learned a lot in the meantime about what makes virtual events successful. At its heart, you are putting on a live TV show with a very small staff to handle the production. You need to plan accordingly on the mixture of live and pre-recorded segments and figure out what tech you are going to use, including the video conferencing and the event management tool. (The two are different and you should understand the differences, which I explain in my paper.)
The results of Paul’s informal census is that folks can’t wait to get back to F2F. We all have been in our pandemic bubbles for far too long and the urge to have human contact and serendipitous hallway meetings is a big reason to return to the rubber chicken circuit. But we’ve all learned a lot in the meantime about what makes virtual events successful. At its heart, you are putting on a live TV show with a very small staff to handle the production. You need to plan accordingly on the mixture of live and pre-recorded segments and figure out what tech you are going to use, including the video conferencing and the event management tool. (The two are different and you should understand the differences, which I explain in my paper.)