Almost 30 years ago, two computer geeks – Marshall Rose and Carl Malamud — put together the first wide-scale attempt at sending faxes over the internet. In the beginning, it was fairly modest, with service reaching a few select cities in the USA and Canberra Australia. The two geeks were fans of the campy 1960’s movie “The President’s Analyst” which was why they named their venture TPC.INT. If you haven’t ever seen a .INT domain name, here is a list of them according to Wikipedia, they are websites for various international organizations. In true Rose/Malamud fashion, they wrote a series of internet RFCs (here is one) to document how the thing worked. (Here is a short history of TPC.INT domain and here is a collection of the first set of faxes they received at their launch.) It relied on a series of volunteers who would have internet-connected  computers that would connect to a standard phone line and make local fax calls (this was before long distance VOIP lines were common, let alone cell phones) and make a call to an actual fax machine. The duo called TPC “an experiment in remote printing” because that was the concept: sending a document to a fax-based “printer” that was located at some other place in the world.
computers that would connect to a standard phone line and make local fax calls (this was before long distance VOIP lines were common, let alone cell phones) and make a call to an actual fax machine. The duo called TPC “an experiment in remote printing” because that was the concept: sending a document to a fax-based “printer” that was located at some other place in the world.
 While TPC was getting together, PC component vendors were building in fax modems as part of their overall modem electronics. For those of you that think a modem is what connects you to the internet through your cable or DSL provider, back in the dial-up days we had modems that plugged into ordinary analog phone lines. One of the first successes was add-in board from Intel that was called SatisFAXtion. This allowed you to fax directly from your DOS applications. Here is a box shot of the adapter.
While TPC was getting together, PC component vendors were building in fax modems as part of their overall modem electronics. For those of you that think a modem is what connects you to the internet through your cable or DSL provider, back in the dial-up days we had modems that plugged into ordinary analog phone lines. One of the first successes was add-in board from Intel that was called SatisFAXtion. This allowed you to fax directly from your DOS applications. Here is a box shot of the adapter.
Anyway, those early experiments brought about an entire service industry that is now dominated by the likes of eFax and jFax. While TPC was just for sending faxes via email (and later via a web browser), these services have expanded to also receiving them (via a fax-to-email interface) and using a variety of modalities, including your mobile phone, cloud storage and dedicated clients.
Along the way, I wrote a few articles for businesses that wanted to use these services, such as “Faxing on the Go” in 1999 for Computerworld and another column for PC World about their basics in 2009. For years I maintained a table comparing services on my website, but given that there are so many places to find more in-depth reviews of these services (including PC Magazine, Tom’s Hardware, and NYTimes’ Wirecutter, just to name three), I gave up trying to keep the table current. If you are looking for an internet fax provider take a look at the Tom’s review. If you scroll down, they will help you frame your decision (do you need multiple inbound fax numbers, custom cover pages, searchable archives, and so forth). The two services that I currently use are eFax (I got on board their free service and still have a working inbound fax number) and FaxZero (which is great for the once-in-a-blue-moon frequency that I need to send faxes). The three review sites have their favorites based on various criteria.
Why was I thinking about internet fax? Last week I was opening a new IRA account. I began with a simple online application, then I needed to send in some documents to the bank. My delivery choices were as follows:
- A secure file upload web portal
- Sending regular postal mail with my check (not a good idea, given the state of the USPS these days)
- Sending an overnight letter (to a different address than above, of course)
- Or sending a fax.
If I used the portal or fax, I would need to talk to a bank representative to provide my existing bank account that they could use to collect the funds. I chose the portal. The experience was far from seamless, which is more a matter of why fax continues to this day. It seems when I have to deal with a bank, an insurance company, or a doctor’s office, all of them still use faxes.
Certainly, we have come a long way since those early days when fax machines used special paper that would fade in strong sunlight. And while there are a number of ways to securely send files (as I wrote about recently for The Verge here), sending a fax is still a lot easier.
![]() The most comprehensive source remains the above annotated map from Husch Blackwell, which will link you to each state’s legislation. If you are looking for more analysis, this page from the National Conference of State Legislatures has more contextual explanations.
The most comprehensive source remains the above annotated map from Husch Blackwell, which will link you to each state’s legislation. If you are looking for more analysis, this page from the National Conference of State Legislatures has more contextual explanations.

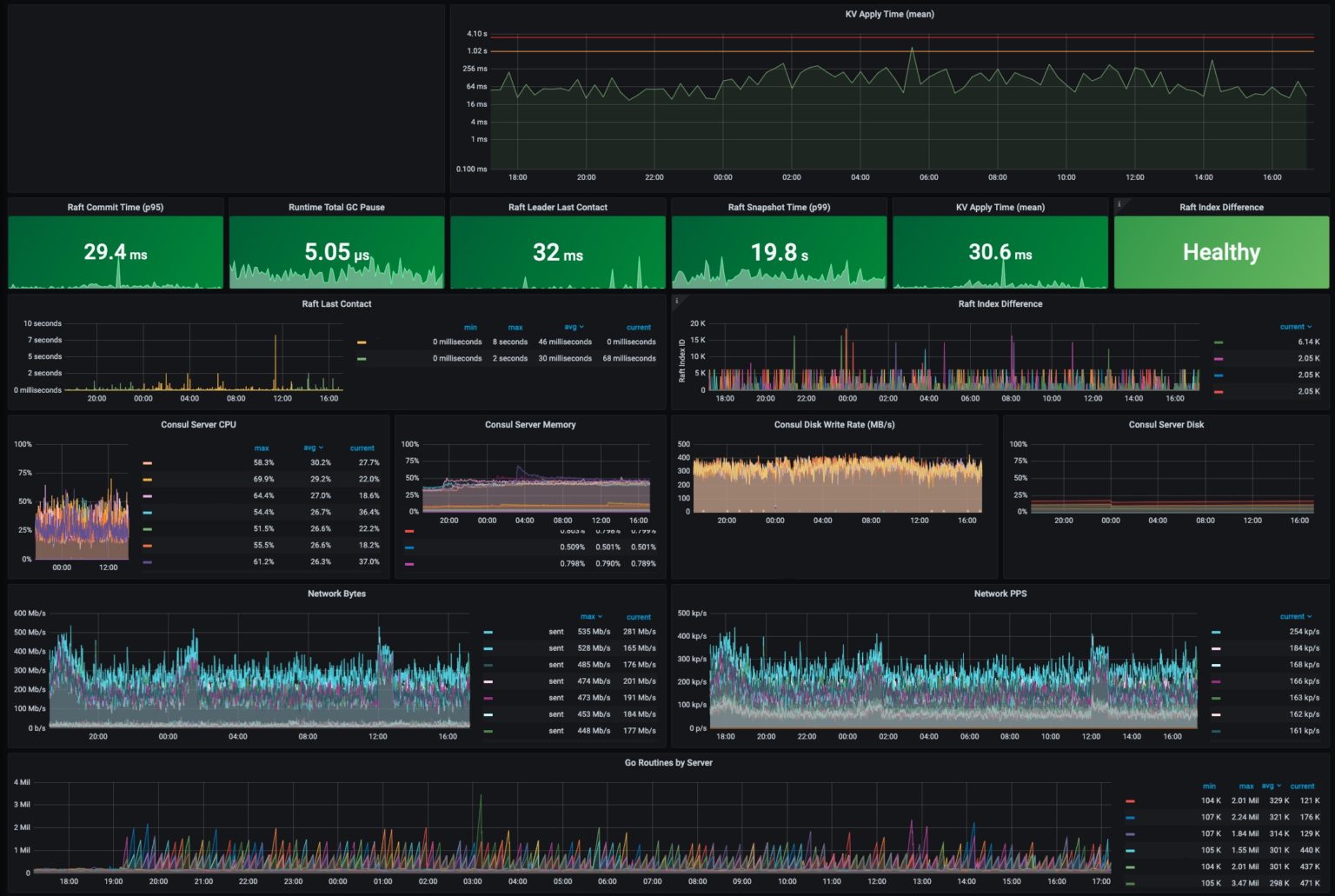 Last October the gaming company Roblox’s online network went down, an outage that lasted three days. The site is used by 50M gamers daily. Figuring out and fixing the root causes of this disruption would take a massive effort by engineers at both Roblox and their main tech supplier, HashiCorp. The company eventually posted an amazing analysis on
Last October the gaming company Roblox’s online network went down, an outage that lasted three days. The site is used by 50M gamers daily. Figuring out and fixing the root causes of this disruption would take a massive effort by engineers at both Roblox and their main tech supplier, HashiCorp. The company eventually posted an amazing analysis on 
