Late last month the Indian CERT issued a ruling directed at improving its breach security. The ruling has some big impact in terms of limiting the privacy of its computer users, and how digital business is conducted there. The news has centered around its effect on VPN operators, but the ruling also affects data center providers and “intermediaries,” which could be any ISP or indeed any digital business that has Indian origin. The ruling isn’t final but is supposed to go into effect next month.
— First, businesses must notify the CERT within six hours of any breach or security incident, and provide any system logs that have to be maintained for six months. These incidents are described across a wide collection of situations, including website defacement, identity theft, DDoS, data theft, wholesale port scans and other attacks. The six-hour window is a pretty tight one, and other geographies have much longer notification periods (The EU’s GDPR is 72 hours for example.), and in some cases, businesses may not even know of a breach during that short time period.
— Second, digital businesses must collect log a variety of user data, including valid names, IP addresses, public encryption keys, emails, physical address and phone contacts. CERT requests that any vendor keep these logs for up to five years. The businesses specifically mentioned in the ruling include remote access vendors, VPN operators, cloud providers and data centers. But it could apply to any company that has a bunch of programmers in India, which is certainly a common situation for perhaps most large international companies.
The actual logs are being collected to enable the CERT to reconstruct individual transactions so they can identify the parties involved. That is a tall order, because it assumes that businesses will have to collect a lot more data about their customers than they have done previously.
As you might imagine, this has thrown many businesses into a tizzy, because of the onerous provisions in this ruling. What is curious is that the role of India’s CERT has moved beyond its lane, which is typically the national agency (our CERT which began its operations in Pittsburgh) that handles breach reporting and makes recommendations when they are observing increases in computer attacks.
The five-year log collection period is what I want to focus on. As I said at the top of this post, the news has mostly focused on VPN providers, and indeed they have reacted with some trepidation. Some have said they might have to forgo their Indian operations. “Forcing VPN providers to track user traffic and their private data is going to invalidate one of the last remaining safeguards of personal privacy on the public internet while helping to expose only a handful of lawbreakers,” said Artur Kane, the CMO at VPN provider GoodAccess.com.
The data retention piece of the regulation is also an issue. Part of the issue, as I mentioned in my earlier reviews of VPNs, is that figuring out data retention policies and practices is very difficult, and almost every vendor has problems here. But there is another side as well: “Asking VPN vendors to retain this amount of customer data is without precedent in democratic countries” Kane said.
Many VPN providers have claimed “no logs” as part of their marketing strategies. This is almost as ridiculous and nearly unprovable as their claims for “military-grade encryption.” CNet wrote this piece a few years ago about why you should be so skeptical about these claims — there are numerous types of logs, and numerous ways to collect and dispose of this data. “No matter how much we trust any particular VPN to help mask our internet browsing, it’s virtually impossible to verify whether a VPN truly keeps no logs,” they wrote. I agree. If you want to research this further, read this analysis by Consumer Reports on how many VPNs keep local logs (on your own machine).
While getting better intelligence about cyber attacks is important, the way the Indian CERT is going about this is wrong-headed, and perhaps will prevent many companies from continuing to do business in India.
 As more communities install automated license plate readers (APLRs) to monitor vehicle traffic, there are growing concerns about the privacy and efficacy of these tools. Stories have appeared in local newspapers, such as those in St. Louis, Louisville and Akron that document the rapid rise of Flock license plate camera data and how it can be a central source of vehicle movements.
As more communities install automated license plate readers (APLRs) to monitor vehicle traffic, there are growing concerns about the privacy and efficacy of these tools. Stories have appeared in local newspapers, such as those in St. Louis, Louisville and Akron that document the rapid rise of Flock license plate camera data and how it can be a central source of vehicle movements. If you have heard of the process of social engineering, the ability of a hacker to trick you into divulging your private details, then you might have come across ethical hacker
If you have heard of the process of social engineering, the ability of a hacker to trick you into divulging your private details, then you might have come across ethical hacker 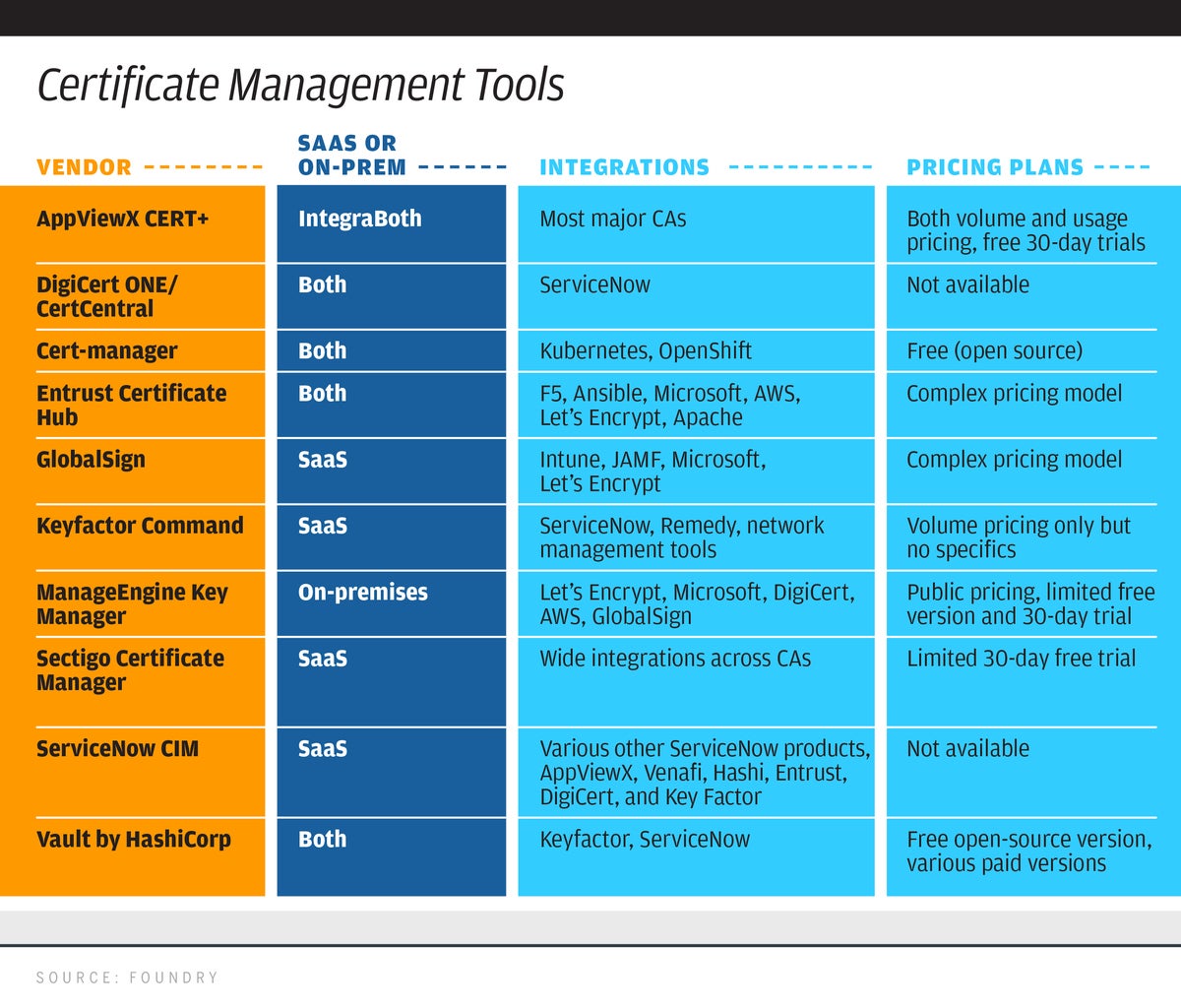
 Saving lives isn’t just some abstract concept for the American Red Cross. Volunteer Brian Mintner not only delivers lifesaving blood to people he’ll never meet, he is directly responsible for saving one specific life. Brian is the manufacturing transportation supervisor for the Missouri-Arkansas region of the Red Cross, coordinating the movement of blood products collected from donors and ensuring they are transported to various hospital blood banks. He oversees a vast transportation network that, he admits, “is a brutal chain of custody.”
Saving lives isn’t just some abstract concept for the American Red Cross. Volunteer Brian Mintner not only delivers lifesaving blood to people he’ll never meet, he is directly responsible for saving one specific life. Brian is the manufacturing transportation supervisor for the Missouri-Arkansas region of the Red Cross, coordinating the movement of blood products collected from donors and ensuring they are transported to various hospital blood banks. He oversees a vast transportation network that, he admits, “is a brutal chain of custody.” The killing of Al Jazeera veteran journalist Shireen Abu Akleh last week has haunted me in the days since it happened. She was covering a raid by Israeli forces in the refugee camp of Jenin in the West Bank. For specifics about what happened, I would urge you to
The killing of Al Jazeera veteran journalist Shireen Abu Akleh last week has haunted me in the days since it happened. She was covering a raid by Israeli forces in the refugee camp of Jenin in the West Bank. For specifics about what happened, I would urge you to