By David Strom and David Strom
No you are not seeing double: we are two different people. Democrat David Strom and Republican David Strom.
Having a well-worn internet presence means that after some time, you get to meet some of your namesakes. Since both of us are authors (Minneapolis David is a Republican who writes on conservative political topics. And as you know me — St. Louis David — as a Democrat who writes about business technology), we thought we would jointly pen a blog post about things that we can both agree on — and where we diverge as well — for our respective audiences. We found these five broad topics.
1) A path towards legal immigration
We both agree that our immigration laws should be updated to allow for a legal path towards citizenship for those who come to our country. That leaves plenty of daylight between us in terms of how this will be implemented, but both of us aren’t happy with the current situation.
Minneapolis David: It’s not just a truism that immigrants built this country–they continue to make enormous contributions to America. But you can have too much of a good thing, and as we have seen open borders have created a crisis that is splitting this country apart. It’s time to get control of our border and a consensus on the number of immigrants the country can import without causing social distress.
St. Louis David: I was surprised when I learned how few countries offer birthright citizenship. We need some consistent policy among the various government branches and across federal, state and local authorities. Wishful thinking, I know.
2) Respect for the rule of law and individual decency
BOTH DAVIDS: Calling for the overthrow of our government by anyone shouldn’t be tolerated. The same holds for threatening law enforcement members, or members of Congress, or really anyone for that matter. We should tolerate people of different points of view — one of the reasons why we are jointly writing this blog post. (Democrat David is married to a conservative Republican, BTW.) And by tolerate we mean being able to disagree without the threat of any violence on that person.
Talk of a civil war–and the increasing number of violent incidents related to political disagreements–make solving real problems nearly impossible. Distrust begets distrust. Neither of us have any idea how to solve the problem, but we need to get a handle on it. Political leaders need to take the first step to calm down the rhetoric.
3) Understanding the role played by the First Amendment and freedom of speech
Until this year, this amendment only applied to government entities. Now we have two court rulings in Texas and Florida that have different interpretations when it comes to the role of social media and how freedom of speech protections should apply. We both deplore and avoid hate speech.
St. Louis David: Regardless of how these cases play out, all of us should be allowed to say what we want, as long as we aren’t promoting violence on a particular group.
Minneapolis David: Maybe I read John Stuart Mill at an impressionable age, but I have long believed that the more you suppress ideas, the more disastrous the outcome. Let people speak. Some people will say things that are wrong, stupid, or just different from what you think is responsible. A lot of people will think the same of you. Deal with it.
4) Importance of science research and respect for the scientific method
St. Louis David: This should be easy. Those people who want to “do their own research” or criticize our scientists for explaining a particular result should fully understand the scientific method of testing hypotheses and running double-blind experiments. Part of respecting scientific research is believing that innovation is a key element of this activity, and accepting the role played by innovation in our society. We may differ on how our governments implement these results, however. Neil DeGrasse Tyson offers some sound advice in his latest book: “Do whatever it takes to avoid fooling yourself into believing that something is true when it is false, or that something is false when it is true.”
Minneapolis David: I agree with St Louis David, with a big “but.” I think that scientists have played a big role in the loss of trust in science. Science is about discovery. Its results are better or worse hypotheses. The goal is truth, but we can only approximate the truth asymptotically (look it up!). Scientists need to project more humility, or their mistakes will only undermine confidence. Example: nutrition science, where it seems like they get it wrong all the time, but with great confidence.
5) Respect for life
Both of us agree that we should respect life, which we hinted at above. But we realize that we all might have different definitions of what constitutes the precise moment when we think it begins or ends. Polling shows that there is ample room for reasonable compromises.
St. Louis David: I believe that our government should allow women to choose, and not make their choices a criminal act.
Minneapolis David: I consider myself “pro-life” in the sense that you know it. I also understand that there are legitimate differences about how we can best determine when life begins. We need to get beyond shouting at each other and have serious discussions, not shouting matches.
One final note on something we can also agree on: both of us are Mac/iPhone users, and both of us have re-invested in Apple products this past year.
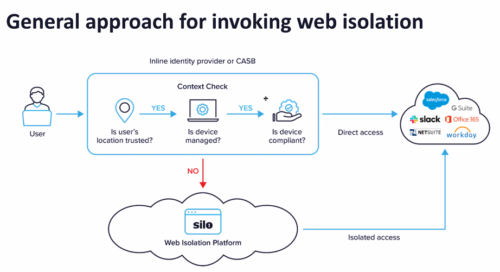 The web browser has long been the security sinkhole of enterprise infrastructure. While email is often cited as the most common entry point, malware often enters via the browser and is more difficult to prevent. Phishing, drive-by attacks, ransomware, SQL injections, man-in-the-middle, and other exploits all take advantage of the browser’s creaky user interface and huge attack surface, and the gullibility of most end users.
The web browser has long been the security sinkhole of enterprise infrastructure. While email is often cited as the most common entry point, malware often enters via the browser and is more difficult to prevent. Phishing, drive-by attacks, ransomware, SQL injections, man-in-the-middle, and other exploits all take advantage of the browser’s creaky user interface and huge attack surface, and the gullibility of most end users. I live a block away from the chess complex that was the scene of a major incident last month. This is when world chess champion Magnus Carlsen (at left) literally walked off a match that he was losing to Hans Neimann, claiming Neimann was cheating with a remote computer. This week, Neimann is back in town for another chess match.
I live a block away from the chess complex that was the scene of a major incident last month. This is when world chess champion Magnus Carlsen (at left) literally walked off a match that he was losing to Hans Neimann, claiming Neimann was cheating with a remote computer. This week, Neimann is back in town for another chess match. 