 The web browser has long been the security sinkhole of enterprise infrastructure. While email is often cited as the most common entry point, malware often enters via the browser and is more difficult to prevent. Phishing, drive-by attacks, ransomware, SQL injections, man-in-the-middle, and other exploits all take advantage of the browser’s creaky user interface and huge attack surface, and the gullibility of most end users.
The web browser has long been the security sinkhole of enterprise infrastructure. While email is often cited as the most common entry point, malware often enters via the browser and is more difficult to prevent. Phishing, drive-by attacks, ransomware, SQL injections, man-in-the-middle, and other exploits all take advantage of the browser’s creaky user interface and huge attack surface, and the gullibility of most end users.
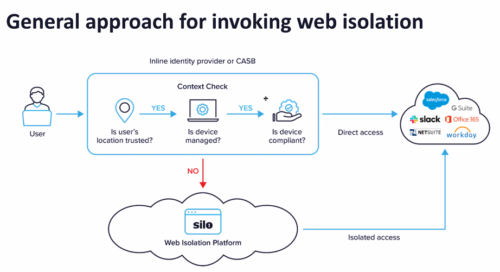
Enter the secure browser, which is available in a variety of configurations (as shown above) that can help IT managers get a better handle on stopping attackers from getting a foothold inside our networks.
I looked at four browsers in a variety of configurations in my latest review for CSOonline: