 Last week Shou Chew, the CEO of the American TikTok, was called on the US House hearing room carpet. Combining the current anti-China paranoia with social media crimes against teenagers was a potent political mix that brought a tremendous amount of bipartisan angst. The five hour hearing was attended by seemingly the entire House membership, and for me it was noteworthy in that almost none of the members were folks that I have ever heard of, but all managed to ask unanswerable questions that they demanded simple yes or no answers so they could save time for their own take.
Last week Shou Chew, the CEO of the American TikTok, was called on the US House hearing room carpet. Combining the current anti-China paranoia with social media crimes against teenagers was a potent political mix that brought a tremendous amount of bipartisan angst. The five hour hearing was attended by seemingly the entire House membership, and for me it was noteworthy in that almost none of the members were folks that I have ever heard of, but all managed to ask unanswerable questions that they demanded simple yes or no answers so they could save time for their own take.
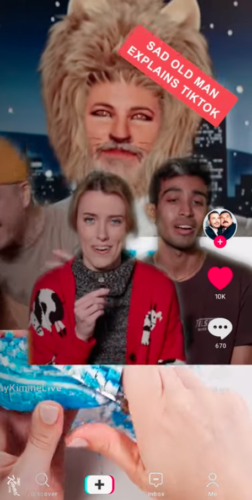
The best commentary was Jimmy Kimmel who simulated what the app does on his show (shown here at right). More insights from Casey Newton here.
Also last week, Utah became the first state to place legal restrictions on social media usage by children (<18). This law goes into effect in a year; we’ll see how they will enforce it, which will be difficult. TikTok seems to be included in its framework, although Google might not be (there is an exemption for online emails, so Gmail might not apply but YouTube might be covered).
The hearing wasn’t a total time waster. In addition to getting acquainted with our Congress (a couple of whom actually have had tech jobs, interestingly), it also brought to the public’s attention a few reports that I will highlight here. But what I saw was that America will probably join others in some form of ban, whether it be just for the government employees (as the US has done, as have the UK and France did last week) or something that is contemplated by other bills that are making their way through Congress.
Second best commentary was by security maven Bruce Schneier, who wrote last month “There’s no doubt that TikTok and ByteDance, the company that owns it, are shady. If we want to address the real problem, we need to enact serious privacy laws, not security theater, to stop our data from being collected, analyzed, and sold—by anyone.” He explored on the blog various kinds of bans, all of which would be ineffective or place Chinese-style restrictions across our internet. That message was lost on Congress, sadly. The UK ban is ineffective if you use your own Wifi or data provider, for example.
 The relationship between TikTok and its parent company was explored in detail in this report done for the Australian Senate and released earlier this month. This was cited several times by various Congress members. The research found that ByteDance should be considered as a hybrid state/private entity, collaborating closely with the government on its operations. Chew made an effort to show TikTok’s independence from its parent and the Chinese Communist Party (CCP), an effort that fell on deaf ears and “didn’t pass the smell test” as one member said. The report looked closely at two days’ worth of content last November and compared the depictions of the CCP across TikTok when compared with what was posted on Twitter, Instagram and YouTube. While the researchers couldn’t assess the cause, they did find both Twitter and TikTok had more pro-CCP content than YouTube or Instagram.
The relationship between TikTok and its parent company was explored in detail in this report done for the Australian Senate and released earlier this month. This was cited several times by various Congress members. The research found that ByteDance should be considered as a hybrid state/private entity, collaborating closely with the government on its operations. Chew made an effort to show TikTok’s independence from its parent and the Chinese Communist Party (CCP), an effort that fell on deaf ears and “didn’t pass the smell test” as one member said. The report looked closely at two days’ worth of content last November and compared the depictions of the CCP across TikTok when compared with what was posted on Twitter, Instagram and YouTube. While the researchers couldn’t assess the cause, they did find both Twitter and TikTok had more pro-CCP content than YouTube or Instagram.
Another issue is how TikTok tracks users across the internet. Consumer Reports did a report last fall that found hundreds of organizations sharing data with TikTok using tracking pixels and other canvas fingerprinting techniques. Before you sound any alarms, these are common for Facebook, Google, and numerous commercial websites, and TikTok’s tracking efforts are a small fraction of what these other companies do. Still Chew’s answers were less than satisfying in this area.
Much was made about the differences between the TikTok app we use in the USA versus the ByteDance app called Douyin that is only available in China. The excellent Citizen Lab issued a report last year that examined what data leaks from both apps. Not surprisingly, the Chinese app had more potential security and privacy issues, although the researchers said neither app had any noticeable malware characteristics.
So let’s answer some questions.
Is the TikTok app spying on its users? Not according to Citizen Lab and other security analysts. Could it become weaponized? Sure. But so could any other phone app.
What else should the government ban on its own phones? Well, if you are going to ban TikTok, how about deleting dozens of other apps that collect private data too? That is what France just did, or is trying to do. Good luck with that.
Will selling the company accomplish anything? Not really, other than improved optics. Look no further than Facebook to show misuse of data by a wholly-owned American company. Ownership doesn’t mean total control.
What about the Oracle Cloud migration? TikTok is making a big effort towards migrating its servers to the Oracle Cloud, and promises to keep all US data on these servers eventually. That clearly comes under the heading of “security theater,” since these servers can still transmit anything back to their Chinese parent company. Chew made a big deal about the Oracle project, but what he neglected to say is that any third-party code audit would be nearly impossible, since the servers started out in a pristine “bare metal” state and TikTok could put anything on them. I am not sure what is accomplished here other than having better app latency for US users. Again, a lot of effort to improve optics, but not much else.
 Last month, the Securities and Exchange Commission proposed some
Last month, the Securities and Exchange Commission proposed some  Last week Shou Chew, the CEO of the American TikTok, was called on the US House hearing room carpet. Combining the current anti-China paranoia with social media crimes against teenagers was a potent political mix that brought a tremendous amount of bipartisan angst. The five hour hearing was attended by seemingly the entire House membership, and for me it was noteworthy in that almost none of the members were folks that I have ever heard of, but all managed to ask unanswerable questions that they demanded simple yes or no answers so they could save time for their own take.
Last week Shou Chew, the CEO of the American TikTok, was called on the US House hearing room carpet. Combining the current anti-China paranoia with social media crimes against teenagers was a potent political mix that brought a tremendous amount of bipartisan angst. The five hour hearing was attended by seemingly the entire House membership, and for me it was noteworthy in that almost none of the members were folks that I have ever heard of, but all managed to ask unanswerable questions that they demanded simple yes or no answers so they could save time for their own take. The relationship between TikTok and its parent company was explored in detail in this
The relationship between TikTok and its parent company was explored in detail in this ![Stalked by Revenge (Zane Clearwater Mystery Book 3) by [Lynn Lipinski]](https://m.media-amazon.com/images/I/41tkpMWe6jL.jpg) This is the third book in a series of mystery novels featuring Zane Clearwater, a character who has had a shady past. It can be read independently of the others and there is a fourth is in the works. The story centers on Clearwater’s family, including a gun-packing grandmother and a private detective who comes to the aid of the family to stop a revengeful assailant who starts out in prison at the story’s beginning. Lipinski’s descriptive prose is first-rate, and the various characters are well drawn, with some very realistic challenges in their lives. By the end of the book you will feel that you know them and have a lot of empathy for their circumstances. Fans of mystery novels will enjoy this book, and I highly recommend it.
This is the third book in a series of mystery novels featuring Zane Clearwater, a character who has had a shady past. It can be read independently of the others and there is a fourth is in the works. The story centers on Clearwater’s family, including a gun-packing grandmother and a private detective who comes to the aid of the family to stop a revengeful assailant who starts out in prison at the story’s beginning. Lipinski’s descriptive prose is first-rate, and the various characters are well drawn, with some very realistic challenges in their lives. By the end of the book you will feel that you know them and have a lot of empathy for their circumstances. Fans of mystery novels will enjoy this book, and I highly recommend it.![A Likely Story: A Novel by [Leigh McMullan Abramson]](https://m.media-amazon.com/images/I/41GrD0EcOLL.jpg) I really
I really