I have known Dave Piscitello for several decades; he and I served together with a collection of some of the original inventors of the Internet and he has worked at ICANN for many years. So it is interesting that he and I are both looking at spam these days with a careful eye.
He recently posted a column saying “It sounds trivial but spam is one of the most important threats to manage these days.” He calls spam the security threat you easily forget, and I would agree with him. Why? Because spam brings all sorts of pain with it, mostly in the form of phishing attacks and other network compromises. Think of it as the gateway drug for criminals to infect your company with malware. A report last December from PhishMe found that 91% of cyberattacks start with a phish. The FBI says these scams have resulted in $5.3 billion in financial losses since October 2013.
We tend to forget about spam these days because Google and Microsoft have done a decent job hiding spam from immediate view of our inboxes. And while that is generally a good thing, all it takes is a single email that you mistakenly click on and you have brought an attack inside your organization. It is easy to see why we make these mistakes: the phishers spend a lot of time trying to fool us, by using the same fonts and page layout designs to mimic the real sites (such as your bank), so that you will login to their page and provide your password to them.
Phishing has gotten more sophisticated, just like other malware attacks. There are now whaling attacks that look like messages coming from the CFO or HR managers, trying to convince you to move money. Or spear phishing where a criminal is targeting someone or some specific corporation to trick the recipient into acting on the message. Attackers try to harvest a user’s credentials and use them for further exploits, attach phony SSL certificates to their domains to make them seem more legitimate, use smishing-based social engineering methods to compromise your cell phone, and create phony domains that are typographically similar to a real business. And there are automated phishing construction kits that can be used by anyone with a minimal knowledge to create a brand new exploit. All of these methods show that phishing is certainly on the rise, and becoming more of an issue for everyone.
Yes, organizations can try to prevent phishing attacks through a series of defenses, including filtering their email, training their users to spot bogus messages, using more updated browsers that have better detection mechanisms and other tools. But these aren’t as effective as they could be if users had more information about each message that they read while they are going through their inboxes.
There is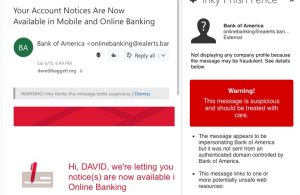 a new product that does exactly that, called Inky Phish Fence. They asked me to evaluate it and write about it. I think it is worth your time. It displays warning messages as you scroll through your emails, as shown here.
a new product that does exactly that, called Inky Phish Fence. They asked me to evaluate it and write about it. I think it is worth your time. It displays warning messages as you scroll through your emails, as shown here.
There are both free and paid versions of Phish Fence. The free versions work with Outlook.com, Hotmail and Gmail accounts and have add-ins available both from the Google Chrome Store and the Microsoft Appsource Store. These versions require the user to launch the add-in proactively to analyze each message, by clicking on the Inky icon above the active message area. Once they do, Phish Fence instantly analyzes the email and displays the results in a pane within the message. The majority of the analysis happens directly in Outlook or Gmail so Inky’s servers don’t need to see the raw email, which preserves the user’s privacy.
The paid versions analyze every incoming mail automatically via a server process. Inky Phish Fence can be configured to quarantine malicious mail and put warnings directly in the bodies of suspicious mail. This means users don’t have to take any action to get the warnings. In this configuration, Outlook users can get some additional info by using the add-in, but all the essential information is just indicated inline with each email message.
I produced a short video screencast that shows the differences in the two versions and how Phish Fence works. And you can download a white paper that I wrote for Inky about the history and dangers of phishing and where their solution fits in. Check out Phish Fence and see if helps you become more vigilant about your emails.