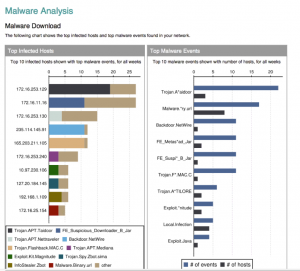
ATMs have long been targets for thieves; there was the Tyupkin malware, which could control cash drawers, reported on last fall. But a more popular form of attack is carried out via ATM skimmers, which are typically overlays attached to the outside of the ATM unit. When you insert your card into the machine, these skimmers capture your account number and PIN, which will be used later to clean out your account.
ATM Skimmers Threaten Travelers
PC Magazine has a long list of suggestions about how to recognize these skimmers, as well as how to take care when you are getting cash in a new location to ensure you’re accessing the legitimate ATM service. This is especially a problem now that many ATMs are being made by private vendors and are situated in non-banking areas such as bodegas and bars. That could be an issue, especially with the rise of more sophisticated ATM skimmers. It is hard enough to obtain foreign currency from a legit machine, given language and other issues. Now you have to worry if you are just giving your identity to the bad guys
As ATMs become more popular, the crooks are paying more attention and getting more sophisticated in compromising operations. With that in mind, it’s worth reading a series by security analyst Brian Krebs that he posted in September. Earlier this year, he was invited to come down to Mexico and see the problem firsthand. He managed to find at least 19 different ATMs that all appeared to be hacked and retrofitted with tiny, sophisticated devices that store and transmit stolen data and PINs via Bluetooth technology. These ATM skimmers could have been installed by compromised employees bribed to open up the machines and insert the necessary circuit boards to trap customer data.
 As Krebs wrote in one blog post, “Stolen card data can be retrieved from the Bluetooth components wirelessly: The thief merely needs to be within a few meters of the compromised ATM to pull stolen card data and PINs off the devices, providing he has the secret key needed to access that Bluetooth wireless connection.”
As Krebs wrote in one blog post, “Stolen card data can be retrieved from the Bluetooth components wirelessly: The thief merely needs to be within a few meters of the compromised ATM to pull stolen card data and PINs off the devices, providing he has the secret key needed to access that Bluetooth wireless connection.”
Unlike the more traditional ATM skimmers, there is no way to immediately know if a machine has been tampered with other than by analyzing the Bluetooth signals coming from the machine. In fact, Krebs found one such machine coincidentally at his own hotel! Despite meetings with the hotel security staff, he wasn’t able to get the ATM disabled.
Are Fake ATMs a Concern?
After more gumshoeing, Krebs was able to zero in on a company that is apparently producing these devices and masquerading as a legit ATM manufacturer. A fake ATM? Hold on, can that really be possible? Krebs described how it could work by generating canceled transactions. “For example, if the transaction is canceled before it reaches the processing switch of the customer’s bank, there would be absolutely no record of the customer using the ATM, despite the card data and PIN being compromised,” he wrote. This would make it harder for the banks to track down the compromised ATM, particularly if these canceled transactions were spread around the country.
Krebs mentioned that the problem isn’t unique to Mexico: Back in the U.S., a Connecticut fraudster was arrested in 1993 for placing fake ATMs across the state. The tipoff? These fakes never contained any actual cash to dispense.
Given these exploits, there are a few suggestions you should remember the next time you need get to cash. First, follow the PC Magazine suggestions on being aware of the kind of ATM you are about to use. Second, when abroad, use a bank-owned machine whenever possible and not a private, third-party ATM; the ATM skimmers that Krebs found were all from private parties.
If you do travel abroad frequently, make use of a special debit card that has a limited balance in case it does get compromised. Finally, examine your bank statements and reconcile all of your account activity as soon as possible after you return to ensure your account hasn’t been compromised.
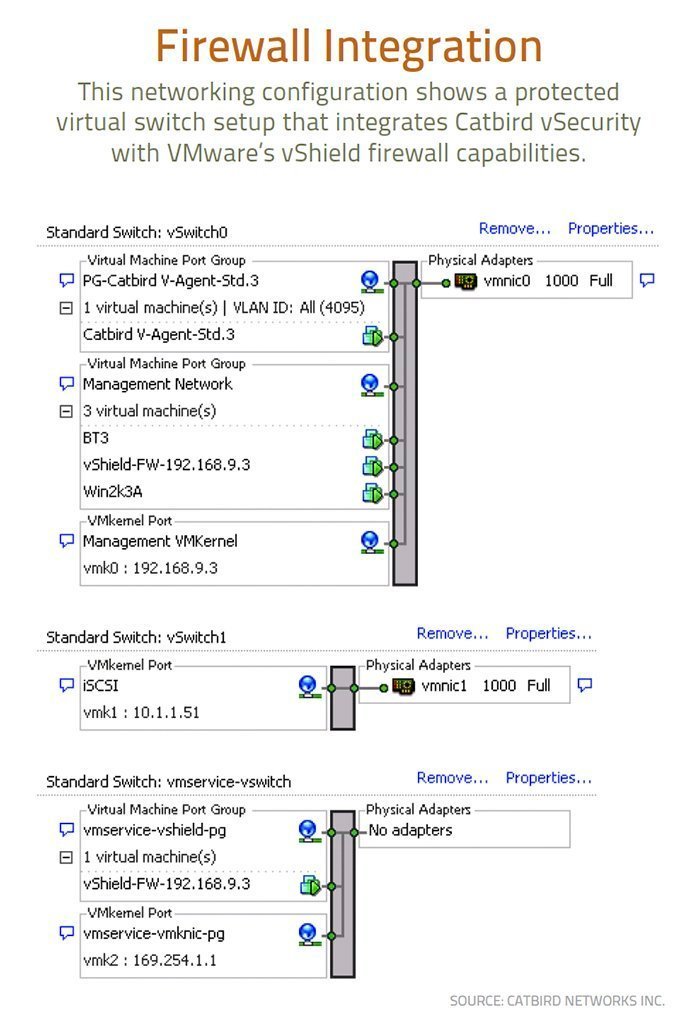 The days when IT managers used different security products to protect their on-premises and cloud infrastructures are happily coming to a close. There’s a growing awareness that migrating virtual workloads to new IT infrastructure requires different levels of protection with security mechanisms built-in.
The days when IT managers used different security products to protect their on-premises and cloud infrastructures are happily coming to a close. There’s a growing awareness that migrating virtual workloads to new IT infrastructure requires different levels of protection with security mechanisms built-in. As Krebs wrote in
As Krebs wrote in  The Security Operations Center (SOC) may be going the way of the dodo bird as security professionals outsource their protection to managed and cloud services. While many large organizations still have SOCs, smaller enterprises are finding that new technologies and better security architectures lessen the need to assemble large teams. This combination can make an IT team more proactive in protecting their infrastructure even without having a formal operations center.
The Security Operations Center (SOC) may be going the way of the dodo bird as security professionals outsource their protection to managed and cloud services. While many large organizations still have SOCs, smaller enterprises are finding that new technologies and better security architectures lessen the need to assemble large teams. This combination can make an IT team more proactive in protecting their infrastructure even without having a formal operations center.