In a new blog for Avast, I report on a new study from the IRS which shows that smishing attacks — phishing using SMS text alerts– is on the rise. My wife and I have seen numerous messages that typically are phony package delivery acknowledgements on packages that we never ordered, or offers to send us money out of the blue.
The IRS said the attacks have increased exponentially, especially texts that appear to be coming from the taxing agency. It’s important to note that no matter who you are or your particular tax situation, the IRS never communicates with anyone in this fashion, or by email either. “It is phishing on an industrial scale,” said IRS commissioner Chuck Rettig.
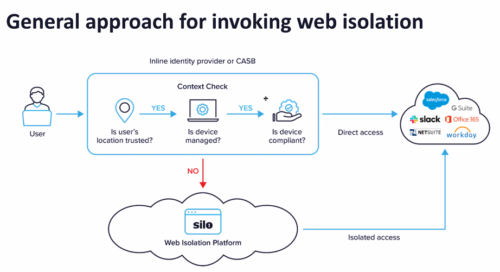 The web browser has long been the security sinkhole of enterprise infrastructure. While email is often cited as the most common entry point, malware often enters via the browser and is more difficult to prevent. Phishing, drive-by attacks, ransomware, SQL injections, man-in-the-middle, and other exploits all take advantage of the browser’s creaky user interface and huge attack surface, and the gullibility of most end users.
The web browser has long been the security sinkhole of enterprise infrastructure. While email is often cited as the most common entry point, malware often enters via the browser and is more difficult to prevent. Phishing, drive-by attacks, ransomware, SQL injections, man-in-the-middle, and other exploits all take advantage of the browser’s creaky user interface and huge attack surface, and the gullibility of most end users.
 Last week, an 18-year old hacker used social engineering techniques to compromise Uber’s network. He compromised an employee’s Slack login and then used it to send a message to Uber employees announcing that it had suffered a data breach.
Last week, an 18-year old hacker used social engineering techniques to compromise Uber’s network. He compromised an employee’s Slack login and then used it to send a message to Uber employees announcing that it had suffered a data breach. 
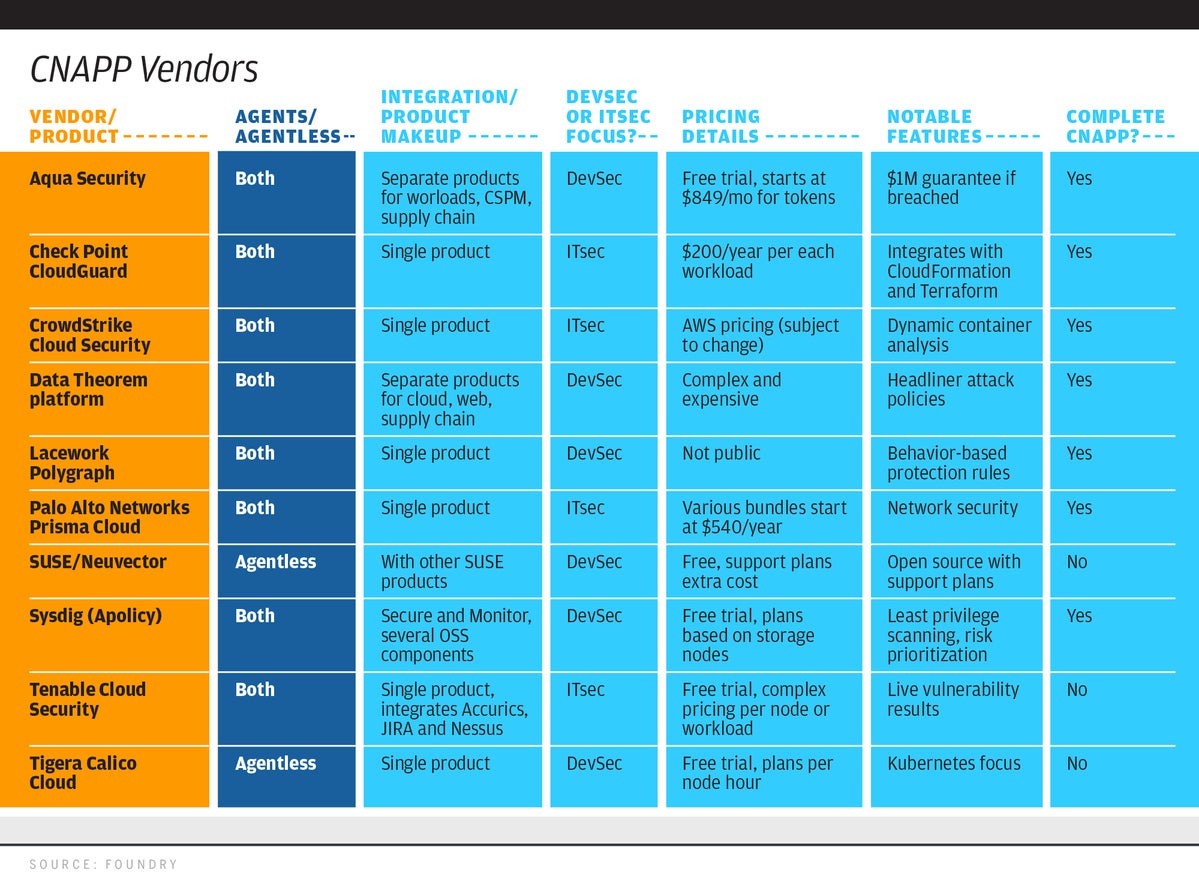 Even still, that is a lot of software to manage, integrate, and understand. However, almost none of the products that claim to be CNAPP have a full set of features that incorporate all four of these categories. In this
Even still, that is a lot of software to manage, integrate, and understand. However, almost none of the products that claim to be CNAPP have a full set of features that incorporate all four of these categories. In this