One of my first jobs was working as a professional photographer for the city of Albany documenting the city and its people. While that never morphed into a career, I have always had a love for photography. That is why I was intrigued when I heard that this month’s issue of Bon Appetit magazine comes with an interesting twist: all of its feature stories were shot with iPhone cameras by its professional food photographers.
The edict came from its editorial staff, and it was a smart move. For one thing, it shows just how far the iPhone camera has come: the latest models sport a 12 megapixel rear-facing camera, which is certainly closing in on what the best digital SLR cameras used by today’s pros normally tote around. (You can see below as one example.) And not to be outdone, but some of the Samsung Android phones have 16 megapixel cameras. One thing still lacking from the iPhone is having better control over depth of field, although there are rudimentary finger swipe gestures to help.

Cheese fries never looked as good. (from Bon Appetit)
But this isn’t just how many pixels you can put into a camera, but the fact that an iPhone camera is so ubiquitous that it can function for magazine work.
I started out in my teens with a Pentax SLR that used 35mm film and eventually graduated to first a 120-sized twin lens and then eventually to a 4×5 view camera. This latter beast required cut sheet film and a strong back to carry all the gear around, not to mention corresponding darkroom equipment that could handle the larger-sized film. I still have many of the negatives that I shot with this camera, but I haven’t had a darkroom for decades so I had to take some of them to the lab to get digital scans made.
The editors interview the photographers for the iPhone issue, who have some interesting things to say and recomm endations for budding food photographers. First, shoot from above or the side but never at an angle. That makes for more dramatic photos and better compositions. Indeed, composition is key. I realize that many of my own food photos suffer from this issue, such as the one here taken at the Ikea cafeteria.
endations for budding food photographers. First, shoot from above or the side but never at an angle. That makes for more dramatic photos and better compositions. Indeed, composition is key. I realize that many of my own food photos suffer from this issue, such as the one here taken at the Ikea cafeteria.
Second, the camera is just a tool. As one of the magazine’s photographers said,
In the past, the bigger and scarier-looking the camera you pulled out, the more intense and professional you looked. Now, you have to let go of the ego you attach to the tool, and the iPhone is the ultimate expression of that.
Understanding light and exposure helps to make for better pictures. Seems like a truism, but this becomes more important given the limited controls you have from the iPhone.
When in doubt, use a tripod. The pros came with adapters that could fit their phones accordingly, which is always a good idea to get just the shot you want.
Finally, that much-maligned selfie-stick can come in handy, especially for those overhead shots of what is served on the dinner table. One photographer didn’t come with one at their shoot, and had to go buy one to get the right shot. (For the rest of us, please put them away on the street!)
 I cover a recent white paper from the Cloud Security Alliance about network function virtualization (NFV) in a series of posts for IBM’s SecurityIntelligence.com blog. In the first post, “Security and the Virtual Network: Part I,” I discuss how NFV and software-defined networks (SDNs) are changing the traditional enterprise infrastructure. Part two explored some security challenges and implementation risks involved with deploying new virtual networks and their related technologies. And in the third post, I recommend improvements and certain security frameworks for protecting your virtual networks.
I cover a recent white paper from the Cloud Security Alliance about network function virtualization (NFV) in a series of posts for IBM’s SecurityIntelligence.com blog. In the first post, “Security and the Virtual Network: Part I,” I discuss how NFV and software-defined networks (SDNs) are changing the traditional enterprise infrastructure. Part two explored some security challenges and implementation risks involved with deploying new virtual networks and their related technologies. And in the third post, I recommend improvements and certain security frameworks for protecting your virtual networks.

 It isn’t often that a speech from a head of state at a tech conference is relevant to IT security managers, but Prime Minister Benjamin Netanyahu’s address at last week’s third annual
It isn’t often that a speech from a head of state at a tech conference is relevant to IT security managers, but Prime Minister Benjamin Netanyahu’s address at last week’s third annual 

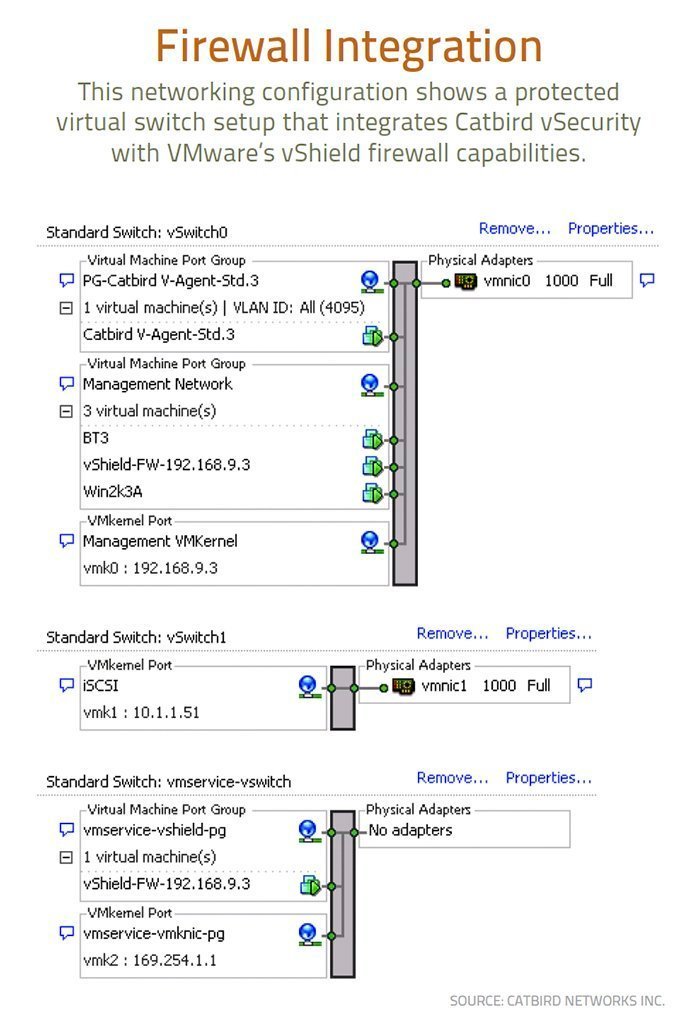 The days when IT managers used different security products to protect their on-premises and cloud infrastructures are happily coming to a close. There’s a growing awareness that migrating virtual workloads to new IT infrastructure requires different levels of protection with security mechanisms built-in.
The days when IT managers used different security products to protect their on-premises and cloud infrastructures are happily coming to a close. There’s a growing awareness that migrating virtual workloads to new IT infrastructure requires different levels of protection with security mechanisms built-in.