Google Docs is a favorite way to build applications for lightweight data manipulation, reporting, and analytics as well as useful for building websites that can capture and display data. While it is a great tool to get started using an online all-purpose office suite, you should also know its limitations and when it is time to move on to something more industrial strength. Let’s look at what is missing and when you should move on.
Document size limits. Google Docs has several limits on file sizes, depending on the type of file that you store there. For example, uploaded document files that are converted to the Google documents format can’t be larger than 50 MB, spreadsheets can be up to 2 million cells.
You need to enable Javascript and allow cookies for Google Docs to work. That might be an issue in some environments.
Lack of workflows. Google Docs is setup for real-time collaboration, which means that everyone working on a document can chime in at the same time, if they are online and have access to a particular document. As the others make changes to your document, you see them displayed almost immediately. While that is great, there is no control over the workflow: meaning you have to play traffic cop and make sure your teammates know the order of who is going to be working on the document next and how it gets passed around. There are other collaboration tools (such as the Skyword editorial add-on to WordPress) that handle this workflow better.
Weak data reporting and report construction. If you are used to these features in QuickBase, you will be frustrated by what Google Docs offers.
It isn’t at feature parity to Microsoft Office, especially for Excel, Access and PowerPoint apps. You can import .PPT and other presentation files, but you might lose some fidelity, transitions, and other aspects of your presentations. The same is true when Google Sheets is compared to Excel or other dedicated spreadsheets: while you can build a pivot table in the former, you probably wouldn’t want to use Sheets to produce complex financial models.
Fewer granular access controls to documents. Google Docs has three roles to choose from: a user can edit, can view, or can just post comments to a shared file. You can send a link and allow anyone access via email, and if you are the original owner of the document you can prevent other editors from change access permissions or adding new collaborators to the overall workflow. As owner you can also disable the options to download the file to your local desktop or print the document. That is about it: other online workspaces have more sophisticated access controls that allow more flexibility.
These user roles are established through email addresses of your workgroup. If you have users that have multiple Google IDs (such as their own Gmail account and a corporate email account that is hosted by Google) it can get confusing managing all the various access roles.
Another limitation is that with Google Docs, all documents can be either public or private (and shared among a specific list of email addresses). Other online systems are more flexible.
If you want to work offline, you have to plan ahead and make your documents available on your local desktop.
 Nearly 30 years ago, Lotus Software came out with a radical new tool called Notes that has since become a corporate staple. More than an email program, it was used by IT and non-IT alike to build collaborative apps. Think of it as the origin of the citizen developer movement.
Nearly 30 years ago, Lotus Software came out with a radical new tool called Notes that has since become a corporate staple. More than an email program, it was used by IT and non-IT alike to build collaborative apps. Think of it as the origin of the citizen developer movement. As more of our users start literally wearing their own gear to work, the number of threats from these devices, such as Fitbits and Apple Watches, increases. After all, they are just another remote wireless computer that can be compromised to gain access to your enterprise network. I talk about the potential threats and ways to mitigate them, along with other factors. You can
As more of our users start literally wearing their own gear to work, the number of threats from these devices, such as Fitbits and Apple Watches, increases. After all, they are just another remote wireless computer that can be compromised to gain access to your enterprise network. I talk about the potential threats and ways to mitigate them, along with other factors. You can  Many of us started out with database software with something like Microsoft Access. It came included as part of the Office suite, was fairly easy to get started and infinitely customizable for light database programming. But with all these advantages, it might be time to look elsewhere for alternatives, especially for citizen developers who want to build more sophisticated online database applications.
Many of us started out with database software with something like Microsoft Access. It came included as part of the Office suite, was fairly easy to get started and infinitely customizable for light database programming. But with all these advantages, it might be time to look elsewhere for alternatives, especially for citizen developers who want to build more sophisticated online database applications.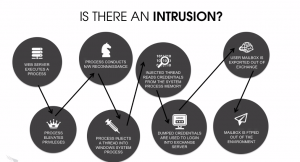
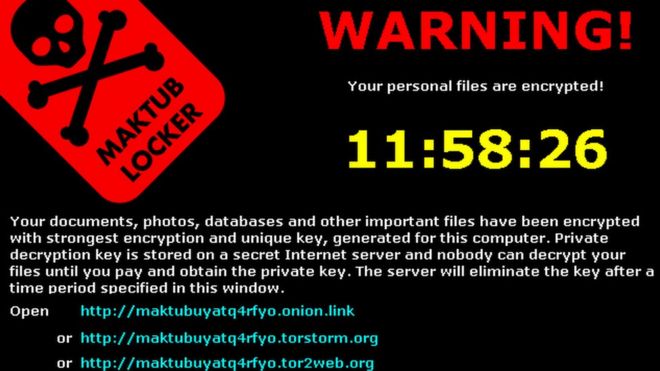
 Detecting virus signatures is so last year. Creating a virus with a unique signature or hash is quite literally child’s play, and most anti-virus products catch just a few percent of the malware that is active these days. You need better tools, called endpoint detection and response (EDR), such as those that integrate with SIEMs, that can recognize errant behavior and remediate endpoints quickly.
Detecting virus signatures is so last year. Creating a virus with a unique signature or hash is quite literally child’s play, and most anti-virus products catch just a few percent of the malware that is active these days. You need better tools, called endpoint detection and response (EDR), such as those that integrate with SIEMs, that can recognize errant behavior and remediate endpoints quickly.