 Now that more of us are working from home (WFH), one of the key technologies that can cause problems is surprisingly our networked printers. Hackers target these devices frequently, which is why many IT departments have taken steps to prevent home laptops from connecting to them. In my latest blog post for Network Solutions, I suggest several strategies to help you understand the potential threats and be able to print from home securely, including what IT managers can do to manage them better and what users can do to avoid common security issues.
Now that more of us are working from home (WFH), one of the key technologies that can cause problems is surprisingly our networked printers. Hackers target these devices frequently, which is why many IT departments have taken steps to prevent home laptops from connecting to them. In my latest blog post for Network Solutions, I suggest several strategies to help you understand the potential threats and be able to print from home securely, including what IT managers can do to manage them better and what users can do to avoid common security issues.
Category Archives: Published work
Network Solutions blog: How to Secure Mobile Devices from Common Vulnerabilities
 The biggest cyber threat isn’t sitting on your desk: it is in your pocket or purse and, of course, we mean your smartphone. Our phones have become the prime hacking target, due to a combination of circumstances, some under our control and some not. These mobile malware efforts aren’t new. Sophos has been tracking them for more than a decade (see this timeline from 2016). There are numerous examples of attacks, including fake anti-virus, botnets, and hidden or misleading mobile apps. If you want the quick version, there is this blog post for Network Solutions. It includes several practical suggestions on how you can improve your mobile device security.
The biggest cyber threat isn’t sitting on your desk: it is in your pocket or purse and, of course, we mean your smartphone. Our phones have become the prime hacking target, due to a combination of circumstances, some under our control and some not. These mobile malware efforts aren’t new. Sophos has been tracking them for more than a decade (see this timeline from 2016). There are numerous examples of attacks, including fake anti-virus, botnets, and hidden or misleading mobile apps. If you want the quick version, there is this blog post for Network Solutions. It includes several practical suggestions on how you can improve your mobile device security.
You can also download my ebook that goes into more specific details about these various approaches to mobile device security.
Avast blog: Your guide to safe and secure online dating
Recently, information from five different dating sites have leaked millions of their users’ private data. The sites cover users from the USA, Korea and Japan. On top of this, a variety of other niche dating apps (such as CougarD and 3Somes) had data breaches of their own that exposed hundreds of thousands of users’ profiles in May, including photos and audio recordings. This latter event occurred thanks to a misconfigured and open Amazon S3 storage bucket. Thankfully, the owner of the account quickly moved to secure it properly when they heard from security researchers. We haven’t heard much about dating site breaches since private data from some 30M Ashley Madison users were posted online in 2015.
 In this time of the pandemic when more of us are doing everything we can online, dating remains a security sinkhole. This is because by its very nature, online dating means we eventually have to reveal a lot of personal information to our potential dating partners. How we do this is critical for maintaining both information security and personal safety. In this post for Avast’s blog I provide a bunch of pointers on how to do this properly and provide my own recommendations.
In this time of the pandemic when more of us are doing everything we can online, dating remains a security sinkhole. This is because by its very nature, online dating means we eventually have to reveal a lot of personal information to our potential dating partners. How we do this is critical for maintaining both information security and personal safety. In this post for Avast’s blog I provide a bunch of pointers on how to do this properly and provide my own recommendations.
Avast blog: Understanding BlueLeaks
Earlier this month, a group of hackers published a massive dataset stolen from various local law enforcement agencies. The data has been labeled BlueLeaks and contains more than 269 GB of thousands of police reports that go back at least two decades from hundreds of agencies from around the US. The reports list private data including names, email addresses, phone numbers and bank accounts. The source is a group called Distributed Denial of Secrets or DDoSecrets, which like Wikileaks has been publishing various leaked datasets for many years.
The data can be easily searched as shown in the screenshot below.
What BlueLeaks shows is that third-party IT providers need to be properly vetted for their internal security methods. While having an easy-to-update website is great, it needs to be secure and all accounts should use multi-factor authentication and other tools to ensure that only authorized users have access. You can read more about the leak and its relevance here in my post for Avast’s blog.
RSA blog: Making the Next Digital Transition Will Require Extensive Security Planning
We are all in a forced march towards a more accelerated digital transition because of the virus. McKinsey is one of many consulting firms who have proposed a 90-day guide towards moving into this brave new era. And while I don’t want to pick on them specifically, their plan –like others of its ilk — is somewhat flawed. It will take more than Zoom and Slack meetings and a corporate subscription to G Docs or O365 to remake our organizations.
“Every remote worker is now a separate risk to the company,” Canadian cybersecurity consultant Andrew Brewer shared with CIM Magazine.. “Each home environment is different, and with so many of them and [the health crisis] happening so suddenly it’s like a perfect storm for companies.”
To make this move successful, we all will have a lot more work to do in planning for this transition. Here are a few ways to begin to frame your thinking:
First have a security-by-design approach to become more digital and to support remote working long-term. We have to stop giving lip service to InfoSec. Instead, we should be thinking about security first and foremost. This isn’t something to wait until the end of a project when the security team will be tasked with another “cleanup on Aisle 6” operation and asked to add security in after the environment is built. This means involving the entire C-suite at the beginning of the process to lay a solid foundation for a new network infrastructure, a new communications plan and the right kinds of gear for your remote workers.
Second have a better understanding of the sea changes that will need to happen in DevSecOps to support 100% WFH. In a different report, McKinsey says that rapid IT changes “may have created new risks and exposures.” Planning for these risks and modernizing the tech stack may take more than a 90-day project timeline.
Finally, there is the parallel effort to understand the omnichannel approach that will be introduced with a digital-centric business model. The move towards 100% WFH will introduce even more digital channels, which means more opportunity for fraud. Over the years, I have spoken to Daniel Cohen, the Head of Anti-Fraud Products and Strategy for RSA. In his opinion, the way to combat this is to start investing in omnichannel fraud prevention. A more digital operation also means that your cybersecurity attack surface area will increase, so it will take “information security, risk management and fraud prevention teams to work together, says Cohen.
As an example, I offer my purchase of some pants from the Gap. I got them online, but they were too small, so I returned them. I still haven’t received a credit for my return, because the returns are sitting in a big pile in some warehouse, waiting for an employee to sort through them to ensure that I did indeed return the appropriate merch. And this is from a company that has a robust online business. As long as the multiple channels intersect with some human-provided function, you will still have non-digital intersections and collaborations that will need careful planning and attention.
There are many risks and challenges associated with digital transformation in response to the current health crisis. I think they can be conquered, but all will require significant planning to ensure that we manage the associated risk appropriately.
Network Solutions blog: How to sell your spare IP address block
For the past 27 years, I have owned a class C or /16 block of IPv4 addresses. I don’t recall what prompted me back then to apply for my block: I didn’t really have any way to run a network online, and the Internet was just catching on at the time. The transaction took moments with the exchange of a couple of emails, and there was no cost to obtain the block.
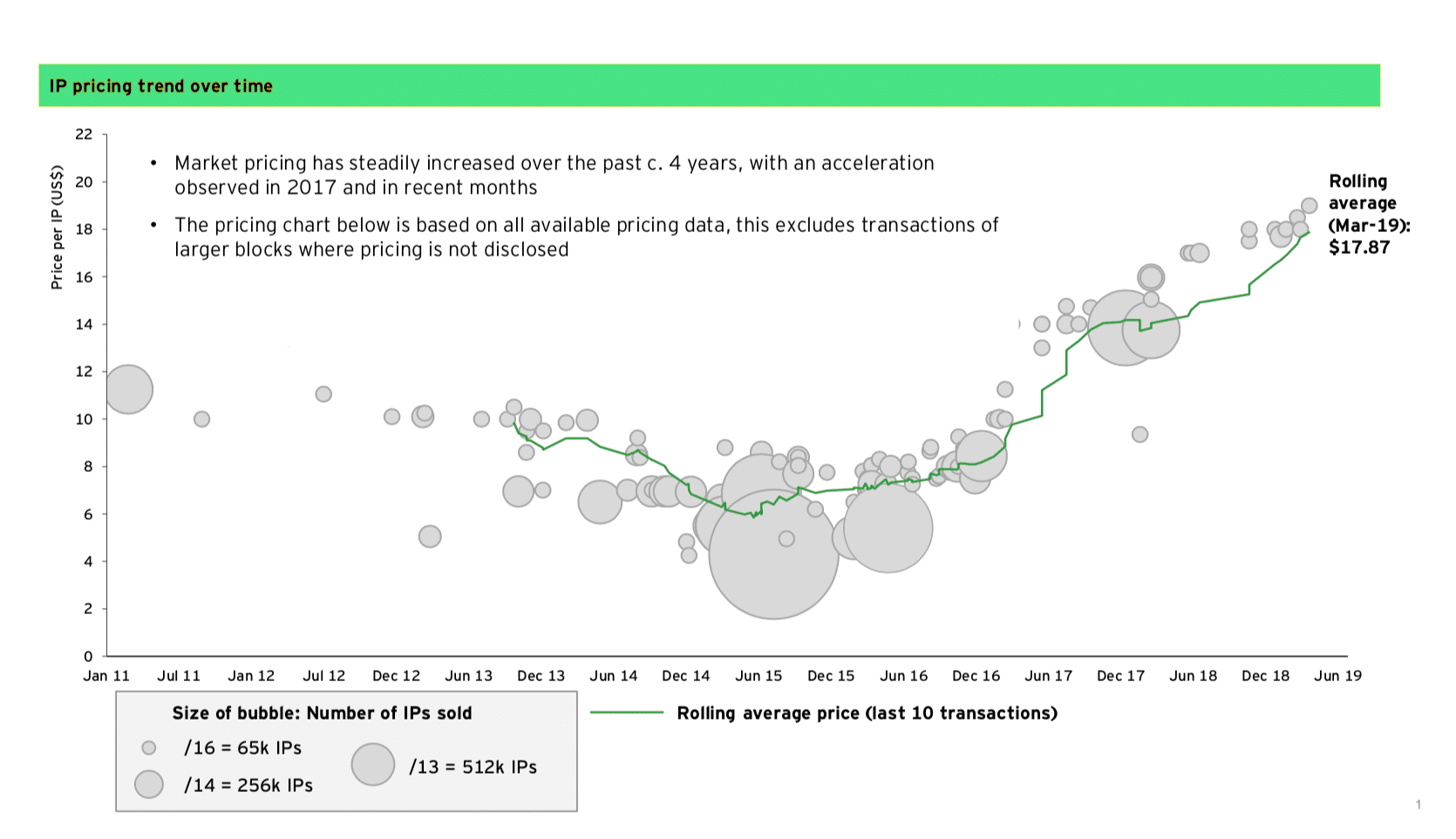 Earlier this year I was reminded that I still owned this block and that I could sell it and make some quick cash. What was interesting is that in all the years I had the block I had never really used it for anything. I had never set up any computers using any of the 256 IP addresses associated with it. In used car terms, it was in mint condition. Virgin cyberspace territory. So began my journey into the used marketplace that began just before the start of the new year. I document some of this journey in a blog post for Network Solutions. I tell the story about what I learned and what I would do differently knowing what I know now. You can see that block transfers have become a thing from this graph.
Earlier this year I was reminded that I still owned this block and that I could sell it and make some quick cash. What was interesting is that in all the years I had the block I had never really used it for anything. I had never set up any computers using any of the 256 IP addresses associated with it. In used car terms, it was in mint condition. Virgin cyberspace territory. So began my journey into the used marketplace that began just before the start of the new year. I document some of this journey in a blog post for Network Solutions. I tell the story about what I learned and what I would do differently knowing what I know now. You can see that block transfers have become a thing from this graph.
I also wrote an eBook for them based on this experience if you want to learn more about the address block aftermarket. And in this more personal post,Beware that it isn’t easy or quick money by any means. It will take a lot of work and a lot of your time.
RSA blog: Do you know where your firewalls are located?
When I was growing up, the evening news (on one of the five total broadcast channels we could watch) would start with the tag line, “It’s ten o’clock, do you know where you children are?” I know, seems so quaint now, especially since many of us haven’t left home in weeks. But the modern equivalent might be, “It’s whatever o’clock. Do you know where your firewalls are?” This is not a rhetorical question and answering it will give you some insight into how your network infrastructure is governed (or not, as the case might be), and what actionable items you’ll need to fix that pronto.
I wrote in last month’s blog as more of us work from home (WFH) we have to go back to basics. One of those basics is in understanding our network topology and where those firewalls are located. A recent informal Twitter survey by researcher Kate Brew showed that less than half of infosec managers don’t even know the basics of their network configurations. They couldn’t even figure out the raw number of firewalls in their network. That is a depressing thought. Now, granted this isn’t a Gallup-level definitive answer, but still probably undercounts the observed on-the-ground truth.
Why is this a big deal? Mainly because our networks are evolving rapidly. Take the situation of new data flows as we have higher proportions of remote users. Or the situation where smartphones are being brought into healthcare facilities and used in different ways by health workers to communicate with patient families. Given that many infosec managers are juggling numerous crises to keep their business networks running, this very basic fact needs quick attention.
It is important now because the bad guys are already sharpened their phishing lures: numerous vendors (and the FBI) report that Covid-related phishing attacks are on the rise. You have to up your game, before someone finds a wormhole and makes off with your most precious data.
But let’s just take this a step further. It isn’t just the number or location of our firewalls, but also what happens to them. Let’s posit that you have put in place a series of “emergency” exceptions to your well-crafted rule set. (Ahem, do you really want to go there?) You did this as a response to fix your network traffic flows to handle the rise in WFH’ers. Great. But let’s move into the future a few years when these exceptions have remained in place, long forgotten and leaving not just a wormhole but the broad side of a barn for your drive-by attack.
This points out that now is the time to get our risk and data governance act together. If we are going to be a 95% WFH operation, then make sure we plan our networks and our security accordingly. In other words, we need to figure out a network topology that will be more secure and have the right tools and hardware, as I mentioned in last month’s blog.
If you view this in another light, the uncertainty over your firewalls is really a proxy for the conflict between the network and security teams at your company. This is an old issue (see this Sandra Gittlen piece in Network World from several years ago) and I am not suggesting that you should combine them into a single unit. Gittlen cites sources who point out that the two teams can collaborate better when they are separated, because they have different roles and jobs to do. Security should track down issues, vulnerabilities and risks; the network folks should fix things and prevent future problems. And both need to work on security from the beginning of any new project, what is commonly called “security by design.” Still, another source says, “There is value in security teams learning networking’s language.”
Take the time to know where your firewalls are located and use this as a teachable moment to better understand how you have set up their rulesets and other basic configuration details.
Network Solutions blogger
In April 2020, I began writing blog posts and ebooks for them.
- Why you need a premium DNS provider
- How to prevent a VPN data leak
- What is URL blacklisting?
- What is honeypot network security?
- How sandbox security helps prevent malware attacks
- Protecting your brand from domain squatters
- How to reduce privilege escalation attacks
- Why are so many online containers unsecured?
- How to find the most useful IT Certifications to Enhance Your Career
- 10 Strategies to Harden Your WP Installation
- The Future of Cloud Access Security Brokers
- Characteristics of Reliable Registrars
- Modifying Your Company’s Network Security to Handle more WFH Employees
- How to avoid network-level blacklists
- What SSL is Right for my Business
- What Technologies Can Protect Your Applications Stack
- Three Tactics to Avoid Being Blacklisted
- My personal experience selling my IP block
- Best practices for securing an enterprise IM
- Solutions to purchase and setup CASB With Ease
- How to Secure Mobile Devices from Common Vulnerabilities
- Tools and tips for best practices with network printers when you work from home
- Better and more cost-effective network bandwidth
- Mastering Email Security with DKIM
- How to evaluate a DNS security provider
- Understanding SSO and how it can help protect your environment
- Using passwordless options
- Protect your organization from ransomware attacks
- Counter Darkweb Threats with Proactive Security Management.
- Microsoft Teams improvements
- Blocking homographic attacks
- How to Find and Stop Smishing Attacks
- Ways to Identify and Prevent Vishing Attacks
- Identity access management tools for your business
In addition, I also wrote these ebooks:
Avast blog: The citizen’s guide to spotting fake news
 Truth and facts are hard to come by these days. Most of us want to understand what is true and what is not. What’s more, we want our kids to understand the difference between fact and fiction. But sifting through our social media — and even ordinary news reports — does require some work. I have put together some resources in this blog post to help you discriminate the truthiness (as Stephen Colbert might have said) of what you find online.
Truth and facts are hard to come by these days. Most of us want to understand what is true and what is not. What’s more, we want our kids to understand the difference between fact and fiction. But sifting through our social media — and even ordinary news reports — does require some work. I have put together some resources in this blog post to help you discriminate the truthiness (as Stephen Colbert might have said) of what you find online.
The sheer amount of disinformation, lies, conspiracy theories — call them what you will — is staggering. In this post for Avast’s blog, I review how we got here, how you can start to figure out whether something is true or false online, and what should be your own strategies for becoming more skeptical of what you read online.
RSA blog: Renaissance of the OTP hardware token
Few things in infosec can date back to the early 1990s and still be in demand today, but such is the case with RSA’s long history of its SecurID one-time password (OTP) hardware key-fob tokens. Despite numerous security analysts predicting their death, hardware OTPs have been a great business for RSA and lately are undergoing a renaissance with a newfound interest among security managers. In this month’s blog, I take a look at this evolution, why the hardware token is coming back, and what are some of the current trends in multi-factor authentication (MFA) too.
Today’s hardware token has gotten more sophisticated than that original fob that just displayed a series of those OTP random digits. This was partly a necessity, since their use always has been somewhat cumbersome for both end users and security managers alike. (I mentioned this drawback in one of my reviews of MFA tools in Network World in 2013, when I said that “toting around tokens means that they can get taken, and in a large enterprise, hardware tokens are a pain to manage, provision and track.” Still, this review in 2012 mentioned this attraction for using hardware tokens: “They don’t require app developers to rewrite their apps from scratch, and the hardware token provides us with the level of security assurance we want and need. We’ve been carrying tokens around for 25 years; I wonder if they’ll make 50?” I think we can safely say that tokens will have this longevity.
In 2016, several vendors released smarter hardware tokens that came with encryption keys or encryption engines embedded. This made them easier to use, because of push authentication methods that eliminated a few steps. More recently, there have been other vendors who have released hardware tokens that support the Fast Identity Online (FIDO) protocols, so a single token can work with a variety of authentication servers. In the past, each fob was married to a particular server, which meant users had to cart around a collection of tokens if they needed to login to multiple servers and cloud-based services.
As the tokens were getting more capable, the demand for better MFA security was also increasing. Remote workers were on the rise, and earlier this year travel restrictions and flight cancellations because of the coronavirus made remote work more necessary and acceptable. That in turn drove increased demand for better authentication methods such as both hardware and smartphone-based tokens. A good case study is the US Army, which is expanding its MFA coverage to National Guard members and first responders to use hardware and smartphone tokens.
At the same time, this increased demand didn’t escape the criminal world, who began to focus on ways to exploit MFA weak points, especially SMS-based MFA methods. The FBI issued warnings last fall that documented various techniques to bypass MFA methods, including swapping out cellphone SIM cards, using specialty-designed malware to automate MFA phishing schemes and employing social engineering methods to fool users into providing the OTP digits in real time. At the RSA Conference last month, researchers documented new methods to get around the MFA smartphone apps by using outdated phone operating systems, attacks called Android screen overlays that fool users into entering the OTP codes or other compromises to the kernel mobile phone OS itself.
Where do we go from here with deploying MFA? Here are a few thoughts. First, you need to take a step back and craft a solid access and authentication management strategy for your entire enterprise out of whole cloth. You should examine whether every user needs a hardware token and for all their access methods. Instead, focus on the relative risks. For example, tokens are a good idea for those users who handle money transactions, but perhaps not if their jobs are on the factory floor. Next, think about how you handle your partners and customers’ transactions, and how to beef up their logins. Getting hardware tokens registered and eventually revoked to anyone who isn’t a full-time employee is still painful. And also consider whether you should mix and match hardware and smartphone MFA apps, especially when the application circumstances and risk profiles dictate.
Finally, consider how to authenticate cloud apps. Some clouds support standards that make integrating smartphone MFA apps easier, so that might be a better solution. At the end of the day, having more MFA is usually better than no MFA, but it should be deployed intelligently and carefully.
