For those of you who are avid readers, you might want to investigate a service called NetGalley. I have been using them for seven years and have read hundreds of books for free. The only catch? I have to read them on my Kindle (or Nook or equivalent device) and then write a short review that I then post to Amazon, B&N, Goodreads, and other bookselling websites.
It is a terrific service which publishes the pre-publication versions of books, which used to be called galleys back in the days of Gutenberg, to a select audience of what they call “professional readers.” These versions often have small editing mistakes but are otherwise close to the actual text that you will see in the finished book.
The workflow is as follows. Once you join the service, you will get weekly notifications in your email about upcoming new books. Sometimes there is a short description, and you can click on that and get a longer one that will give you an idea if you are interested in reading the book. The service is used by both new authors and established ones alike, and there are tens of thousands of readers and authors using the service. Some books are immediately available for download; some will require the publisher to approve your request. Sometimes I get turned down, but usually within a day or so I have a new book waiting for me in my NetGalley account. I then send the digital file to my Kindle reader, and within minutes I can be reading a new book. Pretty neat, this whole internet thing, right?
I would say over the past several years I go through phases where I read more books on my Kindle than in print, and then the reverse. Given that bookstores have been mostly closed for browsing under the pandemic, I have gone back to using my Kindle more.
The NetGalley service keeps track of when the book is actually available for sale on the book ecommerce sites and sends you a tickler so you can post your review accordingly. That appeals to me, because I like to be in the first batch of folks posting my review.

There is a wide range of books available on the service, and this also includes audiobooks as well as the traditional printed text. You can set your subject matter preferences and other parameters for your account. If you don’t want to wait for the weekly notifications, you can browse for new titles at any time.
If you really like a book and want to get to interview the author, NetGalley will help facilitate that relationship. They also make it very easy to take your review and get it put on the bookselling sites with a couple of clicks.
As I said, the service is free for readers. They make their money from publishers (and self-published authors) who pay a fee to post their galleys on the service for a specific time period. The fees vary from a single book for $450 for six months to discounts for multiple books for publishing houses or members of various publishing associations.
I will be giving a seminar on NetGalley in September for the St. Louis Publishers Association. Email me if you are interested in seeing this presentation.




 If you’ve been following Amazon’s move towards having physical storefronts, you probably have seen the news about a series of different types of retail stores they have created, including bookstores, grocery stores, general merchandise stores, and shops selling prepared food. Add to this along with the fact that they’ve owned Whole Foods Markets for the past four years. In
If you’ve been following Amazon’s move towards having physical storefronts, you probably have seen the news about a series of different types of retail stores they have created, including bookstores, grocery stores, general merchandise stores, and shops selling prepared food. Add to this along with the fact that they’ve owned Whole Foods Markets for the past four years. In 
 The copycat serial killer on the loose is a common plot point, but this horror/thriller takes things a step further. Some of the steps I can’t reveal without spoilers but let’s just say this novel has some very strange stuff going on and it plumbs the depths of psychosis of several of its characters. The POV is from the daughter who has found out her mother killed herself, and she tries to figure out what happened. The two were never very close, and the death brings out many life moments that were swept under the rug and placed into dark reaches of her memories. While I am not a big horror genre reader this book worked for me as a pure thriller and mystery. The characters ring true and of course the bodies begin to pile up as the copycat killer continues to strike.
The copycat serial killer on the loose is a common plot point, but this horror/thriller takes things a step further. Some of the steps I can’t reveal without spoilers but let’s just say this novel has some very strange stuff going on and it plumbs the depths of psychosis of several of its characters. The POV is from the daughter who has found out her mother killed herself, and she tries to figure out what happened. The two were never very close, and the death brings out many life moments that were swept under the rug and placed into dark reaches of her memories. While I am not a big horror genre reader this book worked for me as a pure thriller and mystery. The characters ring true and of course the bodies begin to pile up as the copycat killer continues to strike. 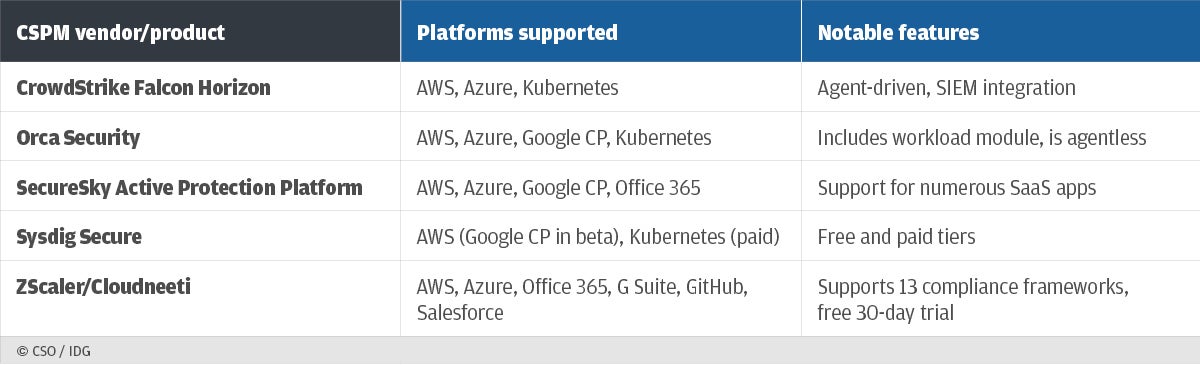 Every week brings another report of someone leaving an unsecured online storage container filled with sensitive customer data. Thanks to an increasing number of unintentional cloud configuration mistakes and an increasing importance of cloud infrastructure, we need tools that can find and fix these unintentional errors. That is where cloud security posture management (CSPM) tools come into play. These combine threat intelligence, detection, and remediation that work across complex collections of cloud-based applications. You can see a few of them above.
Every week brings another report of someone leaving an unsecured online storage container filled with sensitive customer data. Thanks to an increasing number of unintentional cloud configuration mistakes and an increasing importance of cloud infrastructure, we need tools that can find and fix these unintentional errors. That is where cloud security posture management (CSPM) tools come into play. These combine threat intelligence, detection, and remediation that work across complex collections of cloud-based applications. You can see a few of them above.