Mobile payment apps can be a convenient way to send and receive money using your smartphone or smartwatch. Paying for items this way has never been easier, thanks to the availability of numerous mobile payment apps, better payment terminal infrastructure, and wider support for Bluetooth/near-field communication (NFC) contactless credit cards by American issuers. The coronavirus pandemic has also helped to make contactless “everything” more compelling. I tested out five different mobile payment apps: Apple Pay, Google Pay, Samsung Pay, Venmo (by PayPal) and Cash App (by Block, formerly Square) recently, and wrote my review for CNN/Underscored here.
How to choose the best MFA methods to help stop ransomware
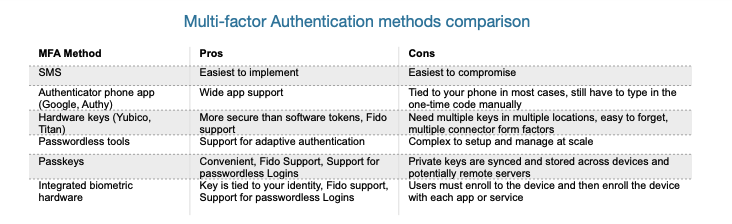
 Interest in multi-factor authentication (MFA) has risen in the past few years, spurred by the increasing frequency and severity of data breaches and destructive attacks. When Covid-19 happened, ransomware actors proliferated. Recently, MFA has received a boost from various supporters, including Google, the US federal government, GitHub and Microsoft. When evaluating the various MFA products and technologies on the market today, it’s important to understand the tradeoffs in security, scalability and usability inherent in each option. Additionally, it can be helpful to understand your available choices in the context of how MFA has developed over time.
Interest in multi-factor authentication (MFA) has risen in the past few years, spurred by the increasing frequency and severity of data breaches and destructive attacks. When Covid-19 happened, ransomware actors proliferated. Recently, MFA has received a boost from various supporters, including Google, the US federal government, GitHub and Microsoft. When evaluating the various MFA products and technologies on the market today, it’s important to understand the tradeoffs in security, scalability and usability inherent in each option. Additionally, it can be helpful to understand your available choices in the context of how MFA has developed over time.
In this ebook I co-authored with Evan Krueger, the engineering manager of Token, we track the evolution of MFA, the work of the FIDO Alliance to bring the industry together and provide new authentication standards, and some suggestions on how to choose the right MFA technology that you carry with you, that understands your biometrics, and can be married to your identity without any operator intervention. Ransomware and data theft are only increasing in severity. It’s time for the defenders to up their game as well.
Avast blog: More developments on NSO’s Pegasus spyware
Last summer, I wrote about a major international investigation of the NSO Group and its Pegasus spyware. We described how it works and what you can do to protect your phone. NSO has gone through some difficult times as a result of that analysis. NSO was almost purchased by an American company that is closely linked to intelligence operations until the US Government put them, along with another Israeli spyware vendor Candiru, on a special block list that prevents both from obtaining government contracts. Candiru, you might recall, was discovered to be doing its own zero-day spying by Avast researchers.
In my post today for Avast’s blog, I review what transpired at a recent hearing held by the House Intelligence Committee. There were three witnesses who emphasized the threat of spyware to various democracies around the world, and provided lots of specifics about how Pegasus has operated.
Tracking the web of misinformation and copycats
How fast does misinformation spread across the web? Turns out, when it comes to the Kardashians, pretty darn fast. But even for those of us who are mere mortals and write about boring stuff like tech, still plenty fast. Let me explain.
Shelly Palmer also writes about tech stuff, and one of his articles quoted Kim and Kylie from an article in CNBC The quote contained a typo, namely, “Strop trying to be tiktok I just want to see cute photos of my friends.” Note the italics. He saw the typo and called CNBC, and within minutes the typo was fixed. No matter. By that short moment in time, hundreds of sites picked it up and included the original typo. Shelly used the typo as a “misinformation DNA marker,” as he puts it, to track who was more diligent about the typo and who could care less. It’s all about the clicks, and when it comes to Kim and Kylie, well, that can supercharge a story.
Shelly found the original phrase, with correct spelling, on a Change.org petition the women signed. What is interesting about his investigation was showing exactly how there are still close to 200 sites that haven’t changed the typo when I did my own search just now.
I feel for both Shelly and the CNBC reporter Jonathan Vanian who admitted to making the typo. I have found copycat websites all over the place that have taken my stories and posted exact replicas — some including my own byline — as if they were syndicating my content legally. They are not. It helped that I included (unintentionally at first, but now more deliberately) my own misinformation DNA marker in the form of a link to a previous blog post on my own blog. WordPress does a very solid job of tracking when someone else is posting to another WordPress blog with a link back to my content. I have seen dozens of these copycat posts, some within minutes of my story going live on the corporate blogs that have paid me to write for them. Of course, I notify my editors, but there is really very little that they can do. These copycat sites are often in other countries, and getting a takedown notice is nearly impossible, expensive, time-consuming, or all three.
All this talk about copycat websites reminds me of a story from my early career at PC Week back in 1988. I wrote a column for the paper that envisioned the advice columnist Miss Manners giving out computing advice (link) for common situations of that era. I have to say, first, I got her tone and style down cold (I will tell you why in a moment). And second, the piece has held up well after all these years, even though it uses terms that many contemporary PC users might never have heard of before. About a month after the piece ran in PC Week, I got a cease and desist letter from her syndicate’s lawyers. That to me was one of the high moments of my tenure at the pub, and an indication of how well the parody had gotten things.
Now, if any of you dear readers would like to try your hand at parodying my own style, please have it. I promise not to engage any lawyers.
Avast blog: How to prepare for a hacking incident
The initial phases of a breach are often the most critical: The intruder is counting on your confusion, your lack of a plan or a clear chain of authority, and any early missteps. Given that it’s only a matter of time before a breach happens, what can you do after encountering an incident to minimize the damage?
For businesses of all sizes, incident response planning infrastructures have gotten very complex, with many interconnected relationships that might not be immediately obvious — until something goes wrong. In this blog for Avast, I outline how you can prepare for an incident in a well-thought-out and organized manner.
CNN Underscored: Best cloud personal storage apps
It used to be that 1 TB of storage was a lot, but now this amount of storage is quite common to find on even the least expensive laptops. Over the years, a number of cloud-based storage vendors have begun to support the TB era and now many of them offer monthly storage plans for a reasonable price. We tested five different cloud-based storage apps—Apple iCloud+, Box, Dropbox, Google One, and Microsoft OneDrive—to see which one is the best cloud-based storage app for you. OneDrive comes out on top and it was easier to install on Macs than on some of our Windows PCs that had additional browser-based security that blocked the desktop client downloads.
Your car has become yet another subscription service
The Verge has this piece about how carmakers have discovered subscription pricing, thanks in part to the leadership of Tesla. I have always thought of Tesla as a software company that installs their code in a big computer that happens to look a lot like a car. Now the traditional car companies have gotten more interested in selling subscriptions. For GM, these generate $2B annual revenues, which works out to customers paying around $40 a month for various o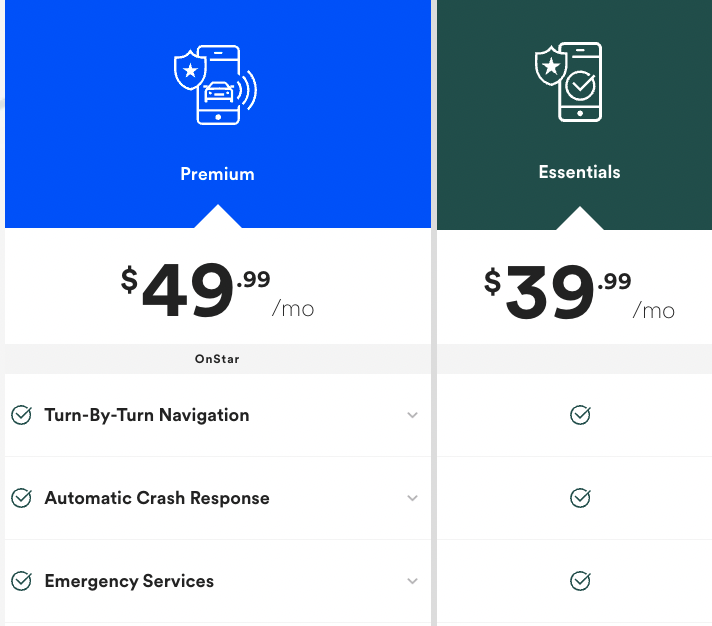 ptions such as OnStar or SiriusXM.
ptions such as OnStar or SiriusXM.
But as Hawkins points out in his piece, this has fast become a nightmare for those citizens that don’t want to debug their car’s software and just want to drive them from one place to another. BMW was selling subs overseas to turn on the option for heated seats. Granted, most of the subs are for things like entertainment or driver-assisted features.
The problem with subscription cars is that the Netflix (or choose your favorite SaaS supplier) model breaks down quickly. There are several reasons. First, the software that comes with your car is most certainly out of date, sometimes by about a year even if you buy the current year’s model when it first goes on sale the previous fall. This is because it takes time to design the car and get subs it from the factory to your dealer and then to you. But another reason is that the car companies are not doing nightly software builds or set up like software companies — until Tesla came along.
Second, the car needs connectivity to update itself, and until lately that connectivity was either expensive (for cellular broadband) or inconvenient (such as using Bluetooth to get to your phone), or both.
Third, car subscribers are often paying to remove a software block on a functionality that already exists when the car rolled off the line. That can be frustrating for consumers, although Tesla owners seem ok with it for now.
Next, unlike SaaS vendors, you can’t usually try before you buy the subscription. Some of the car companies do offer enticement — when I got my used GM car from the dealer, they bundled in SiriusXM for a limited time. But for the most part, they haven’t fully embraced the SaaS model. Plus, the collection of features for the “free pricing tier” — if such a thing existed to the extent that it does in the SaaS world — is just brutally hard to figure out. It is hard to figure out a decent price point (see BMW’s mistakes charging upwards of $80/month for some of their services). It is hard to price something (like a heated seat) that was in the “free forever ” tier. And it is hard to support. Call your dealer? Yeah, right.
That brings up another point. How do you recover from a car’s software error? No one wants to see a blue screen in their car. My aging car’s GPS gets “lost” and has me driving through empty places on its map, which is somewhat disconcerting. It is one thing to wait for a file to download from some cloud server but another thing if you are going along at 70 mph down the freeway. Can I get a software update on my GPS? Nope.
Finally, the biggest issue is that carmakers are looking at subscriptions as found money when they should be dropping prices and using them as a way to amortize the vehicle sale. As prices on vehicles is rising faster than (insert your favorite supply chain metaphor here), you would think this is obvious. But no. This just adds to the distrust many of us have when the time comes to buy our next car and have to enter the 12 circles of hell otherwise known as the showroom.
Still, there is Tesla. Like I said, not your dad’s Buick.
Avast blog: More Magecart attacks
Magecart, the notorious credit card stealing cybercrime syndicate, is once again in the news. It is the gift that keeps on giving – it has recently taken root in three different online restaurant ordering websites: MenuDrive, Harbortouch, and InTouchPOS. The malware was found in more than 300 restaurants that used them and exposed more than 50,000 paid orders. The malware was present in some of these systems for many months before they were discovered. Indeed, some attacks began last November and are still active.
How Fortnite spurred innovations in architectural technology
For someone who has been deeply steeped in technology for most of my career, I am woefully ignorant about computer games. I have written about this aspect of my life before, but today’s topic is how one game studio has had a breakout success in developing some very serious non-gaming business applications.
 The company is Epic Games, most notably known for its Fortnite brand. Perhaps you have played it, or your kids have played it. Fortnite is built using the Unreal Engine, which has been around for decades and is now on its fifth version. Epic was smart with UE in getting it established as the premier 3D visualization tool, and it is used in all sorts of business applications. One of them caught my interest, when I watched this video from one of my favorite You Tube creators about the building of the Xi’an soccer stadium. The architects of the stadium used UE to pre-visualize how the seating sight lines would work, how the roof would be constructed, and other design aspects of the stadium. It is still under construction. We are building a more modest soccer stadium here in St. Louis, so I have a bit of stadium envy here.
The company is Epic Games, most notably known for its Fortnite brand. Perhaps you have played it, or your kids have played it. Fortnite is built using the Unreal Engine, which has been around for decades and is now on its fifth version. Epic was smart with UE in getting it established as the premier 3D visualization tool, and it is used in all sorts of business applications. One of them caught my interest, when I watched this video from one of my favorite You Tube creators about the building of the Xi’an soccer stadium. The architects of the stadium used UE to pre-visualize how the seating sight lines would work, how the roof would be constructed, and other design aspects of the stadium. It is still under construction. We are building a more modest soccer stadium here in St. Louis, so I have a bit of stadium envy here.
Anyway, Epic was smart with spinning out UE from Fortnite. First, it is free to download and get started. Yes, there are license fees if you want to do more with it, but you can figure it out and use most of its features without spending any money. Second, there is a huge dev community to support your efforts: discussion forums, loads of documentation, and professional education options too. UE is being taught in numerous colleges across the world. For example, there is this entire online curriculum. These efforts have paid off, and now there are numerous games that independent developers have built in UE.
Before I get to that, here is a short diversion into the world of film pre-viz. When I was living in LA back in the early aughts, I got to meet Dan Gregoire of Halon Entertainment. Halon is one of the pre-eminent pre-viz shops in the entertainment space, and has worked on numerous blockbuster movies. The concept is similar to what the architects are doing: if you can represent what will be shown on screen digitally, you can help a director figure out what camera and lighting and actors are going to be filmed and save a lot of time and money. I asked Dan about UE and turns out he has been using this tool for more than five years, first adopting it for his work for War for the Planet of the Apes. “It is the core foundation of our pre-viz pipeline,” he told me. “We use it for all sorts of things, including as a virtual art department, LED stage content and final pixel game cinematics.” Coincidentally, today they are part of a conference being held in Burbank featuring experts from Nvidia, UE and Microsoft.
But let’s turn back to this field of architectural technology. As architects have gotten comfortable with digital tools, things like doing pre-viz for the Xi’an stadium make a lot of sense. If you can create a digital copy of your building and experiment with various changes before you pour the first foundation footing, you can save a lot of money and build a better building too.
”In the past, architects had to put huge financial resources aside to hire experts who specialize in using visualization tools,” writes this one blog. “The Unreal Engine removes all this from the equation. It is an easy-to-use tool with medium hardware requirements and supports real-time rendering and experimental visualization.” In effect, UE has made rendering more of a commodity to designers and made pre-viz more approachable even for smaller design studios. Epic has this website that will provide all sorts of case studies and links to resources. There is the Atlantic Technological University in Dublin, which actually offers a three-year BS degree in this area. That is impressive.
It is ironic in a way. Just as our construction industry supply chains are getting choked, digital technology can help cut down on mistakes and help build better buildings. “Real-time technology is the future,” says Dan. “All it took was for the technology to be accessible from a business model perspective, and having Epic license it for free for non-game content was a big step.”
Avast blog: The importance of patching
I’ve often made recommendations about patching your systems. Patching is a simple concept to explain: Keeping all your various digital components (hardware, software, and networking infrastructure) up to date with the most recent versions. However, it can be easier said than done – this is due to the fact that our day-to-day operations have become complex systems that interconnect and intersect in ways that are hard to predict. In this blog post for Avast, I review some of the benefits of timely patching, how to get a patching program established and operational, and some notable failures about patching over the years.