There are two things you need to know about me, if you haven’t already caught on reading my screeds all this time:
- I am very concerned about my infosec, to the point where I continuously evaluate new ways to protect myself. This means I go down a lot of rabbit holes and kiss a lot of frogs. Or whatever trite phrase you’d like.
- I am extremely cheap when it comes to adding monthly subscriptions to do the above. Thus, I tend to be more interested in the free tiers, and carefully weigh the pros and cons of bumping up to something more expensive.
So let’s talk about the basket of services that include a password manager, an encrypted email provider, and an email alias provider. Before a few weeks ago, this looked like the following:
Zoho Vault – This is entirely free, and is an excellent password manager, works across desktops, mobiles and browsers. For some reason, this app isn’t on many people’s radar, which is a shame because I like the other Zoho apps too and think they are a standup company. I switched over to Zoho after getting tired dealing with all the Lastpass breaches. Importing (from Lastpass) and exporting my password collection is simple, with one caveat that I will get to in a moment.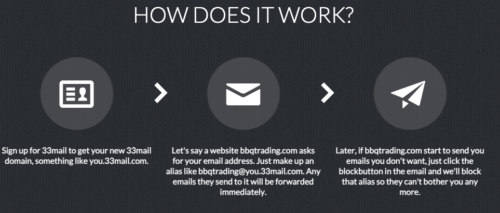
33mail.com – for mail aliases. I have the free Lite version, which has a 10MB bandwidth limits on how much email they will forward to you. I have hit that a few times, and their cheapest paid pricing tier is $1/month. It is easy to create an alias (you just type it into the website’s subscription form that you want to use) and your emails now come filtered through their service. Why would you want to use this service? If you don’t like giving out your “real” email address, this adds an extra layer of control and you can quickly turn off the flood of messages.
ProtonVPN. I have been using the free version with a few minor issues, mostly when I travel or take up residency in some coffee shop. Unlike Brian Chen, I don’t want to build my own VPN (I just don’t trust myself). Speaking of VPNs, I wrote a piece for SiliconANGLE which takes a look back at the history of VPNs, and how they have changed roles, ironically thanks to the pandemic and the way we now work most remotely. .
ProtonVPN just came out with a new pricing scheme and a new password manager app, and so in the interests of the First Directive, I wanted to try them out. Thanks to my friendly PR person, who gave me a press upgrade to their unlimited plan. This is $10/month if you buy a year-long package. This includes several of their services, including encrypted email and their password manager. The VPN on its own is $6/month.
My tl;dr is that the Proton password manager is still too early to rely on, and I am back to using Zoho Vault in production. My reasons:
- Importing my password collection from Zoho to Proton was a nightmare that took a series of false starts and several emails to resolve my issues. Yes, they have some imports that have been put up, but not Zoho’s. I had to create a CSV and use Excel to edit the collection. Yuck.
- It doesn’t have a lot of features, as witnessed by this roadmap of what is to come. Not having a desktop app means if you are trying to enter a password outside of your browser, you will have some effort involved.
I still like Proton as a company: they care about their users’ privacy and security and try to be as transparent as possible, as that roadmap post shows.
Department of Self-promotions
Speaking of SiliconANGLE, I wrote a bunch of stories this week that you might be interested in reading, including about new Google Workspace security features, Proton’s VPN service, and trends in malvertising.
 The former hacker known as Mudge is once again on the move. Mudge, the alias for Peiter Zatko (pictured, center), was the former head of security back when X Corp. was known as Twitter. He is now a consultant for the U.S. Cybersecurity and Infrastructure Security Agency, the Washington Post
The former hacker known as Mudge is once again on the move. Mudge, the alias for Peiter Zatko (pictured, center), was the former head of security back when X Corp. was known as Twitter. He is now a consultant for the U.S. Cybersecurity and Infrastructure Security Agency, the Washington Post