 The former hacker known as Mudge is once again on the move. Mudge, the alias for Peiter Zatko (pictured, center), was the former head of security back when X Corp. was known as Twitter. He is now a consultant for the U.S. Cybersecurity and Infrastructure Security Agency, the Washington Post reported yesterday. My story for SiliconANGLE here.
The former hacker known as Mudge is once again on the move. Mudge, the alias for Peiter Zatko (pictured, center), was the former head of security back when X Corp. was known as Twitter. He is now a consultant for the U.S. Cybersecurity and Infrastructure Security Agency, the Washington Post reported yesterday. My story for SiliconANGLE here.
SiliconANGLE: The summer of adversarial chatbots
This has been the summer of adversarial chatbots.
Researchers from SlashNext Inc. and Netenrich discovered two such efforts, named WormGPT and FraudGPT. These cyberattack weapons are certainly just the beginning in a long line of products that will be developed for nefarious purposes such as creating very targeted phishing emails and new hacking tools. This summer demonstrated that generative artificial intelligence is quickly moving into both offensive and defensive positions, with many security providers calling out how they are using AI methods to augment their defensive tools. The AI security arms race has begun.
You can read my post in SiliconANGLE here.
SiliconANGLE: How Kremlin-backed social media campaigns continue to spread disinformation
A new report sponsored by the European Commission has found that social media has played a key role in the spread of Russian-backed disinformation campaigns since their war with Ukraine began.
“Over the course of 2022, the audience and reach of Kremlin-aligned social media accounts increased substantially all over Europe,” the researchers stated in the report, “Digital Services Act: Application of the Risk Management Framework to Russian disinformation campaigns.”
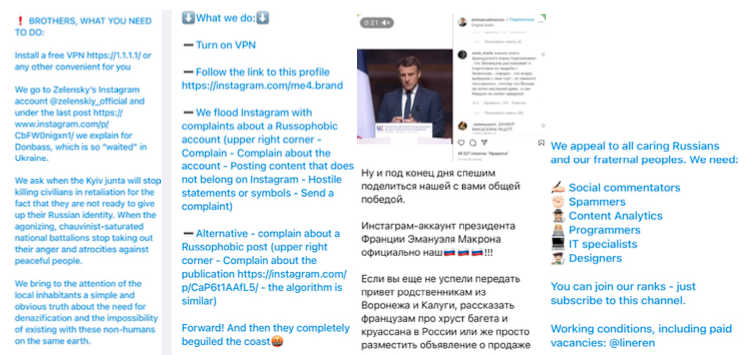
Here you can see various recruitment lures to join Russia’s cyber army who call themselves “Cyber Front Z” and are looking for help on Telegram to post content across networks, up- and down-vote posts, and hound opponents with derogatory comments. The photo shown in the screenshot above is one such target, a pro-Ukraine politician.
The work was done by the nonprofit group Reset and published last week. The group examined these campaigns across 10 languages and over a year. It can serve as useful guidance for U.S. regulators and for how businesses should moderate their own social media content. You can read my analysis for SiliconANGLE here.
NYC subway adventures in zero-factor authentication
Most of you know by now the meaning and importance of MFA, having multiple pathways to authenticate yourself for your various logins. But here is a story that is somewhat chilling: thanks to the NYC subway authority MTA, someone who knows your credit card number could track your movements about the system, thanks to their implementation of zero factor authentication.
Before Joe Cox, the business journalist who now writes for 404media (I know, miserable branding IMHO), wrote a story about this, you could bring up a page on the MTA’s website, enter the card number and you could see a week’s history of the station entry and exit times for each station you swiped your contactless fare card (or Apple or G payments on your phone). Well, you used to be able to do this, until Cox’s story ran exposing this vulnerability. Then the MTA wisely took this down a day after the story ran, saying they were evaluating the “feature.” Well, it is a feature for your estranged spouse (or someone who is looking to do you harm) to track your movements and establish a pattern of life. For the vast majority of us, it is a major-league problem and privacy disaster. Credit card numbers are remarkably easy to obtain.
Now, I call this somewhat ironically zero factor authentication, although sadly many security vendors are now using this term to refer to ways to authenticate your account without using passwords, which technically it is. But There Is No Authentication Involved Here Folks.
Contactless cards — and the phone-based payment apps — are a big convenience. You don’t have to touch any public turnstiles or fumble with putting your card inside those pesky slot readers upside down and backwards. But the MTA went overboard and for some reason was completely brain-dead when they turned this “feature” on.
SiliconANGLE: News of the week
- Microsoft revokes the certificates that were once VeriSign’s, now owned by DigiCert. Lots of confusion ensues.
- Lazarus Group strikes again, this time leveraging open source frameworks and more lethal tools. This criminal group — an arm of the North Korean government — has been active for years spreading all sorts of trouble via ransomware and other attacks.
- Pam Baker’s new book, ChatGPT for Dummies, is useful in a variety of situations, even if you think you already know a lot about the service and AI.
- The life and hard times of phishing-as-a-service malware groups, how they ply their criminal trade and how they work.
SIliconANGLE: Meta’s Facebook finally supports end-to-end message encryption
The importance of end-to-end encryption of digital messages is getting new attention with the announcement that Meta Platforms Inc.’s Facebook will partly add the feature to its Messenger product now, and eventually for all use cases such as group chats by year-end.
It’s an important step, since E2EE, as it’s known for short, is a critical method of providing secure communication that keeps outside parties from accessing data while it’s transferred between systems or devices. But the announcement isn’t the whole story, either, because Facebook is playing catch-up with many of its competitors, such as Signal and Telegram, which have offered E2EE messaging products for years now.
SiliconANGLE: How the new breed of business VPNs will keep them relevant in security
Since virtual private networks were invented nearly 30 years ago as a way to extend a corporate network across the work, they’ve gone through a complete role reversal, even as they’ve continued to evolve to help protect business users’ data and communications. Today’s VPN is now the linchpin for a series of edge business security technologies, taking center stage thanks to a few trends: the popularity of hybrid working conditions brought on by the COVID pandemic, the movement to the cloud away from on-premises servers, and the acceptance of software-as-a-service tools that made it easier to deploy and manage these clouds.
Evaluating password managers, again
There are two things you need to know about me, if you haven’t already caught on reading my screeds all this time:
- I am very concerned about my infosec, to the point where I continuously evaluate new ways to protect myself. This means I go down a lot of rabbit holes and kiss a lot of frogs. Or whatever trite phrase you’d like.
- I am extremely cheap when it comes to adding monthly subscriptions to do the above. Thus, I tend to be more interested in the free tiers, and carefully weigh the pros and cons of bumping up to something more expensive.
So let’s talk about the basket of services that include a password manager, an encrypted email provider, and an email alias provider. Before a few weeks ago, this looked like the following:
Zoho Vault – This is entirely free, and is an excellent password manager, works across desktops, mobiles and browsers. For some reason, this app isn’t on many people’s radar, which is a shame because I like the other Zoho apps too and think they are a standup company. I switched over to Zoho after getting tired dealing with all the Lastpass breaches. Importing (from Lastpass) and exporting my password collection is simple, with one caveat that I will get to in a moment.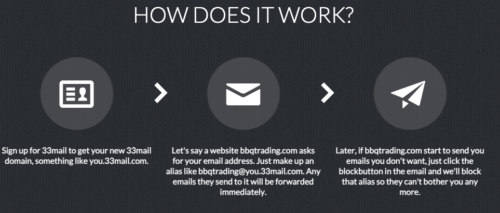
33mail.com – for mail aliases. I have the free Lite version, which has a 10MB bandwidth limits on how much email they will forward to you. I have hit that a few times, and their cheapest paid pricing tier is $1/month. It is easy to create an alias (you just type it into the website’s subscription form that you want to use) and your emails now come filtered through their service. Why would you want to use this service? If you don’t like giving out your “real” email address, this adds an extra layer of control and you can quickly turn off the flood of messages.
ProtonVPN. I have been using the free version with a few minor issues, mostly when I travel or take up residency in some coffee shop. Unlike Brian Chen, I don’t want to build my own VPN (I just don’t trust myself). Speaking of VPNs, I wrote a piece for SiliconANGLE which takes a look back at the history of VPNs, and how they have changed roles, ironically thanks to the pandemic and the way we now work most remotely. .
ProtonVPN just came out with a new pricing scheme and a new password manager app, and so in the interests of the First Directive, I wanted to try them out. Thanks to my friendly PR person, who gave me a press upgrade to their unlimited plan. This is $10/month if you buy a year-long package. This includes several of their services, including encrypted email and their password manager. The VPN on its own is $6/month.
My tl;dr is that the Proton password manager is still too early to rely on, and I am back to using Zoho Vault in production. My reasons:
- Importing my password collection from Zoho to Proton was a nightmare that took a series of false starts and several emails to resolve my issues. Yes, they have some imports that have been put up, but not Zoho’s. I had to create a CSV and use Excel to edit the collection. Yuck.
- It doesn’t have a lot of features, as witnessed by this roadmap of what is to come. Not having a desktop app means if you are trying to enter a password outside of your browser, you will have some effort involved.
I still like Proton as a company: they care about their users’ privacy and security and try to be as transparent as possible, as that roadmap post shows.
Department of Self-promotions
Speaking of SiliconANGLE, I wrote a bunch of stories this week that you might be interested in reading, including about new Google Workspace security features, Proton’s VPN service, and trends in malvertising.
SiliconANGLE news of the week
News items that I wrote this week include:
- Google adds new security features to its Workspace. The features cover aspects of implementing zero-trust security, data loss prevention or DLP, and data privacy controls. Many involve a series of automated improvements that will continuously monitor data placed in Google Drive, using its AI engine.
2. Proton adds new business-oriented VPN packaging to its services. The features build upon existing adware blockers, a smart protocol called Stealth that automatically chooses the best-performing connection, and support for both WireGuard and OpenVPN protocols.
3. Malvertising trends: The malware exploits known as malware-infected ads, or malvertising, have been around for decades, but new reports point to a steady rise in lethality. The technique continues to be profitable, because the malware ads are masquerading as normal ads in the ad networks and using the network as a distribution and funds collection system.:
Book review: Containing Big Tech by Tom Kemp
 Tom Kemp’s new book about the dangers of the five Big Tech companies is several books in one volume. Normally, this would not be a great recommendation, but stick with me here and see if you agree that he has written a very useful, effective, and interesting book.
Tom Kemp’s new book about the dangers of the five Big Tech companies is several books in one volume. Normally, this would not be a great recommendation, but stick with me here and see if you agree that he has written a very useful, effective, and interesting book.
It is a detailed history on how Microsoft, Google, Meta/Facebook, Amazon and Apple have become the tech powerhouses and near-monopolists with their stranglehold on digital services, at the same time threatening our privacy. It is a reference work for consumers who are concerned about what private information is shared by these vendors, and how to take back control over their data. It is also an operating manual for business IT managers and executives who are looking to comply with privacy regs and also to prevent their own sensitive data from leaking online. And it is a legislative to-do list for how to fashion better data and privacy protection for our digital future.
Kemp focuses on eight different areas of interest, one per chapter. For example, one chapter describes some startling failures at reigning in the data broker industry and another goes into details about how easily disinformation has prevailed and thrived in the past decade. He mixes his own experience as a tech entrepreneur, investor and executive with very practical matters. Each chapter has a section dealing with the issue, then the response of the various tech vendors, and finally a collection of various laws and proposals from both the EU and the US in response. This last section is a sad tale about the lack of legislative forward motion in the US and how the EU has forged ahead with their own laws in this area — only to be lightly enforced.
Speaking of legislation, I asked him what he thought about the lack of any progress in that department, especially at the US federal level. He told me in a recent interview that “No one is going to do anything to modify Section 230 — all previous efforts have been roundly beaten. Eventually, pressure is going to shift to EU, with its new laws that take effect in 2024. These will require online businesses to monitor their platforms for objectionable speech. These will also give end users the ability to flag content and make the tech vendors to be more transparent. Tech platforms will then have to finally respond. I don’t see anything happening in the US, nor with any new federal privacy laws enacted.”
His unique know-how and the combination of these different perspectives makes for a fascinating read. For example, to test Google’s claims that they have cleaned up their heavy-handed location monitoring, he did some role playing and set up appointments at local abortion clinics, visited drug stores, and shopped online. His online activity and location data was monitored by Google about every six minutes. “The real-time nature of this monitoring was impressive. Google knows the ads that they served me, the pages I visited, my Android phone notifications and locations. And despite their promises, they were logging all these details about me,” he said.
Even if you have been parsimonious about protecting your privacy, you probably don’t know that Meta’s tracking Pixel is used by a third of the world’s most popular websites and is at the heart of numerous privacy lawsuits, especially in Europe. Or the sequence of steps to tamp down on what the five tech vendors allow you to make your activities more private.
Kemp doesn’t pull any punches — he lays blame at the keyboards of these Big Tech vendors and our state and federal legislators. “Big Tech’s anticompetitive practices have also significantly contributed to them becoming these giants who act as gatekeepers to our digital economy,” he writes. “The five Big Tech firms have five of the seven largest cash balances of any S&P 500 company in 2022.”
He documents the missteps that the major tech vendors have taken, all in the service of their almighty algorithms and with the aim of increasing engagement, no matter the costs to society, or to its most at-risk members — namely children.
I asked him about the latest crop of studies that were paid for in part by Meta/Facebook and appeared in various technical journals (and covered here in the NY Times.) He told me, “Meta was closely involved in shaping this research and in setting the agenda. It wasn’t a neutral body – they framed the context and provided the data. Part of the problem is that the big tech platforms are talking out of both sides of their mouths. They market their platforms specifically to influence people to buy products from their advertisers. But then their public policy staffs have another message that says they don’t really influence people when bad things happen to them. They certainly haven’t helped the situation via algorithmic amplification of using their services.” I reminded him that many of the big tech trust and safety teams were one of the first groups to be fired when the most recent downturn happened.
So get a copy of this book now, both for yourself and your business. If you want to stay abreast of the issues he mentions, check out his website for post-publication updates, which is very helpful.
You may have taken some of the privacy-enhancing steps he outlines in one of the book’s appendices, but probably will learn some new tricks to hide your identity.