One of my readers asked me how to go about removing Facebook completely from their online lives. After I pulled together the various links that you’ll see below, I thought I would share with you all. Now, I am not saying that I am contemplating doing this: sadly, my online professional life requires that I continue to be a part of Facebook, whether I like it or not. But that doesn’t mean I have to agree with its corporate policies, as I have made clear in several posts earlier this summer. But read on or save this column somewhere, just in case you are thinking about de-Facing your life. And be prepared to spend a few hours going through the numerous steps.
 Your first to-do is to download all of your data that Facebook has on you. I wrote about this process earlier (and covered the other social networks too) in this post. But if you just want the Facebook archive download, go to this page. You might have to wait a few days until your archive is ready: don’t worry, you will be notified.
Your first to-do is to download all of your data that Facebook has on you. I wrote about this process earlier (and covered the other social networks too) in this post. But if you just want the Facebook archive download, go to this page. You might have to wait a few days until your archive is ready: don’t worry, you will be notified.
Next, decide whether you want a trial separation or a total divorce. Facebook refers to the former as deactivating your account. This keeps your data in their grubby digital hands, but at least you will disappear from your friends’ social networks. You can change your mind in the future and re-activate your account just by logging back into your account, so if you are somewhat serious about this but don’t want to inadvertently login, make sure you delete the login details from your password manager or any saved websites on your various browsers and computers.
If you still want to stick with Facebook, you might just want to cleanse your privacy settings. This post goes into detail about how to do this. You can see how complex setting up your privacy has gotten, when you need a full page of instructions to naviagate the various options.
Before you opt for the total divorce, take a look at the connected apps that you once allowed access to your Facebook account. You might not have remembered doing this, and in another column I spoke about what you should do for a social media “spring cleaning” for the other networks and for your various privacy settings. You should spend some time doing this app audit for the other networks as well.
Why do you want to deal with your connected apps before total account deletion? Because you might want to still access one or more of these apps, and if you delete your Facebook presence, your access goes away if that particular app depends on that. For example, a web portal that my doctors use to communicate with me could depend on my Facebook login. (It doesn’t, but that is because I decided to use another login mechanism other than Facebook.) By going to the connected apps page, you can see the complete list of whom you have authorized.
Still with me? I realize that it seems as if the scope of this project continues to widen, but that is to be expected. Let’s continue.
Mashable has this nice article that will walk you through the steps of both deactivation and a complete deletion process. I won’t repeat the numerous steps here, but you should take the time to review their post.
If you opt for deletion, remember you have to cleanse your entire computing portfolio of everything Facebook: this means all your browsers, your mobile devices, and your mobile messenger apps too. I don’t particularly like the mobile messenger app, as one friend described it accurately as a “rabid dog” that just grabs your contacts and other data. Indeed, if you have examined your downloaded archive you can see that for yourself.
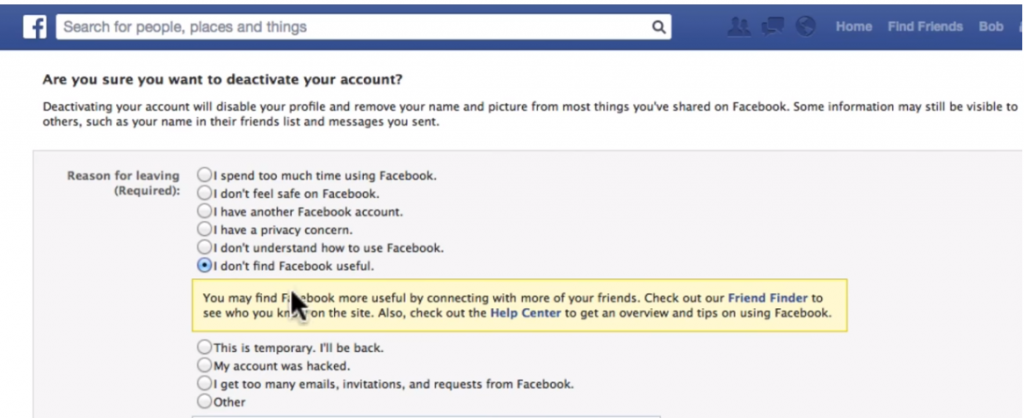 Now for the final step, the actual deletion. The Mashable piece has a long list of what you have to do, aside from hitting the delete button in the Facebook interface. If you want a more visual aid, check out this screencast that shows you these first steps.
Now for the final step, the actual deletion. The Mashable piece has a long list of what you have to do, aside from hitting the delete button in the Facebook interface. If you want a more visual aid, check out this screencast that shows you these first steps.
I realize this is a lot of effort, and Facebook has very nicely put in a number of “Are you sure” checks along the path, just in case you aren’t completely ready for the divorce. I would be interested in hearing from you if you do go through the entire process and what your reasons are for doing it.
 So how do you get the audio and video signals from your computer to your living room TV? Two ways: either by connecting your computer directly to your TV with an HDMI cable or using one of several devices like Google’s Chromecast that does this for you wirelessly. If you use the direct cable connection from your computer, you will have to figure out a wireless keyboard and mouse to control it. If you use Chromecast, you will have to figure out the sequence of controls using the three apps that Google has (Google’s Chrome browser, Google Home and the Chromecast app itself) to get it setup. The workflow isn’t immediately obvious, and I suggest you learn the process before bringing your spouse into the room for the demo.
So how do you get the audio and video signals from your computer to your living room TV? Two ways: either by connecting your computer directly to your TV with an HDMI cable or using one of several devices like Google’s Chromecast that does this for you wirelessly. If you use the direct cable connection from your computer, you will have to figure out a wireless keyboard and mouse to control it. If you use Chromecast, you will have to figure out the sequence of controls using the three apps that Google has (Google’s Chrome browser, Google Home and the Chromecast app itself) to get it setup. The workflow isn’t immediately obvious, and I suggest you learn the process before bringing your spouse into the room for the demo.
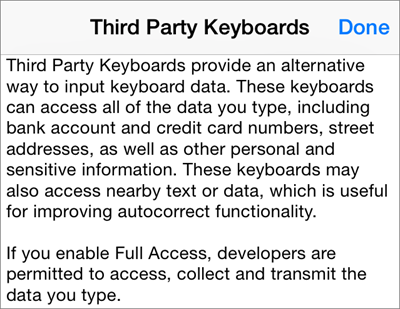 Here is the thing. In order to install one of these keyboard apps, you have to grant it access to your phone. This seems like common sense, but sadly, this also grants the app access to pretty much everything you type, every piece of data on your phone, and every contact of yours too. Apple calls this full access, and they require these keyboards to ask explicitly for this permission after they are installed and before you use them for the first time. Many of us don’t read the fine print and just click yes and go about our merry way.
Here is the thing. In order to install one of these keyboard apps, you have to grant it access to your phone. This seems like common sense, but sadly, this also grants the app access to pretty much everything you type, every piece of data on your phone, and every contact of yours too. Apple calls this full access, and they require these keyboards to ask explicitly for this permission after they are installed and before you use them for the first time. Many of us don’t read the fine print and just click yes and go about our merry way.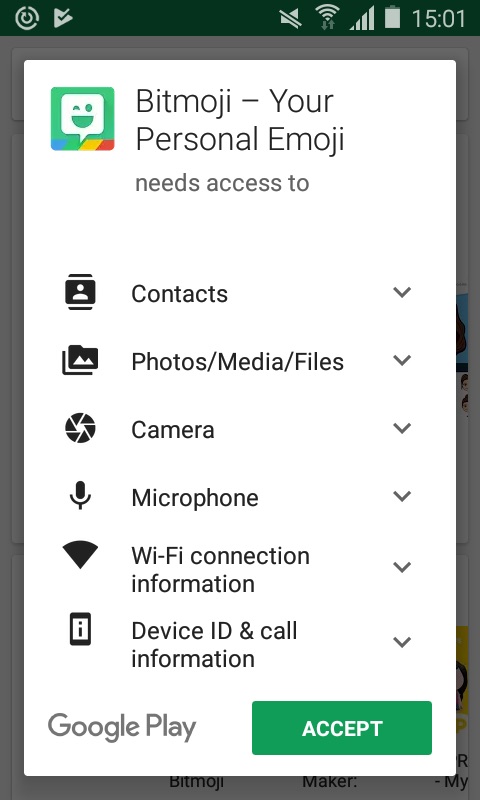 On Android phones, the permissions are a bit more granular, as you can see in this screenshot. This is actually just half of the overall permissions that are required.
On Android phones, the permissions are a bit more granular, as you can see in this screenshot. This is actually just half of the overall permissions that are required.