I have been spending time studying up on what actually happened at Sony over the past month. There has been a tremendous amount of inaccurate reporting, and a dearth of factual information. Let’s try to set that record a bit straighter. From where I sit, the attack and the activity about the movie were two separate events and were probably caused by at least two separate entities. Assigning blame across both of them to the same actor is ludicrous. (And Dr. Evil has a few funny things to say about the whole situation too.)
First, the sad irony of a company that deliberately injects malware into their products being hacked yet again. While many, including President Obama, were quick to assign blame to the North Koreans, the actual initial breech appears to be the work of a Sony insider who could guide the hackers toward specific servers and IP addresses.Certainly, this level of detail could have sussed out with lots of clever hacking, but the simple explanation is a dissatisfied former employe, of which there are many.
Second, the sad irony of the press becoming so enthralled with the sordid details of the leaked content that they so forgot their actual duty in telling the story of what happened. They share the blame with the hackers, who knew exactly how to manipulate them and feed our hunger for celebrity gossip.
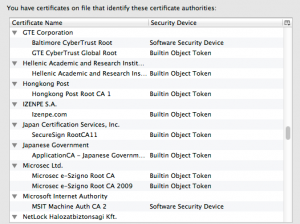
The third irony is that Sony’s security should have been better: this isn’t their first rodeo and certainly now wont be their last. Storing passwords as plain text, using the word “password” or other commonly guessed words, and having no mechanism to monitor the exfiltrated data were all shameful practices. What is doubly wrong is that they have had numerous opportunities to improve their IT procedures, and haven’t.
Ironic that their passwords were so poor that a security researcher was able to inject a fake Sony SSL certificate by guessing one of them. Thankfully, this wasn’t a deliberate hack, just a demonstration of how easy Sony’s procedures could be circumvented.
Ironic too are all the calls for posting the movie on various online streaming services to counter the cancelled Christmas Day release. So the way to combat censorship, even self-imposed, is to take your content to the cloud, so that more people can see your movie. Wasn’t this was many private citizens were asking the MPAA to let them do when they posted movies online?
Also ironic are stories about how the MPAA and Sony were using denial of service methods to try to keep people from seeing their movies, including The Interview. See irony #1 about injecting malware, etc. And how ironic was it that the peer file sharing services actually working in cooperation with the movie studios to take down the leaked content, including some copies of pre-released movies, quickly once the hackers uploaded them?
Also ironic how one of the first things that our government is asking for a joint effort with the Chinese to cooperate in controlling this hack: perhaps the same unit within the Chinese government that we recently indicted for cyber espionage could be used? Granted there is a line between espionage and criminal hacking, or at least there used to be one.
Finally, while not ironic it is sad that the film’s creators so insisted on using the actual name of a living president in their film. While not the first time this has happened, they could have scored their satire points by going the Chaplin/Great Dictator route which doesn’t actually name Hitler but in every other way goes about pillorying him. Certainly, you can’t blame the North Koreans on this point: had someone used a similar plot line with our president, chances are even our bumbling Secret Service would have been all over that one too.
If you want to read a very solid collection of the various events of the past month, the folks at Risk Based Security (a Virginia security VAR) are worth your time and clicks. They continue to add to their coverage as new events unfold.
So what are some action items you can take? Here are a few:
- Understand that all it takes is an unhappy employee with a thumb drive and basic file copying skills. You should think about your HR and data leak prevention policies accordingly.
- Get thy passwords in order, puh-leeze. This isn’t something that will cost megabucks.
- It is way past time to encrypt your email, especially if you communicate with global brands And even if you don’t, still more the reason.
And to wrap up, I want to quote S. Cobb’s blog where he says:
“Rather than berate those who are being realistic about our current weaknesses, let’s put our anger and our energy into demanding companies and governments do a better job of securing our digital assets and defending the digital world.”
![]() Mobile banking has the opportunity to become just as disruptive in the modern era as ATMs were back in the 1970s. From the convenience of our own homes, and with our own devices, we now have the opportunity to do just about everything except get cash from our bank.
Mobile banking has the opportunity to become just as disruptive in the modern era as ATMs were back in the 1970s. From the convenience of our own homes, and with our own devices, we now have the opportunity to do just about everything except get cash from our bank.
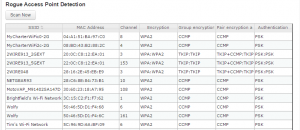 Overall, the market has slowly evolved more than had any big revolutionary changes. Products are getting better in terms of features and price/performance. All six of these units will do fine for securing small offices of 25 people.
Overall, the market has slowly evolved more than had any big revolutionary changes. Products are getting better in terms of features and price/performance. All six of these units will do fine for securing small offices of 25 people.